Proxmox VE is a great solution for home lab environments and production workloads, including virtual machines and containers. A great feature of Proxmox VE is the firewall, which enables administrators to manage network traffic to and from virtual machines and containers. This article will explore the Proxmox firewall and its configuration options.
Proxmox Firewall Rules Configuration
Proxmox firewall is based on the Linux iptables firewall. It is designed to filter network traffic at the hypervisor layer. With the firewall, you can filter traffic based on source and destination IP addresses, protocols, and ports.
Many management options exist, including the Proxmox web interface (web GUI) or command-line interface (CLI). These can be used to configure firewall rules and implement cluster-wide firewall configuration in your Proxmox cluster.
Zones configuration
You can divide the firewall into zones. This combines network interfaces and IP addresses. By default, notice the four zones available in Proxmox VE.
Input – handles incoming traffic from external networks
Output – handles outgoing traffic to external networks
Forward – handles traffic between virtual machines and containers
Host – handles traffic to and from the Proxmox host
Cluster Wide Firewall Rules
With clustered Promox configurations, you can have firewall rules to apply to all nodes in the cluster. This is done by configuring the underlying iptables rules automatically and using the same firewall configuration files on all nodes. You can also configure a central firewall solution for the entire cluster by creating a firewall cluster.
Proxmox VE Firewall Zones
To manage the firewall, you need to enable the firewall service. Once enabled, you can configure the firewall zones using the web interface or the command line.
You can also assign IP addresses to zones and create firewall rules that allow or block traffic based on the zone.
