When it comes to architecting cloud IaaS environments, one of the issues that always comes to the forefront after standing up infrastructure is access. How do engineers, developers, contractors, and others access environments from the outside? The first tendency of course is just to throw a public IP on everything and allow access this way. However, this can create grave security concerns that are not ideal for any organization with today’s high-profile ransomware and other cybersecurity threats. Specifically, in Azure, let’s look at how to access Azure VM from outside and see what mechanisms you can leverage to do that.
Why public access is a security concern
Some may wonder, if I have everything secured even with very strong passwords, why do I need to worry about putting virtual machines and other cloud resources out on the public Internet with a public IP. One of the first tenants of good cybersecurity is minimizing the attack surface. Sticking a virtual machine, no matter how secure, out on the Internet is poking a hole in your defenses.
Even if your VM is fully patched, what if an attacker has possession of credentials of a user who has been granted access to that resource? Today, many attacks begin with a phishing attack that harvests credentials. Breached password lists readily available on the dark web or public Internet can also contain real passwords used by others, potentially in your organization. After all the Colonial Pipeline attack was learned to have started with breached VPN credentials found in a breached password list.
The fewer resources you place on the Internet, the better. It simply minimizes the attack surface and makes it more difficult for an attacker to compromise an environment.
How to Access Azure VM from outside
Let’s take a look at the following ways how to Access Azure VM from outside. These include the following:
- Azure Bastion host
- Virtual Private Network (VPN) connection
- Public IP Address
1. Azure Bastion host
Arguably, the preferred way to access Azure VM from outside is the Azure Bastion host PaaS service. This is a relatively newer service from Microsoft that allows users to access internal VMs without using an external IP address on the internal virtual machines. This alleviates the need to stick everything that you need to access on the Internet and greatly diminishes the attack surface of the internal VMs hosting resources.
As you noticed, we called this a PaaS service. That’s right, it isn’t a VM you have to stand up, maintain, and secure. Microsoft does this for you. That means all the security burden of the Azure bastion host is taken on by Microsoft which is great. Setting up the Azure Bastion host is simple as well. As a note, to use the Bastion host, you will need to be logged into the Azure portal.
Configuring Azure Bastion host
Search in the Azure portal for Bastion and it will bring up the Azure Bastions configuration. Click the Create button.
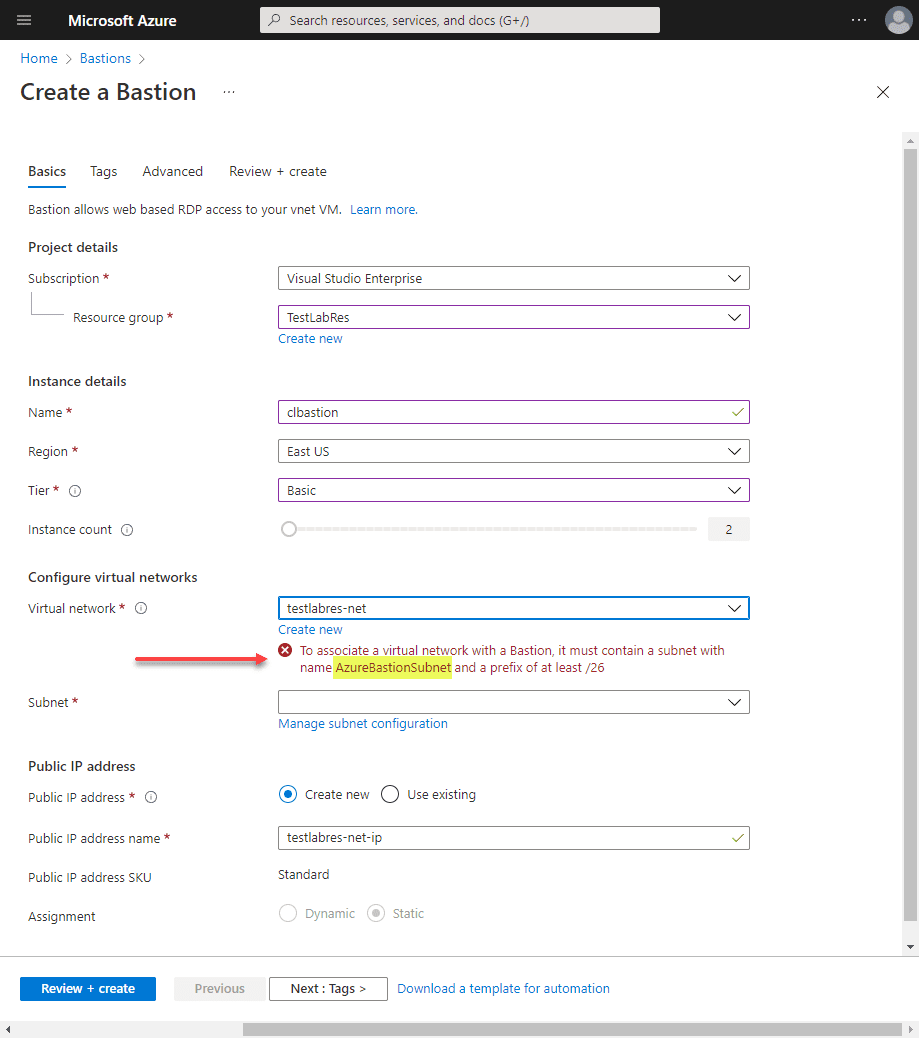
If you just quickly buzz through the blade to create a Bastion, you will most likely get an error on the virtual network section. One of the requirements of creating the Azure Bastion is you have a virtual network explicitly named AzureBastionSubnet.
Azure Bastions are needed for each Azure virtual network. So, you will need a subnet explicitly named for the Azure Bastion host.
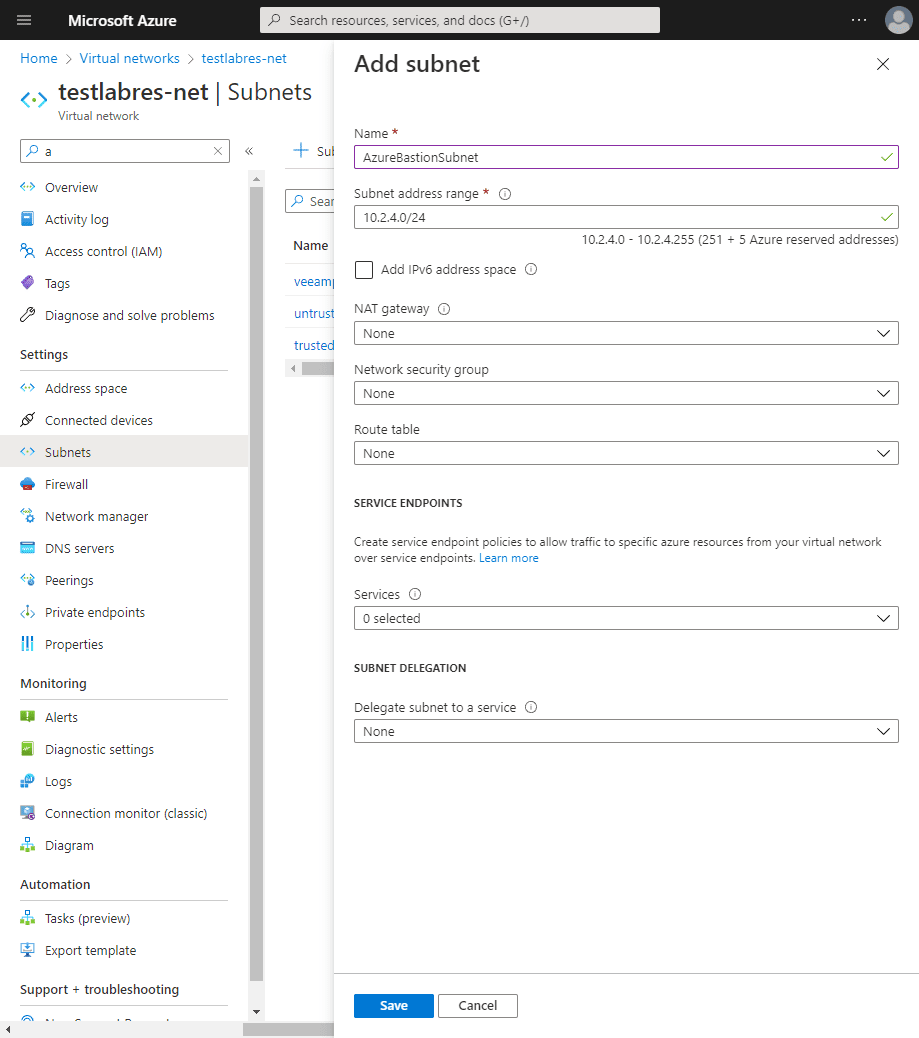
Below, is adding the purpose-built subnet for the Azure Bastion host.
