Microsoft’s latest server release, Windows Server 2022, represents the latest and greatest security features available to organizations today. It provides a new feature called Secured Core Server that provides a “one-stop” shop to enabling all of the recommended core security features in the Windows Server operating system. This is all exposed by the new Windows Admin Center. One of the great features of the latest version of VMware vSphere and VMware Workstation is the ability to use virtual TPMs which is one of the requirements of Secured Core Server. However, there are still a few things to think about with virtual implementations of Windows Server 2022. Let’s take a look at Windows Server 2022 Secured Core virtual TPM and get a better overview of the technologies at play.
What is Secured Core Server?
Windows Server 2022 Secured Core Server is based on the following six security technologies enabled and working on your Windows Server 2022 server:
- HVCI
- Boot DMA Protection
- System Guard
- Secure Boot
- Virtualization-based Security (VBS)
- TPM 2.0
Let’s take a look at these individually and see how these security features help to secure Windows Server 2022.
HVCI
HVCI stands for Hypervisor Enforced Code Integrity. It is a technology used in conjunction with Virtualization-based security (VBS). One of the vulnerable areas of any Windows Server is the boot, system, and driver files. With HVCI, it monitors the validity and integrity of the security technologies built into Windows Server 2022, such as Control Flow Guard, Credential Guard, or tampering with security certificates.
Boot DMA Protection
Drive-by attacks on direct-memory access (DMA) is a way attackers can compromise systems. These types of attacks can be perpetrated by hotplug PCI devices or internal PCIe devices. The Boot DMA Protection helps to prevent malware injection and the bypassing of security controls. It can also guard against malicious code starting and initiating DMA.