Enabling the Firewalls
The Proxmox firewall is disabled by default. To enable the firewall service, you can use the following command on the CLI:
pve-firewall enable
This will start the firewall service and load the firewall configuration files.
Ports used by Proxmox
Proxmox uses several ports for different services, such as SSH, HTTP, and VNC. By default, these ports are open, but you can create firewall rules to restrict access to these ports.
Firewall Rules Configuration Direction
You need to specify the direction of the traffic you want to filter with the Proxmox firewall configuration. You can choose to filter incoming traffic, outgoing traffic, or both.
Enable the Firewall Service from the Command Line
You can enable the Proxmox firewall service from the command line with the following command:
systemctl enable pve-firewall.service
This will start the firewall service on boot and load the firewall configuration files.
Proxmox VE Firewall Configurations via Files
You can also configure the Proxmox firewall using configuration files. These files are located in the /etc/pve/firewall directory and define firewall macros, security groups, IP aliases, and firewall rules.
Enabling the Firewall for VMs and Containers
The firewall is disabled by default for virtual machines and containers. However, you can enable the firewall service for a VM or container. To do this, you must add a firewall configuration file to that VM or container’s/etc/pve/firewall directory.
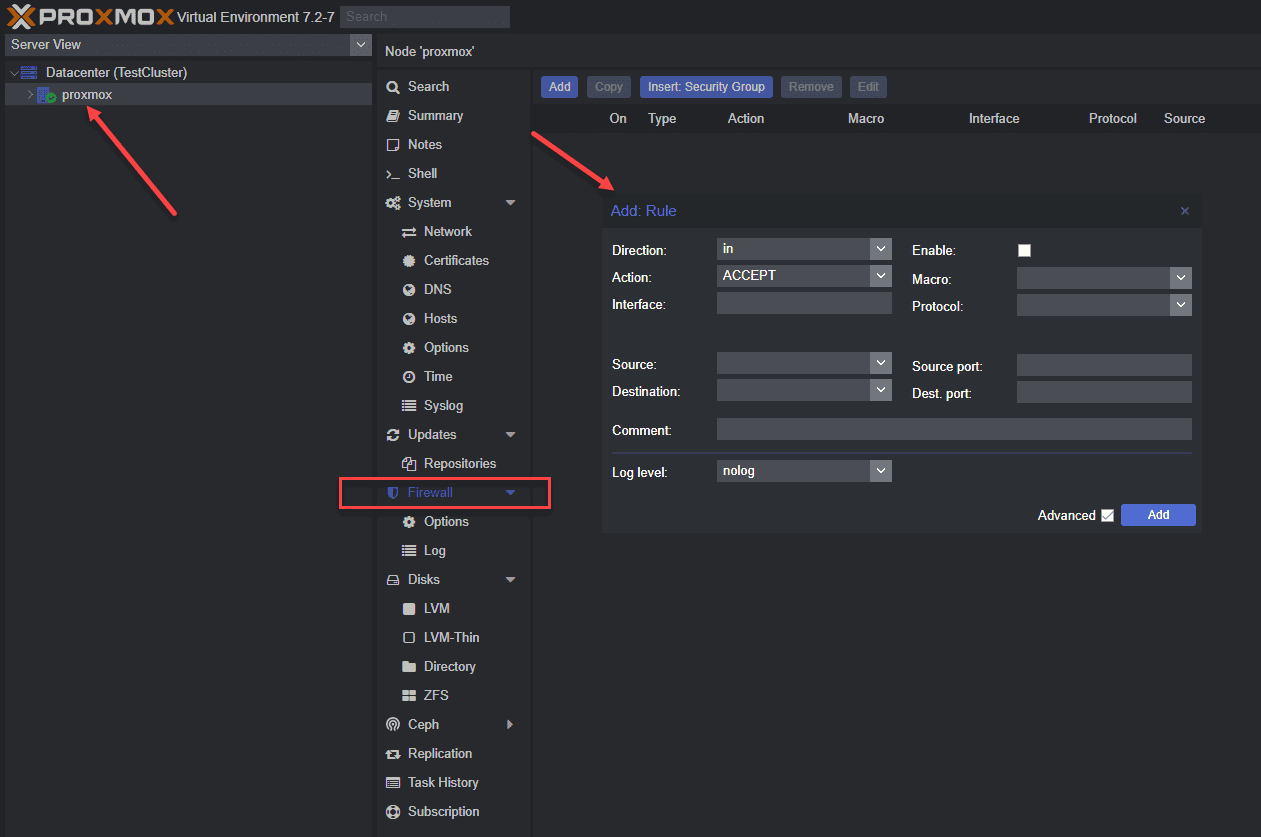
Host, VMs, and Containers Configuration Files
You can configure the Proxmox firewall using host, VMs, and container configuration files. These files define firewall rules for the respective entities and are located in the /etc/pve/firewall directory.
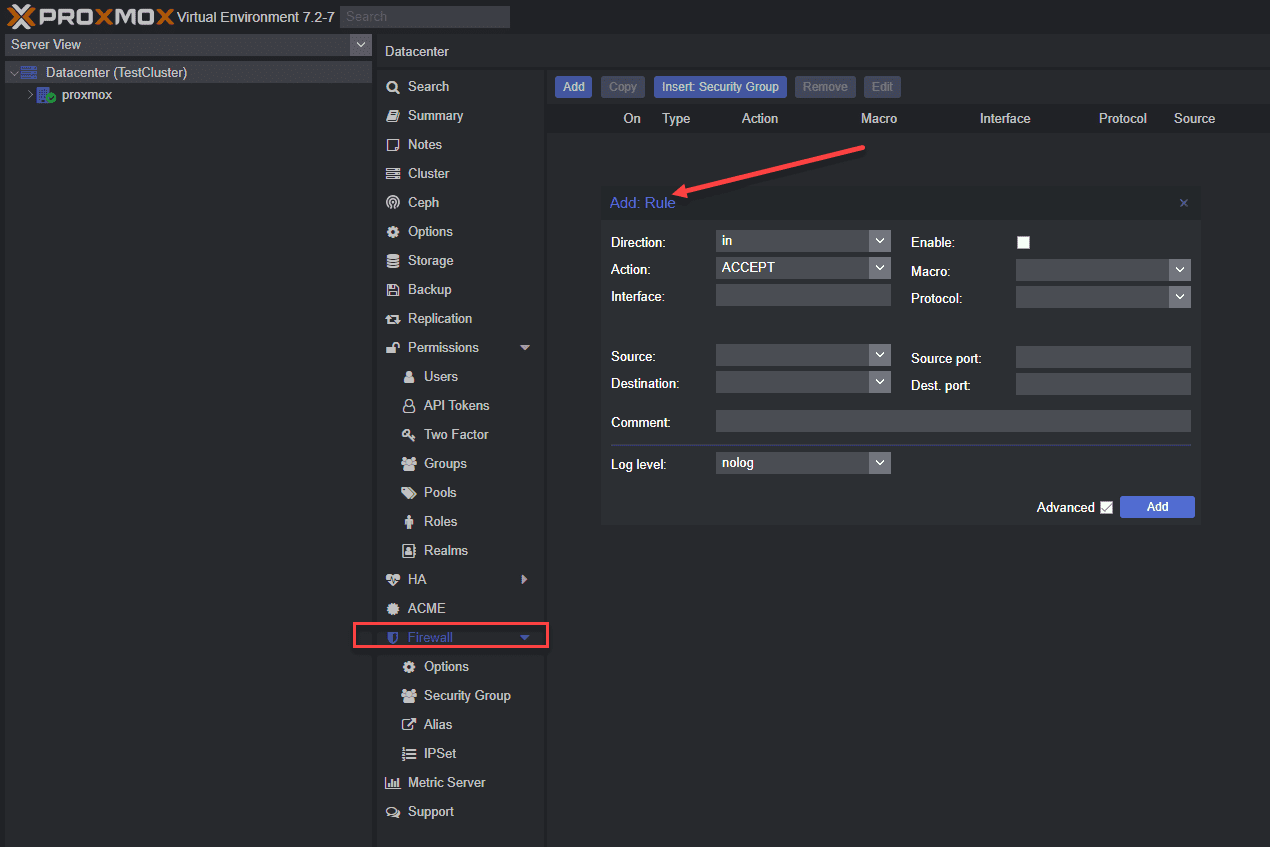
Below is a look at host-specific firewall rules.
