One of the simplest things you can do to prevent malware
from spreading through email in Office 365 is blocking attachment types that
are commonly used to send malware. This includes executables (.exe), scripts
(.vbs), and macro enabled office documents (.docm).
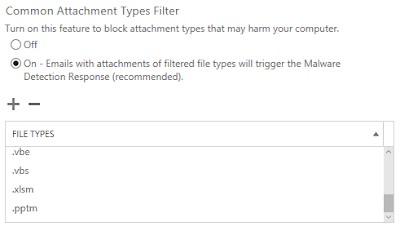
The anti-malware policies in Office 365 have a setting Common Attachment
Types Filter that is off by default. I definitely recommend that you turn
it on.

ace
ani
app
docm
exe
jar
reg
scr
vbe
vbs
Office 365 has an existing list of many other file types
that you can add, but in Exchange admin center, there is no method to add your
own customized file types. For example, xlsm (Excel macros) is not in the list.
You can add your own customized file types by using Windows PowerShell in
Exchange Online.
To add your own customized file types to the malware policy, you can use
the Set-MalwareFilterPolicy cmdlet. The general process is as
follows:
Retrieve the existing list of file types in an array.
Add the new file types to the array.
Set the file types for the malware policy by using the array
$FileTypesAdd = Get-MalwareFilterPolicy
-Identity Default | Select-Object -Expand FileTypes
$FileTypesAdd += "xlsm","pptm"
Set-MalwareFilterPolicy -Identity Default -EnableFileFilter $true -FileTypes $FileTypesAdd
Note that when you run Set-MalwareFilterPolicy, you will probably get an error
indicating that you need to run Enable-OrganizationCustomization. This
creates additional objects in your Exchange Online tenant that allow additional
customizations like this one.

After you have added the file types to the policy, they are visible in Exchange
admin center. You can modify the the list of file types in Exchange admin
center after this point, and it does not accidentally remove the customized
file types you added.
Another way to accomplish this same goal is by using transport rules. Create a
rule to apply if Any attachment's file extension matches. And then Redirect
the message to hosted quarantine. However, this does not give the same options
for notifications as using the malware policy. You could probably build the
same functionality into the rule if you add enough actions, but I think it's
easier to have one central location that controls all of the malware rather
than adding rules.


0 Comments