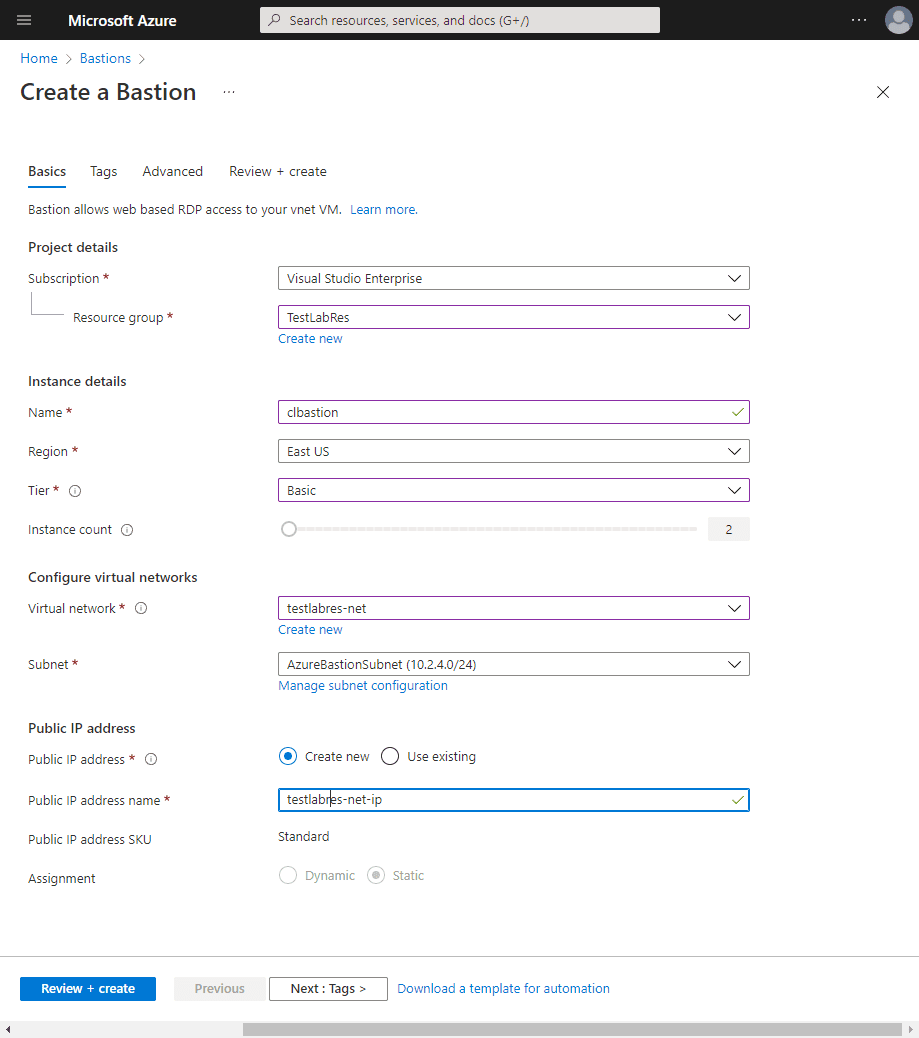
Now, after returning from creating the subnet, we now do not see any errors with the Subnet configuration.
