In working with Proxmox, one of the cool features as part of the solution is the Promox firewall and firewall rules. Proxmox VE firewall is a firewall service that allows configuring firewall rules for filtering traffic to the Promox server, containers, and virtual machines. It also provides the really cool capability of implementing cluster-wide firewall rules. Let’s take a look at the Proxmox firewall rules configuration and see how these are implemented.
What is the Proxmox firewall?
The Proxmox firewall is a fully functional firewall built-in solution that updates the underlying iptables rules automatically in the Proxmox server, clusters, containers, and virtual machine guests. It provides the added benefit of cluster-wide firewall configuration that provides a central firewall solution implemented with firewall configuration files.
You can implement:
Generated iptables rules
Host-specific firewall rules
VM specific firewall rules
Create rules that can filter traffic on network interfaces
Security group implementation
Proxmox VE hosts security
Filter remote IPs
When mastering Proxmox, learning about the firewall configuration is a core concept and provides an really great feature for securing your Proxmox servers and workloads.
Proxmox VE Firewall features
The firewall is completely customizable, allowing complex configurations via the Proxmox GUI or CLI commands. You can set up cluster-wide firewall rules or define rules for VMs and containers only if you want.
It offers the building blocks for automating the firewall’s configuration by allowing you to use the CLI, firewall macros, security groups, IP sets, cluster-wide alias definitions, and cluster-wide firewall options that can be used in Proxmox cookbook configuration files.
A distributed nature firewall service
The Proxmox firewall configuration file is stored at the data center level in the Proxmox cluster file system. So, it is essentially a firewall cluster. It is an IP-based system that is automatically distributed across the Proxmox cluster hosts.
It can provide the building blocks of micro-segmentation as it provides full isolation between virtual machines you enable with the service.
The distributed nature of this system also provides much higher bandwidth than a centralized firewall solution, much like the advantages of the VMware NSX distributed firewall service. However, the Proxmox firewall solution is totally free and open source.
Supports both IPv4 and IPv6
The firewall has full support for IPv4 and IPv6. IPv6 support is fully transparent, and both are filtered by default. So, there is no need to maintain a different set of rules for IPv6.
Very granular
The beauty of the Proxmox firewall is you can be very granular with how the firewall rules are implemented down to a single virtual machine or single IP address.
Proxmox firewall concepts
Let’s better understand the Proxmox VE firewall concepts that make the service work.
Proxmox ve firewall zones
There are two logical zones for which you can create firewall rules for incoming or outgoing traffic:
Host – Traffice to/from the Proxmox cluster node
VM/container – Traffic to/from a specific VM or container
Proxmox VE firewall configurations via files
The firewall configurations with Proxmox VE firewall are implemented using configuration files stored in the cluster file system. These files are automatically distributed to all cluster nodes. Then the PVE-firewall service updates the underlying iptables rules automatically when changes are made.
These configurations are implemented at different levels. From the GUI, you can configure the Datacenter > firewall or you can click on a Node > firewall and make changes there. You can also edit the firewall configurations using a text editor by low-level editing files.
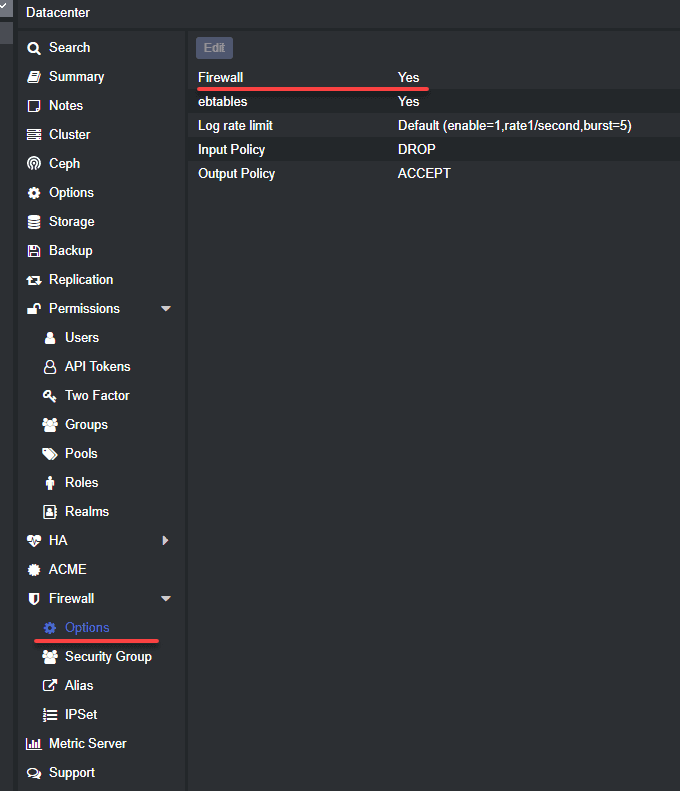
Below, is the Datacenter > firewall view showing the firewall and options available.
