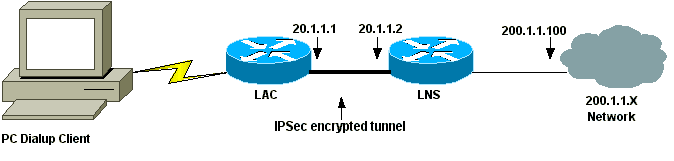
A User Datagram Protocol (UDP) port is used for L2TP communication. Because it does not provide any security for data such as encryption and confidentiality, an encryption protocol such as Internet Protocol security (IPsec) is often used with L2TP.
This term is also known as Virtual Dialup Protocol.
Officially published in 1999, L2TP is an extension of Point-to-Point Tunneling Protocol (PPTP). It is the merger of two protocols, one from Microsoft (PPTP) and one from Cisco. L2TP saves the dial-up cost and overhead for any user willing to remotely connect with a site office. L2TP is known as Virtual Dialup Protocol because of its service of the Point-to-Point Protocol (PPP) extension over Internet.
For example, suppose that a user in New York is connected with a traditional dial-up modem and is looking to communicate with someone in Sydney. For this purpose, the user gets a connection and establishes a dedicated link from New York to Sydney. This dedicated dial-up link will use a public switched telephone network (PSTN) and provide the lowest data transfer speed because of shared PSTN media. Thousands of other users are using the same medium, so the user will have an overall speed of 33 Kbps or worse.
Instead, the user could use L2TP where PPP is used and configured at both ends (the ISP and the user site). Following the successful authentication of a user request, a tunnel is created for user data. When the tunnel is created, the user is open to start communication.
Advantages of L2TP include:
For example, suppose that a user in New York is connected with a traditional dial-up modem and is looking to communicate with someone in Sydney. For this purpose, the user gets a connection and establishes a dedicated link from New York to Sydney. This dedicated dial-up link will use a public switched telephone network (PSTN) and provide the lowest data transfer speed because of shared PSTN media. Thousands of other users are using the same medium, so the user will have an overall speed of 33 Kbps or worse.
Instead, the user could use L2TP where PPP is used and configured at both ends (the ISP and the user site). Following the successful authentication of a user request, a tunnel is created for user data. When the tunnel is created, the user is open to start communication.
Advantages of L2TP include:
- High data security is provided for critical applications.
- High-level encryption is used so that critical information is always safe and remains personal.
- It provides excellent and efficient connectivity.
- It is cost-effective and does not have overhead cost after implementation.
- It is reliable, scalable, fast and flexible.
- It is an industry-standard best for the corporate sector.
- It has the best authorization policy for users with VPN authentication.


1 Comments
Layer 2 Tunneling Protocol (L2Tp) >>>>> Download Now
ReplyDelete>>>>> Download Full
Layer 2 Tunneling Protocol (L2Tp) >>>>> Download LINK
>>>>> Download Now
Layer 2 Tunneling Protocol (L2Tp) >>>>> Download Full
>>>>> Download LINK DG