After the above configuration screen, you can next through the other screens unless you want to set up Tags and more granular network config, etc. The Azure Bastion host will spin up in just a few minutes.
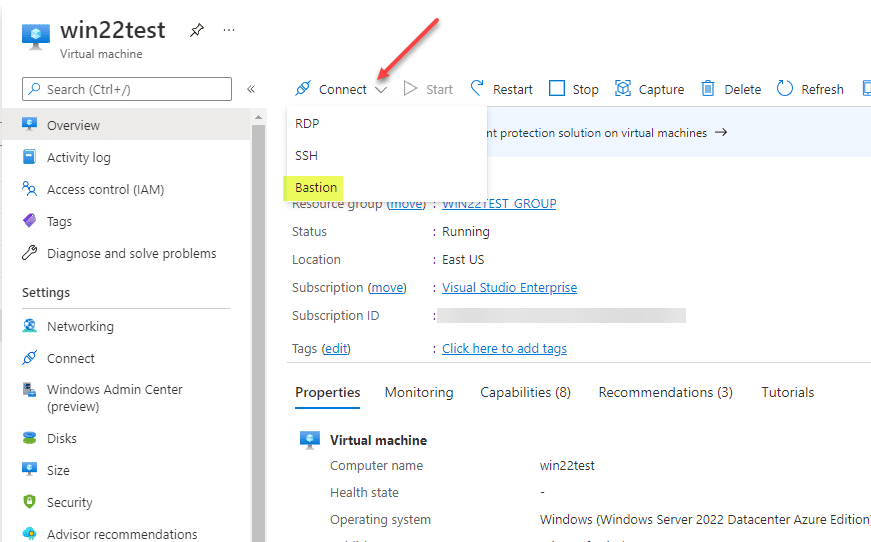
Connecting to Azure VMs with the Bastion option
Now, when you view an Azure VM and click the Connect option, you will see the Bastion option.
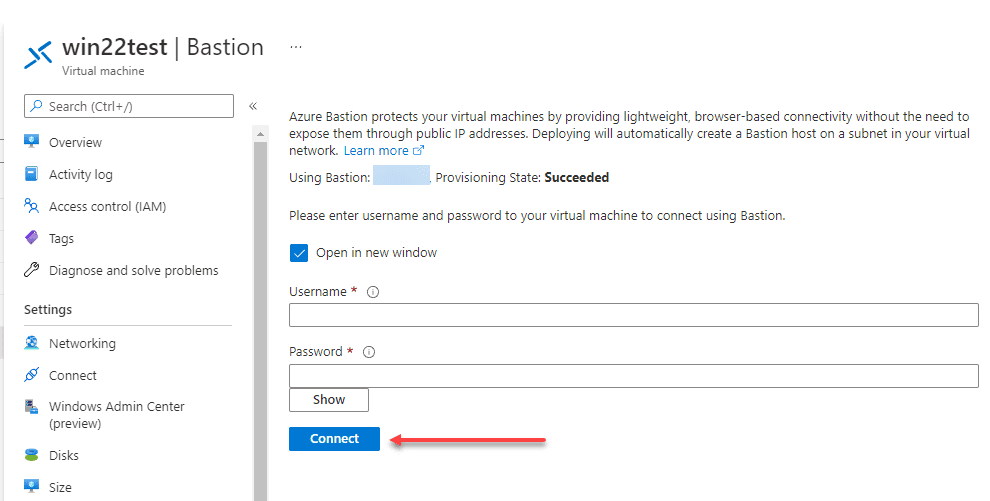
When you click Bastion, you will see the option to enter the username and password for the internal resource.