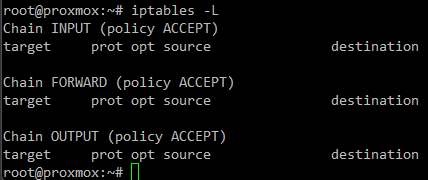
See the Generated IPtables Rules
To view the underlying iptables rules generated by the Proxmox firewall:
iptables -L
This will display the current iptables rules managed by the Proxmox firewall service.
Check VM Network Device
When you configure a Proxmox firewall rule for a virtual machine, you need to know the name of the virtual network device. You can find this by using the following command:
qm config <VM ID> | grep net
This will display the name of the virtual network device used by the VM.
IP Aliases
You can associate a single IP address with multiple network interfaces with IP Aliases. You can configure IP aliases in the Proxmox firewall using the IP alias configuration file in the /etc/pve/firewall directory.
IP Sets
IP sets define a set of IP addresses that can be used in firewall rules. You can configure IP sets in the Proxmox firewall using the IP set configuration file in the /etc/pve/firewall directory.
Default Firewall Rules
A set of default firewall rules out of the box allows incoming and outgoing traffic for certain services. These include traffic types such as SSH and HTTP. You can view the default firewall rules using the following command:
iptables -L
Standard IP Alias local_network
An example of the default IP alias is the local_network standard IP alias defined in the Proxmox firewall configuration files. It represents the IP addresses assigned to the Proxmox host and is used in firewall rules to allow traffic between the host and virtual machines/containers.
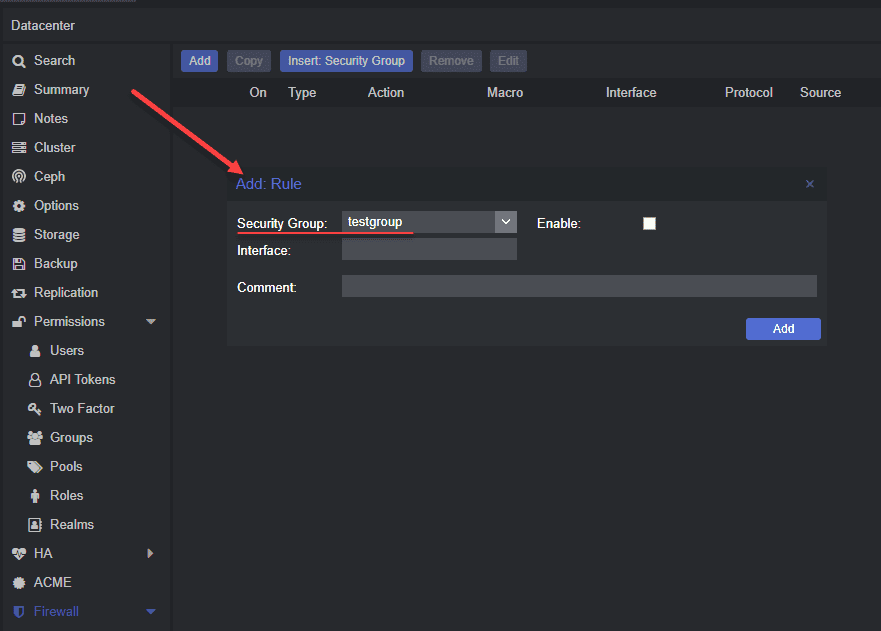
Adding Security Groups and Rules
Security groups and IP aliases can be used in the Proxmox firewall configuration files. These can then be used in firewall rules to allow or block traffic based on the group or alias.