System Guard
System Guard is a Windows Defender component and helps to protect the integrity of the Windows system. Attackers can potentially tamper with Windows system files to compromise a system on boot or at other low levels. System Guard helps to protect against any tampering with Windows system files and does this using local and remote attestation to verify system integrity.
You can think of it as a fingerprint. If the fingerprint changes or no longer matches, System Guard knows there has been tampering. This capability helps to protect against malicious firmware or software from instantiating before the boot loader. As a real-world example, this helps to catch possible supply chain attacks that may infect a firmware release, driver, or other critical software.
Secure Boot
Secure boot makes sure system firmware is validated and is indeed
the firmware released by the OEM vendor. It works off of boot
signatures and UEFI firmware drivers to validate and make sure all of
the necessary software is authorized to execute and is doing what it is
supposed to do. Again, this helps with any boot tampering or malicious
code injection into a Windows Server by an attacker.
Virtualization-based Security (VBS)
Virtualization-based security uses a hypervisor, in this case Hyper-V, to create a protected space where security information is stored out of the reach of privileged system processes. The OS can access the special area of memory, but in a limited way. These safety precautions help to make it much more difficult for an attacker to steal security information from memory such as credential hashes and other sensitive data. As mentioned earlier, HVCI uses the capabilities provided by Virtualization-based security to carry out its tasks and security validation.
TPM 2.0