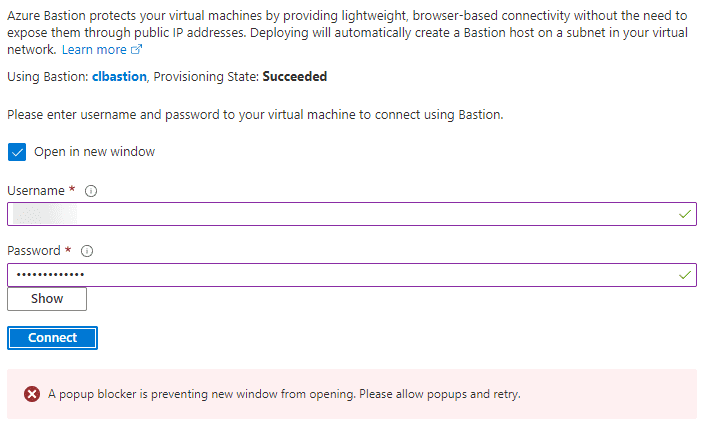
One thing to note, the Bastion connection will pop up a new browser window. Microsoft will let you know if your pop-up blocker is getting in the way of launching the connection window.
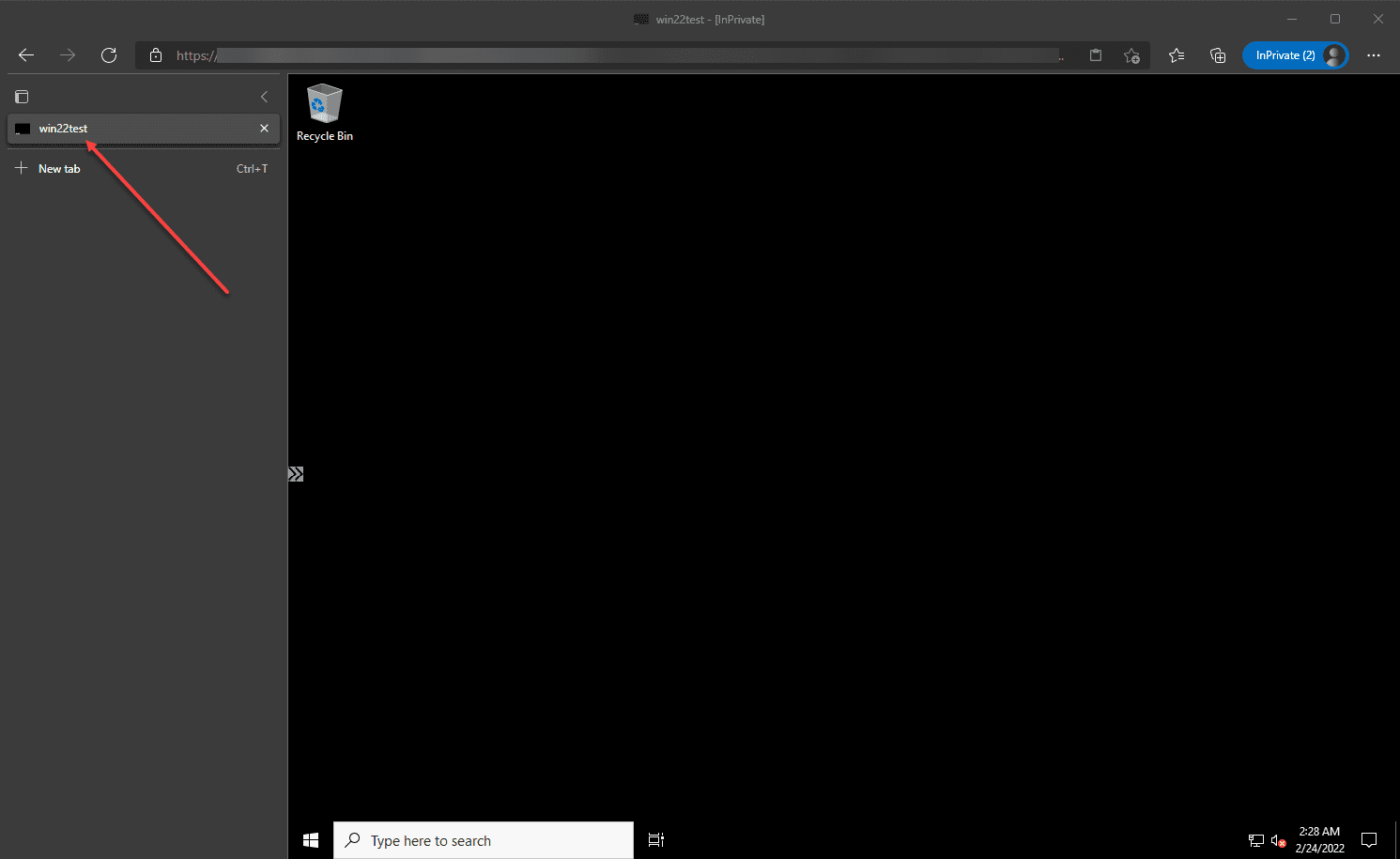
Below, I have successfully authenticated and connected to a Windows Server 2022 virtual machine. Again this was using the Bastion host, without a public IP assigned on the internal VM.
2. Virtual Private Network (VPN) connection
VPN connections have been around for decades now. Creating a VPN connection is a viable option for accessing Azure internal VMs. It can be wrought with challenges and security issues if not managed and configured correctly. Any VPN connection technologies need to be enabled with MFA to help secure against scenarios such as what happened with Colonial Pipeline.
Microsoft Azure offers VPN solutions as an Azure offering that supports the normal IKEv1 and IKEv2 configurations from most security and VPN solution vendors. There are pros and cons to VPNs:
Pros:
- The technology is usually familiar to organizations as they have been traditionally used
- Most vendors support connecting to Microsoft Azure solutions
- You don’t have to be logged into the Azure portal to connect to internal VMs
- It can support MFA if configured and supported by the VPN clients
Cons:
- Can be wrought with security issues if MFA is not configured
- Without MFA, passwords to VPN connections can be cracked or breached
- VPNs can be difficult to manage
- They don’t scale very well
3. Public IP Address
The final option, which isn’t recommended is using public IP addresses. Public IP Addresses are dangerous from a security perspective. Can they be leveraged successfully? Yes, they can. Organizations have to realize and take on the security risks associated with using public IPs.