Note the following to define security groups and IP aliases using the following syntax in the configuration files:
group <group name> { <ip addresses> }
alias <alias name> { <ip addresses> }
Below is a look at creating security group-based firewall rules.
Supports Both IPv4 and IPv6
The Proxmox firewall supports both IPv4 and IPv6 addresses. You can define rules for both addresses using the same firewall configuration files.
Proxmox Firewall CLI Commands to Know
Several CLI commands are useful when configuring the Proxmox firewall:
pve-firewall enable – Enables the firewall service
pve-firewall disable – Disables the firewall service
pve-firewall status – Displays the current status of the firewall service
pve-firewall reload – Reloads the firewall configuration files
pve-firewall log – Displays the firewall log
Adding a Proxmox Firewall Rule
To add a firewall rule to the Proxmox firewall, you must edit the appropriate configuration file in the /etc/pve/firewall directory. The syntax for adding a firewall rule is as follows:
iptables -A <zone> -p <protocol> –dport <port> -s <source address> -d <destination address> -j <action>
Cluster Nodes
If you are using a Proxmox cluster, you can configure the firewall rules to apply to all nodes in the cluster. This is done by configuring the underlying iptables rules automatically and using the same firewall configuration files on all nodes.
PVE Firewall Status
Note the following to check the status of the Proxmox PVE firewall service using the pve-firewall status command on the CLI.
Define Rules
To define a firewall rule in the Proxmox firewall, you need to edit the appropriate configuration file in the /etc/pve/firewall directory. The syntax for adding a firewall rule is as follows:
iptables -A <zone> -p <protocol> –dport <port> -s <source address> -d <destination address> -j <action>
Outgoing Traffic
You can also configure the Proxmox firewall to filter outgoing traffic based on the destination IP address, protocol, and port.
Required Firewall Rules
Certain firewall rules are required for the Proxmox VE software to function properly. These rules allow traffic for SSH, HTTP, and VNC.
Generated Iptables Rules
The underlying iptables rules generated by the Proxmox firewall can be viewed using the iptables -L command.
Automatically Distributed
If you are using a Proxmox cluster, the underlying iptables rules for the firewall are automatically distributed to all nodes in the cluster.
PVE Firewall Stop
To stop the Proxmox firewall service use the pve-firewall stop command on the CLI.
CLI Commands
Several CLI commands can be used to manage the Proxmox firewall service, such as pve-firewall enable, pve-firewall disable, pve-firewall status, and pve-firewall reload.
Remote IPs
You can manage access from remote IP addresses to bolster security. You can configure firewall rules for remote IPs using the remote.fw file located in the /etc/pve/firewall directory.
Cluster Specific Firewall
Using a Proxmox cluster, you can configure a cluster-specific firewall using the /etc/pve/firewall/cluster.fw configuration file.
Configuration Files
The Proxmox firewall is configured using several configuration files in the /etc/pve/firewall directory. These files define firewall macros, security groups, IP aliases, and firewall rules.
Corosync Cluster Traffic
You can manage traffic for Corosync cluster traffic. You can configure firewall rules for Corosync cluster traffic using the corosync.fw file located in the /etc/pve/firewall directory.
HTTP Traffic
You can also filter HTTP traffic in your Proxmox environment. You can configure firewall rules for HTTP connections using the http.fw file located in the /etc/pve/firewall directory.
Create Rules
When creating a firewall rule you need to edit the appropriate configuration file in the /etc/pve/firewall directory. The syntax for creating a firewall rule is as follows:
iptables -A <zone> -p <protocol> –dport <port> -s <source address> -d <destination address> -j <action>
Wrapping up
The Proxmox firewall is a great tool admins can use to manage and control traffic to the Proxmox data center, Proxmox hosts, and virtual machines and containers running in the environment. The firewall is based on the Linux iptables firewall and is managed using several configuration files located in the /etc/pve/firewall directory.
The Proxmox cluster firewall rules are distributed in nature and synchronized between all cluster nodes. It is a great capability that can effectively help secure workloads and Proxmox environments.



0 Comments