The Trusted Platform Module is a passive device that carries out security-related operations. You can think of it as a crypto-processor that has the ability to generate, store, and process cryptographic keys for security-related tasks. These tasks include attestation and security verification to quickly identify and stop malicious code.
Viewing and configuring Secured-Core in Windows Server 2022
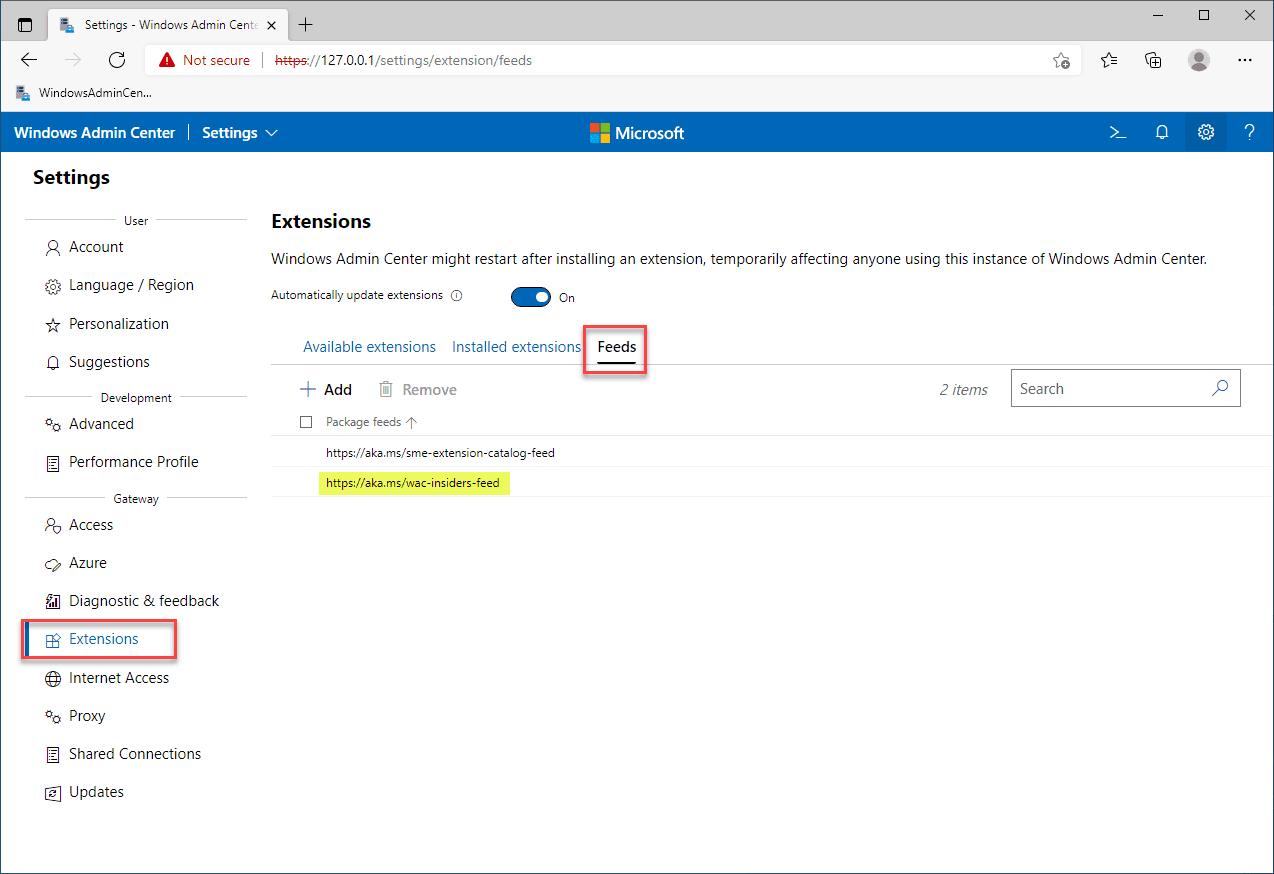
As mentioned at the outset, Windows Admin Center (WAC) is used to view and configure the Secured-Core settings in Windows Server 2022. In Windows Admin Center, to view the Secured-Core functionality in Windows Server 2022, you need to enable the insider’s feed in the extensions Feeds.
Note below. Click Extensions > Feeds > Add. Then add the URL:
Once you enable the Insider’s Feed in Windows Admin Center, you will see the higher version of the Security extension. At the time of this writing, the non-Insider version is 0.9.4 and the Insiders version is 0.23.0. The 0.23.0 version is what I have installed in the screenshot below.
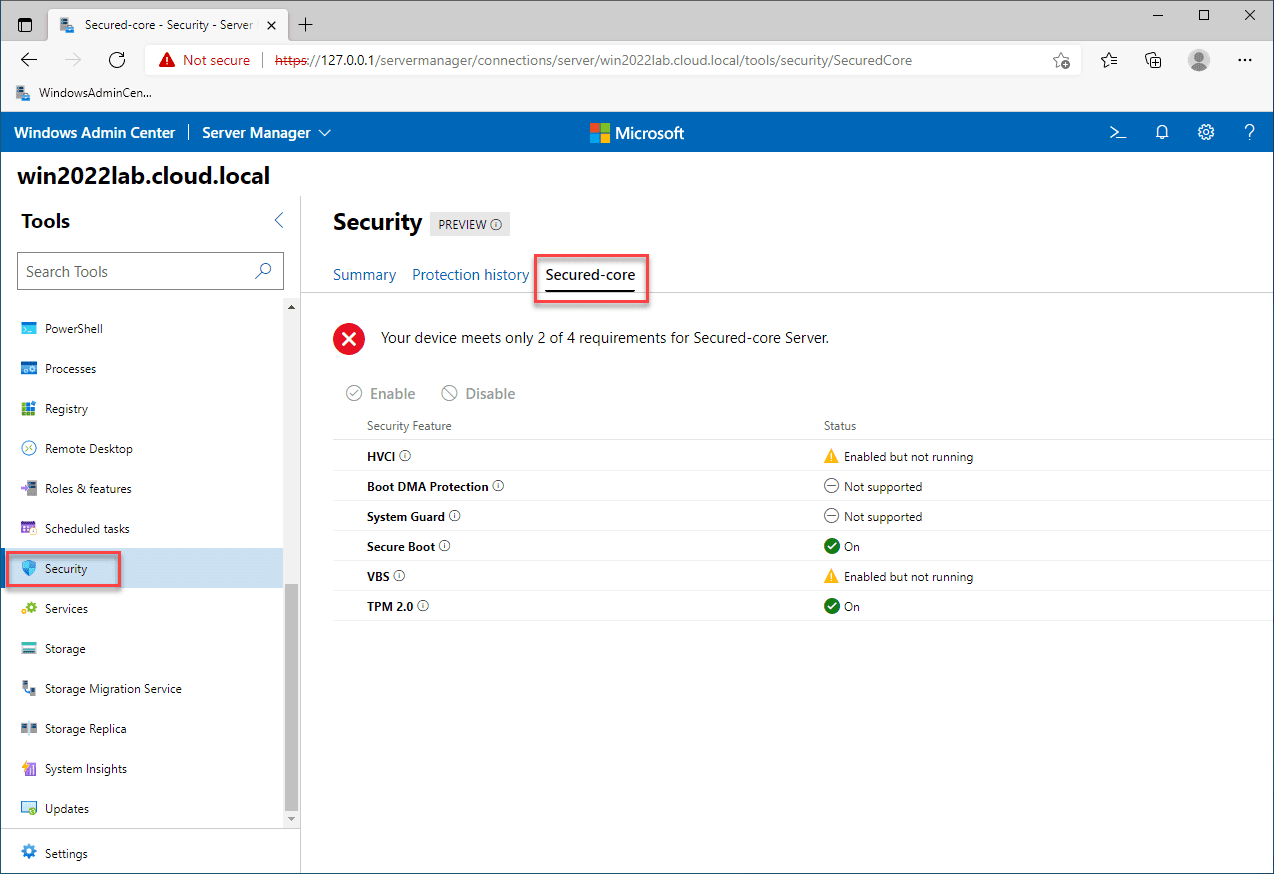
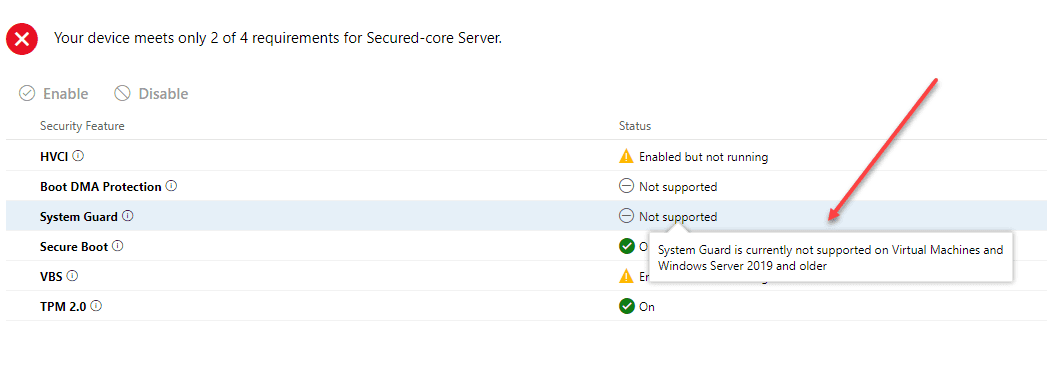
After you have installed the Security Preview extension, you will see the third tab (only available with the Insider version) called Secured-core. When you view the Secured-core tab, it displays the features of Secured-core and tests your Windows Server 2022 installation and security configuration for the six areas detailed above. As you can see below, there are security technologies in my installation that are not supported or enabled.
Windows Server 2022 Secured Core Virtual TPM
As you can see in the screenshot above, I do have the TPM 2.0 and Secure Boot technologies working. Since this is a virtual machine, how do you get the TPM device as recognized in Windows Admin Center Secured-core screen? The Virtual TPM device is a new feature of both VMware vSphere and VMware Workstation. You can effectively create a virtual instance of your hardware TPM device installed in your host (vTPM).