If public IP addresses are used, network security groups need to be used to restrict access and this can be a bear to manage. Also, there are solutions out there that can multifactor enable RDP and SSH protocols such as Duo Security. This is a must if you are considering sticking these dangerous services on a public IP address.
Azure Bastion Host FAQs
- What is Azure Bastion Host? It is a PaaS service that provides a built in “jump box” for Azure portal users to connect to internal virtual machines without assigning a public IP address. With Azure Bastion, Microsoft manages the security and lifecycle management of the solution.
- What are Azure Bastion host advantages? – It is fully managed by Microsoft and provides a secure way to log into internal virtual machines both by Remote Desktop Protocol (RDP) and Secure Shell Protocol (SSH).
- Is Azure Bastion host free? It is free to try but is a pay-as-you-go service. You can note the pricing for Azure Bastion here: Pricing – Azure Bastion | Microsoft Azure
- How do you secure Azure Bastion host? – Azure Bastion is a PaaS service that is maintained and managed by Microsoft. You as the customer don’t have to do anything to secure Azure Bastion. It is secured and maintained for you by Microsoft. This makes it even more attractive for use.
Final Notes
How to Access Azure VM from outside is a question that organizations do not need to take lightly as it can lead to compromise, data breach, and other cybersecurity concerns if not carried out correctly. There are many ways to secure the Azure internal virtual machines configured in a vNet. We have discussed three of those in this post, with Azure Bastion arguably being the most attractive of the three discussed. Let me know your thoughts and what you are doing to secure your Azure environments.


0 Comments