The past few months from a security perspective have been a roller coaster of zero-day vulnerabilities and critical patches that have been needed to patch serious issues found across a wide range of Microsoft products and solutions. This has notably included Microsoft Exchange Server and others. The latest patch Tuesday from Microsoft contains some 55 security fixes, many of which are critical or high in severity. One I wanted to key in on is a Hyper-V Remote Code execution vulnerability that is a pretty nasty one that IT admins will want to make sure they get patched for business-critical Hyper-V environments. Let’s take a look at Hyper-V critical remote code execution vulnerability in May 2021 patch Tuesday and see what it involves and how to get it patched.
May 2021 Patch Tuesday Security Updates available
There is a wide range of vulnerabilities that affect various Microsoft solutions and products to be aware of. The following is a rundown of the patches and vulnerabilities contained in this Patch Tuesday as documented by Bleeping Computer.
| Tag | CVE ID | CVE Title | Severity |
|---|---|---|---|
| .NET Core & Visual Studio | CVE-2021-31204 | .NET and Visual Studio Elevation of Privilege Vulnerability | Important |
| HTTP.sys | CVE-2021-31166 | HTTP Protocol Stack Remote Code Execution Vulnerability | Critical |
| Internet Explorer | CVE-2021-26419 | Scripting Engine Memory Corruption Vulnerability | Critical |
| Jet Red and Access Connectivity | CVE-2021-28455 | Microsoft Jet Red Database Engine and Access Connectivity Engine Remote Code Execution Vulnerability | Important |
| Microsoft Accessibility Insights for Web | CVE-2021-31936 | Microsoft Accessibility Insights for Web Information Disclosure Vulnerability | Important |
| Microsoft Bluetooth Driver | CVE-2021-31182 | Microsoft Bluetooth Driver Spoofing Vulnerability | Important |
| Microsoft Dynamics Finance & Operations | CVE-2021-28461 | Dynamics Finance and Operations Cross-site Scripting Vulnerability | Important |
| Microsoft Exchange Server | CVE-2021-31195 | Microsoft Exchange Server Remote Code Execution Vulnerability | Important |
| Microsoft Exchange Server | CVE-2021-31209 | Microsoft Exchange Server Spoofing Vulnerability | Important |
| Microsoft Exchange Server | CVE-2021-31207 | Microsoft Exchange Server Security Feature Bypass Vulnerability | Moderate |
| Microsoft Exchange Server | CVE-2021-31198 | Microsoft Exchange Server Remote Code Execution Vulnerability | Important |
| Microsoft Graphics Component | CVE-2021-31170 | Windows Graphics Component Elevation of Privilege Vulnerability | Important |
| Microsoft Graphics Component | CVE-2021-31188 | Windows Graphics Component Elevation of Privilege Vulnerability | Important |
| Microsoft Office | CVE-2021-31176 | Microsoft Office Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2021-31175 | Microsoft Office Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2021-31177 | Microsoft Office Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2021-31179 | Microsoft Office Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2021-31178 | Microsoft Office Information Disclosure Vulnerability | Important |
| Microsoft Office Excel | CVE-2021-31174 | Microsoft Excel Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-28478 | Microsoft SharePoint Spoofing Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-31181 | Microsoft SharePoint Remote Code Execution Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-26418 | Microsoft SharePoint Spoofing Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-28474 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-31171 | Microsoft SharePoint Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-31173 | Microsoft SharePoint Server Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2021-31172 | Microsoft SharePoint Spoofing Vulnerability | Important |
| Microsoft Office Word | CVE-2021-31180 | Microsoft Office Graphics Remote Code Execution Vulnerability | Important |
| Microsoft Windows Codecs Library | CVE-2021-31192 | Windows Media Foundation Core Remote Code Execution Vulnerability | Important |
| Microsoft Windows Codecs Library | CVE-2021-28465 | Web Media Extensions Remote Code Execution Vulnerability | Important |
| Microsoft Windows IrDA | CVE-2021-31184 | Microsoft Windows Infrared Data Association (IrDA) Information Disclosure Vulnerability | Important |
| Open Source Software | CVE-2021-31200 | Common Utilities Remote Code Execution Vulnerability | Important |
| Role: Hyper-V | CVE-2021-28476 | Hyper-V Remote Code Execution Vulnerability | Critical |
| Skype for Business and Microsoft Lync | CVE-2021-26422 | Skype for Business and Lync Remote Code Execution Vulnerability | Important |
