If there is one worry among organizations today concerning their data, it has to be ransomware. Ransomware is continuing to plague businesses at an alarming rate. Ransomware variants are continuing to plague businesses by invading networks, locking up data, and now threatening to expose sensitive data to the Internet. Backups are crucial to overcoming the damage inflicted by ransomware. However, backups need to be protected properly. How can businesses protect their backups from ransomware? What other effective security layers need put in place in addition to effective backups? Let’s look at backup strategy for ransomware attacks and see what capabilities you need to protect your business.
The ransomware threat is increasing
Why is the threat of ransomware on the rise? Ransomware has become the go-to attack among cybercriminals today. It is extremely effective at doing what it sets out to do – lock up your data. In addition, ransomware is becoming easier to find and use for cybercriminals. Ransomware-as-a-Service (RaaS) has been a paradigm shift in the availability of ransomware to attackers.
Ransomware-as-a-Service (RaaS) is a malicious take on Software-as-a-Service (SaaS). SaaS provides software as a service that is consumed as such. You don’t have to worry about the infrastructure, how the software works, or any of the details underneath. It just works and does what you want it to do. This is the model that is used by Google Workspace and Microsoft 365.
This new ransomware model allows even novice hackers to have access to very sophisticated ransomware, end-to-end. The ransomware gangs responsible simply take a small percentage of the ransomware payment if this is successful. The new Ransomware-as-a-Service (RaaS) trend has proliferated the use of ransomware across the board to attack unsuspecting businesses. It has made ransomware accessible and even more dangerous due to the RaaS model.
This is a new trend where ransomware gangs and attackers making use of Ransomware-as-a-Service offerings are doubly extorting victims for a ransom payment. The first extortion is the ransom demanded to unlock the data that has been encrypted. The second ransom is demanded to prevent the intentional leaking of sensitive information to the dark web.
Arguably, the second risk may even be more dangerous than the first. Data leaks can damage business reputation and tarnish customer confidence. The effects from both of these can potentially last for years.
Note the following dangers:
- Ransomware is now performing double extortion
- If you pay the ransom, it is no guarantee it will prevent you from being attacked again
- It is also no guarantee you will get your data back as decryptors can be buggy and slow
- Backups are also targeted by attackers so these need to be protected.
Backup Strategy for Ransomware
When it comes to ransomware, you need to have a strategy for backing up your data. What? Isn’t a single backup of your data good enough on a server you have in your data center? Most likely not. You are rolling the dice to think that your backup data is not in danger as well. It leads to the conclusion that businesses need to seriously think about their backup strategy. Let’s consider the following in thinking about your backup strategy for ransomware.
- Use the 3-2-1 backup best practice model
- Encrypt your backups
- Separate your backup infrastructure from your production network
- Use immutable backups
- Encrypt your production data
1. Use the 3-2-1 backup best practice model
The 3-2-1 model works on the premise of diversifying where your data is stored and having multiple copies of your backup data. This helps to minimize the risk of attackers getting to “all” locations where you have your backups stored. Like many security best practices, providing layers of protection for your backups by storing copies in different places helps businesses not have all their “eggs in one basket.”
Using the 3-2-1 backup model, even if attackers are able to get to your primary backup repository, they most likely won’t be able to access the backups stored in an offsite location if security measures are correctly implemented between the main site network and offsite location.
3-2-1 backups generally use several types of backup technologies found in modern backup solutions. These include:
- Backup copies – secondary copies of your data allowing you to provision an exact copy of your backup data in another repository, offsite or in the cloud.
- Replication – Replica virtual machines are a great way to protect workloads at a site level. With replication, you essentially are creating a warm standby VM in another data center that can take over if the primary location fails or is attacked with ransomware.
- Versioned backups – multiple backup versions allow admins to pick a restore point that is prior to the ransomware attack and restore good copies of data.
2. Encrypt your backups
Encrypting your backups, like encrypting your data prevents the bad guys from getting copies of your backup data, mounting the backups in the same backup solution, and getting access to your data. It can be easy to forget that backup data contains production data that is no less sensitive or important. Don’t give attackers the easy ticket to backup access by not encrypting your backups.
Backup encryption needs to take place both in-flight and at-rest. With both types of encryption in place, your data is never sent over clear text in any part of the journey, both over the network and when it is stored on disk. Often, solutions may encrypt data on disk but neglect to do so as the data is transmitted over the wire.