In my case, I do not have a TPM device installed in my vSphere ESXi host, but I do have a TPM 2.0 device installed in my VMware Workstation host. Let’s see how to enable vTPM in VMware Workstation. It involves the following steps:
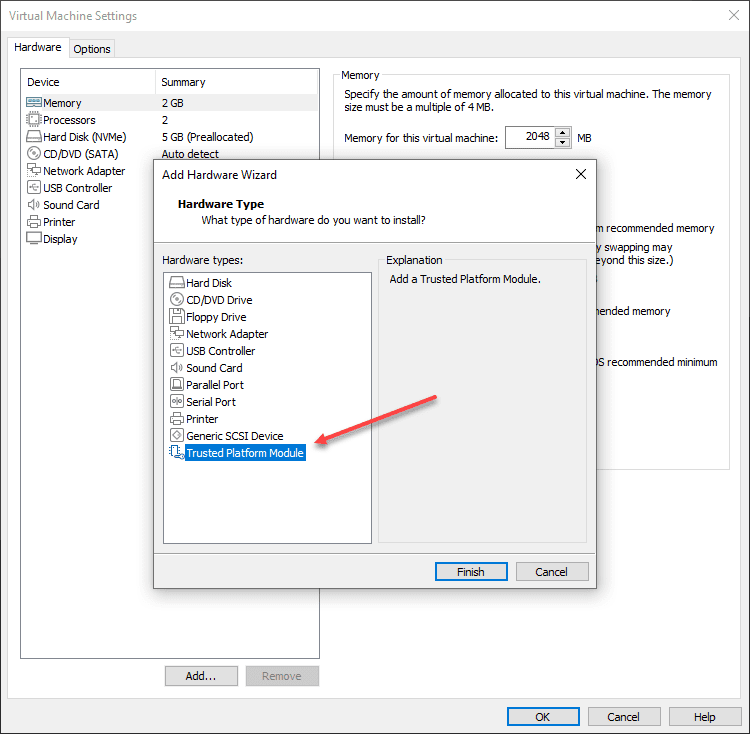
- Encrypt your VM
- Add the Trusted Platform Module
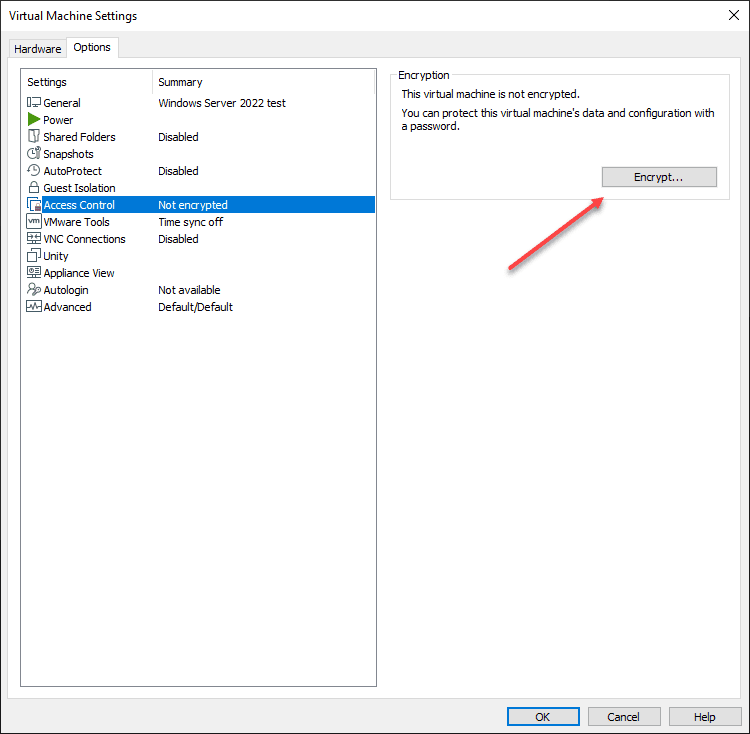
Below, after you create the VM, you navigate to Access Control and Encrypt.
After encrypting the virtual machine, you can launch the Add Hardware Wizard and select the Trusted Platform Module. Note, once you add the TPM device, it holds the encryption key. So, if you remove it, your VM is toast.
Considerations for Secured-Core VMs
There are some components of the Secured-Core functionality that are not supported on virtual machines. One of these is the System Guard.
Also, I had bit of competing technologies and issues with getting VBS enabled correctly for my VMware Workstation VM. I have other hypervisor-assisted technologies being used that caused some conflicts such as WSL and Docker installed on my host.
Concluding Thoughts
Hopefully, you have found this explanation of the Windows Server 2022 Secured Core Virtual TPM setup useful and the overall vision of Microsoft with the new secured-core technology. I think it will provide transparency and visibility to admins on the security stance of their Windows Server 2022 servers in production so is a step in the right direction. There looks to be work still left to do for VMs though with Secured-core.


1 Comments
This post gave me a lot of information on this topic. Keep it up and keep sharing this type of information with us. Try to explore our services towards digital transformation.
ReplyDeleteData Analytics Solutions
Data Engineering Solutions
Artificial Intelligence (AI) Solutions