| Skype for Business and Microsoft Lync | CVE-2021-26421 | Skype for Business and Lync Spoofing Vulnerability | Important |
| Visual Studio | CVE-2021-27068 | Visual Studio Remote Code Execution Vulnerability | Important |
| Visual Studio Code | CVE-2021-31214 | Visual Studio Code Remote Code Execution Vulnerability | Important |
| Visual Studio Code | CVE-2021-31211 | Visual Studio Code Remote Code Execution Vulnerability | Important |
| Visual Studio Code | CVE-2021-31213 | Visual Studio Code Remote Containers Extension Remote Code Execution Vulnerability | Important |
| Windows Container Isolation FS Filter Driver | CVE-2021-31190 | Windows Container Isolation FS Filter Driver Elevation of Privilege Vulnerability | Important |
| Windows Container Manager Service | CVE-2021-31168 | Windows Container Manager Service Elevation of Privilege Vulnerability | Important |
| Windows Container Manager Service | CVE-2021-31169 | Windows Container Manager Service Elevation of Privilege Vulnerability | Important |
| Windows Container Manager Service | CVE-2021-31208 | Windows Container Manager Service Elevation of Privilege Vulnerability | Important |
| Windows Container Manager Service | CVE-2021-31165 | Windows Container Manager Service Elevation of Privilege Vulnerability | Important |
| Windows Container Manager Service | CVE-2021-31167 | Windows Container Manager Service Elevation of Privilege Vulnerability | Important |
| Windows CSC Service | CVE-2021-28479 | Windows CSC Service Information Disclosure Vulnerability | Important |
| Windows Desktop Bridge | CVE-2021-31185 | Windows Desktop Bridge Denial of Service Vulnerability | Important |
| Windows OLE | CVE-2021-31194 | OLE Automation Remote Code Execution Vulnerability | Critical |
| Windows Projected File System FS Filter | CVE-2021-31191 | Windows Projected File System FS Filter Driver Information Disclosure Vulnerability | Important |
| Windows RDP Client | CVE-2021-31186 | Windows Remote Desktop Protocol (RDP) Information Disclosure Vulnerability | Important |
| Windows SMB | CVE-2021-31205 | Windows SMB Client Security Feature Bypass Vulnerability | Important |
| Windows SSDP Service | CVE-2021-31193 | Windows SSDP Service Elevation of Privilege Vulnerability | Important |
| Windows WalletService | CVE-2021-31187 | Windows WalletService Elevation of Privilege Vulnerability | Important |
| Windows Wireless Networking | CVE-2020-24588 | Windows Wireless Networking Spoofing Vulnerability | Important |
| Windows Wireless Networking | CVE-2020-24587 | Windows Wireless Networking Information Disclosure Vulnerability | Important |
| Windows Wireless Networking | CVE-2020-26144 | Windows Wireless Networking Spoofing Vulnerability | Important |
Hyper-V Critical remote code execution vulnerability CVE-2021-28476
The official Hyper-V remote code execution vulnerability CVE is contained in CVE-2021-28476. The description of the vulnerability is as follows:
“Under what circumstances might this vulnerability be exploited other than as a denial of service attack against a Hyper-V host?
This issue allows a guest VM to force the Hyper-V host’s kernel to read from an arbitrary, potentially invalid address. The contents of the address read would not be returned to the guest VM. In most circumstances, this would result in a denial of service of the Hyper-V host (bugcheck) due to reading an unmapped address. It is possible to read from a memory mapped device register corresponding to a hardware device attached to the Hyper-V host which may trigger additional, hardware device specific side effects that could compromise the Hyper-V host’s security.”
Installing Security Updates with PowerShell
I really like the PSWindowsUpdate PowerShell module for installing Windows Updates. It provides a lot of great parameters to key in on specific updates and control the behavior during the install. To use the PSWindowsUpdate PowerShell module, you can use the following to install the module:
Get-PackageProvider -name nuget -force
Install-Module PSWindowsUpdate -confirm:$false -forceAfter installing the module, you can search for and install all security updates using the following:
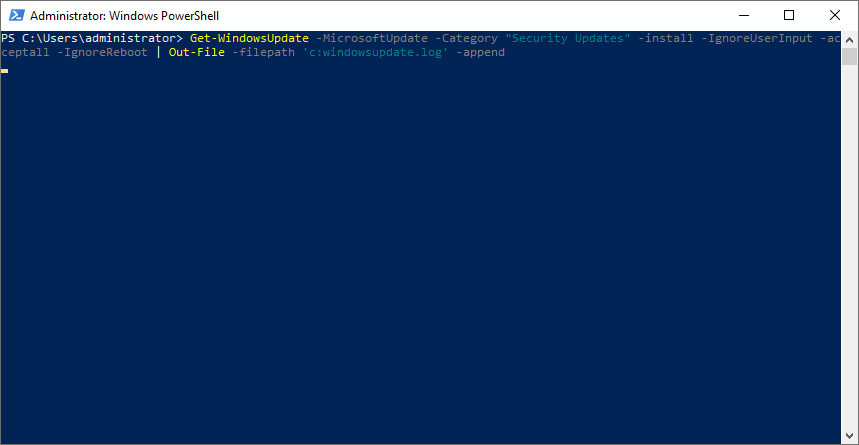
Get-WindowsUpdate -MicrosoftUpdate -Category "Security Updates" -install -IgnoreUserInput -acceptall -IgnoreReboot | Out-File -filepath 'c:windowsupdate.log' -appendPatching your Hyper-V servers from this critical security vulnerability is something you will want to schedule as soon as possible. Even thought it isn’t at this point being exploited in the wild, there is a good chance it will be very soon.

0 Comments