Attackers are often on your network long before they launch a ransomware attack. So, they have time to setup and start sniffing network traffic at various points in the network to begin getting access to any data that is sent clear text.
3. Separate your backup infrastructure from your production network
It is definitely best practice to separate your backup infrastructure from your production network. Placing your backup servers on the same LAN as all the other workloads and even clients greatly increases the risk to your backups. If an attacker infiltrates the perimeter network and is able to gain a foothold on a workstation, it leads to easy access to anything that is on the same network segment, including backup servers.
It also greatly increases the likelihood of backup data getting encrypted along with normal business-critical data during a ransomware attack as ransomware often “crawls” the network to find any data it can get to from a network standpoint.
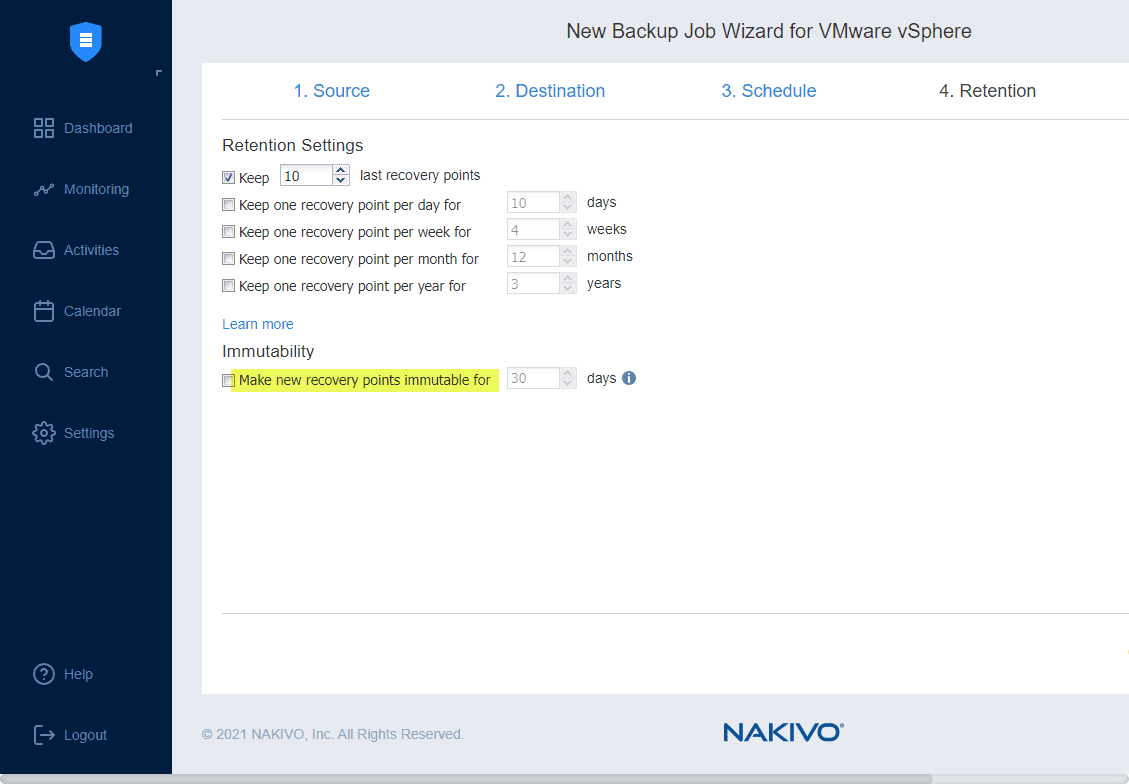
4. Use immutable backups
Immutable backups are a new backup technology that has roots in the public cloud. Amazon S3 object lock introduced the ability to have objects made immutable. This means they cannot be deleted, even by an administrator. This technology has made its way into commercial backup solutions that now allow making local backup repositories immutable.
It means that attackers cannot delete or change your backup data when they get into your environment. With your backups made immutable, your backup data is protected from the changes that are made by the ransomware encryption process.
5. Encrypt your production data
Last but not least, we mentioned encrypting your backup data. It is equally important, thinking about data backups and how attackers can gain access to your data, to encrypt your production data as well. Here we are talking about the good kind of encryption – encryption you are in control of. When you encrypt your production data, attackers can’t just exfiltrate massive amounts of data as they can easily do with clear text data. Any data they copy off that hasn’t been decrypted will be unreadable.