Here, we have enabled the firewall at the datacenter level.
The firewall blocks all traffic by default!
As a word of wisdom and warning, when you enable the Proxmox firewall service at the datacenter level, traffic to all hosts is blocked by default. There are two exceptions to that traffic block behavior:
Web GUI – port 8006
SSH – port 22
These two ports are left open when you enable the firewall service at the datacenter level.
Enable the firewall service from the command line
You can enable the firewall service from the command line using the command:
enable firewall
Ports used by Proxmox
Below is a list of commonly used ports by Proxmox:
Web interface: 8006 (TCP, HTTP/1.1 over TLS)
VNC Web console: 5900-5999 (TCP, WebSocket)
SPICE proxy: 3128 (TCP)
sshd (used for cluster actions): 22 (TCP)
rpcbind: 111 (UDP)
sendmail: 25 (TCP, outgoing)
corosync cluster traffic: 5404, 5405 UDP
live migration (VM memory and local-disk data): 60000-60050 (TCP)
Host, VMs, and containers configuration files
The host firewall configuration file that allows securing the virtual network device is located at:
/etc/pve/nodes/<nodename>/host.fw
The VM/container level configuration file is located at:
/etc/pve/firewall/<VMID>.fw
Firewall rules configuration direction
Firewall rules can be configured with a direction (IN or OUT), allowing you to block incoming traffic or outgoing traffic in or out of your Proxmox node. Also, you can configure an action (ACCEPT, DENY, REJECT). You can also specify a macro name. Macros contain predefined sets of rules and options. Rules can be disabled by prefixing them with |.
Security groups and IP aliases