This drastically reduces the chances of massive data leaks made possible by large data exfiltration by cybercriminals as is now so common with major ransomware attacks.
Backup Strategy for ransomware with NAKIVO
There is no question your data protection solution of choice has a tremendous impact on the backup strategy for ransomware attacks that are devised for your organization. After all, the capabilities and features of the backup solution directly determine what tools you have at your disposal for creating resilient backups that are protected from ransomware.
NAKIVO Backup & Replication is an excellent backup solution that provides modern backup capabilities for protecting backups against ransomware. NAKIVO allows businesses to align their backup strategy for ransomware with the 3-2-1 backup best practice model.
NAKIVO has the capabilities built-in that we mentioned earlier, including:
- Backup copy jobs
- VM replication
- Versioned backups
- Site recovery orchestration
- Immutable backups
- Multi-factor authentication
- A hardened Linux appliance
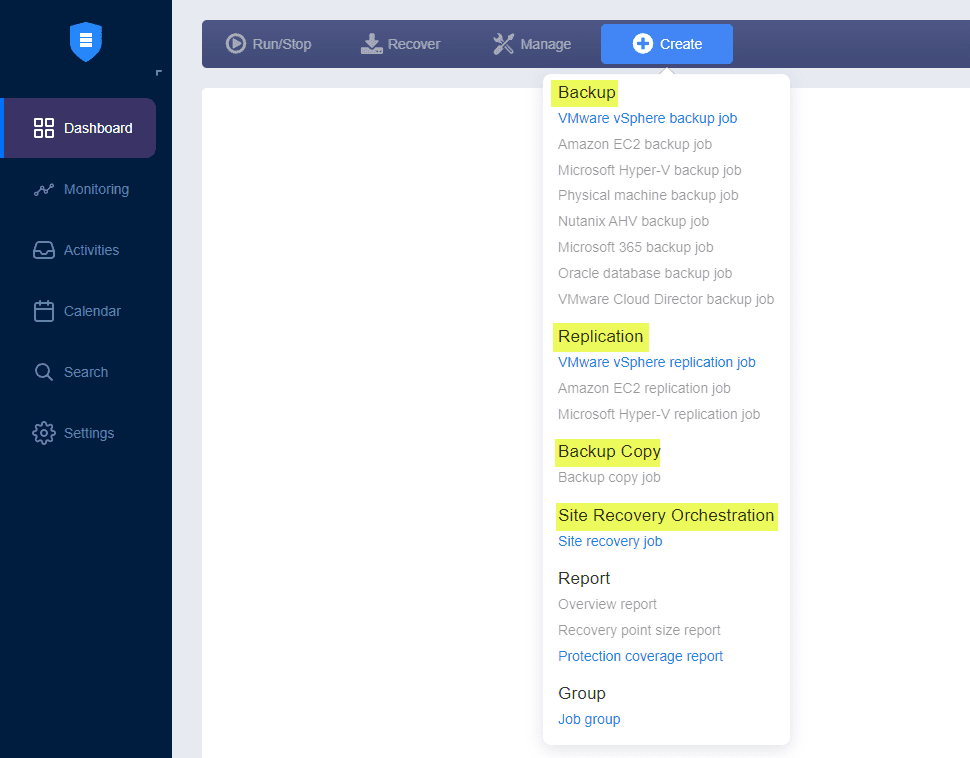
Notice the wide range of technologies and backup types that can be chosen when creating a new job in NAKIVO. ***Note*** the greyed-out items mean we don’t have the particular hypervisor technology added to our inventory. In the environment below, only vSphere is available.
NAKIVO provides backups, replication, backup copies, site recovery orchestration and other benefits.
NAKIVO also provides immutable backups that allow you to protect your backups from ransomware encryption by setting a flag that prevents deleting or modifying the backups.
Wrapping Up
Having a backup strategy for ransomware in place is a great way to proactively prepare your organization for a ransomware attack. With the escalating ransomware threat, it is most likely not if your business is attacked, but when. Choosing a data protection solution that allows protecting your data using modern backup best practices and new tools such as backup immutability is a great way to bolster your backup strategy for ransomware attacks.
NAKIVO Backup & Replication, as shown, provides great features and capabilities that provide the tools needed for bolstering your backup strategy.
Take a look at NAKIVO Backup & Replication and download a fully-featured trial version to test out the full set of production features in your lab – https://www.nakivo.com/

0 Comments