Security groups make administering the Proxmox firewall service easier, where you can create a collection of cluster-level rules that can be used in all VM rules. IP aliases allow you to create and associate IP addresses of networks and give these a meaningful name.
Security group configuration is stored at /etc/pve/firewall/cluster.fw
Proxmox firewall CLI commands to know
To start and stop the Proxmox firewall from the command line, use:
pve-firewall start
pve-firewall stop
pve-firewall status
See the generated IPtables rules
iptables-save
Adding a Proxmox firewall rule
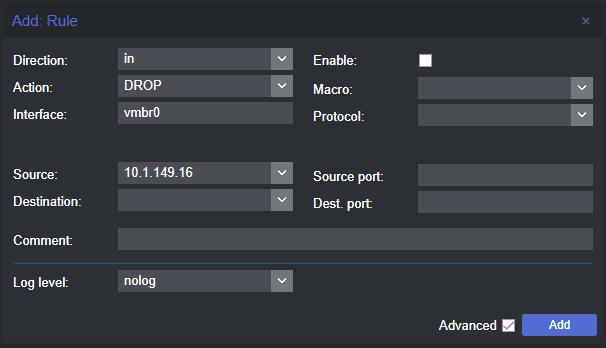
When you click the add button, you will see the Add Rule dialog box. Here, you can configure a new firewall rule with the following settings (not all are required):
Direction
Action
Interface
Source
Destination
Comment
Macro
Protocol
Source port
Dest port
Log level
Enable
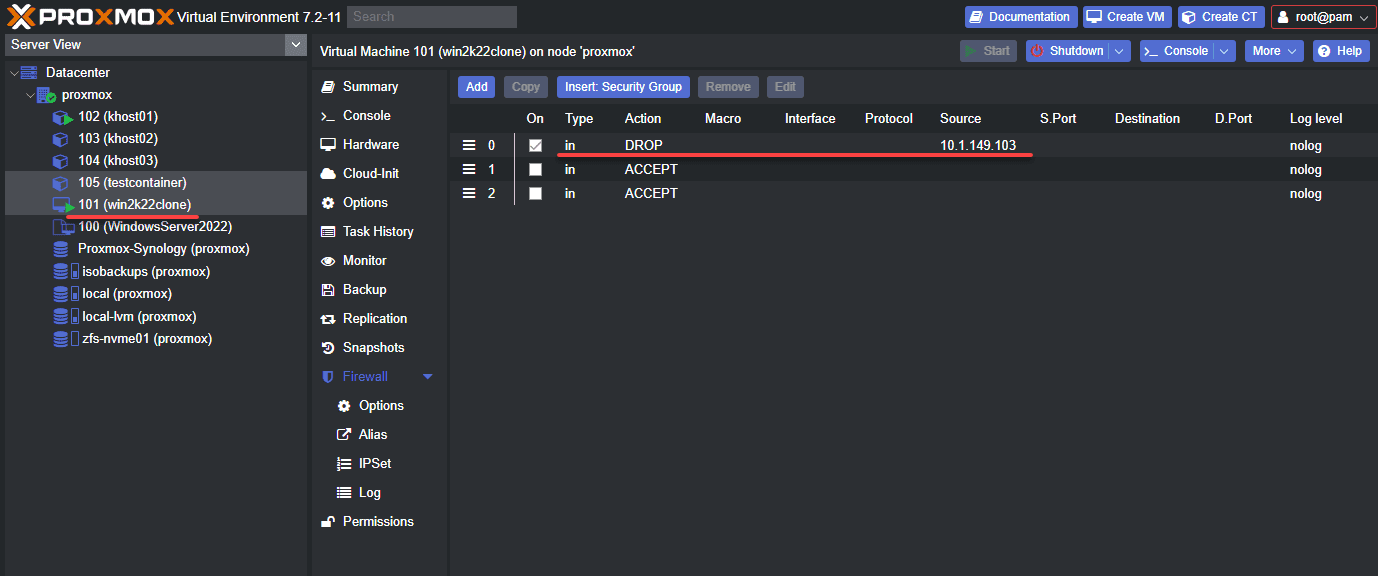
Below is a virtual machine with a firewall rule blocking traffic from a specific host.
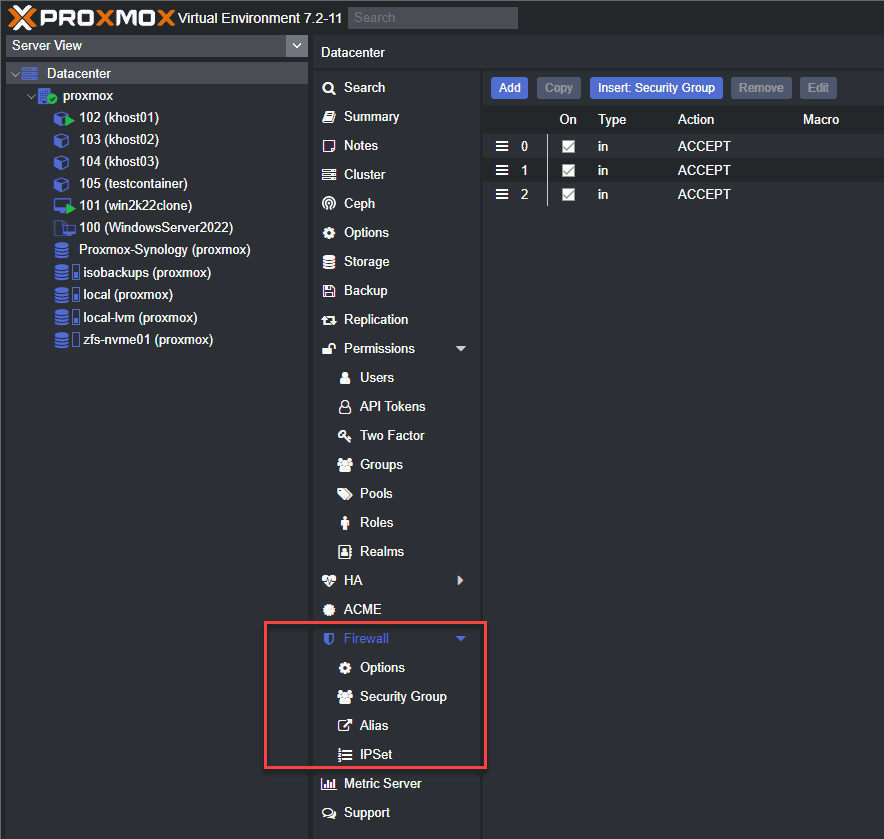
Adding Security Groups and Rules
The Security Group for the Proxmox firewall rules is a great way to group rules together for easily applying them in the environment.
If you browse to the Datacenter view, you can create the security group and associated rules. These can then be inserted at the host or VM/container level.
Wrapping Up
The Proxmox firewall rules configuration is powerful. It allows creating very granular and also, cluster wide firewall configurations that are distributed in nature. These can be applied also to specific VMs in the environment. You can control the firewall service via the GUI or using the command line.
Check out more information about the Proxmox firewall here: Firewall – Proxmox VE.



0 Comments