Forcing safe search is a great way to filter unwanted websites for children, families, and other users from sites that may feature mature content. The pfSense open-source firewall is a robust firewall with many enterprise features, including the ability to turn on safe search. Let’s look at the pfSense force safe search feature and how it can be configured.
What is pfSense?
pfSense is an open-source firewall and router software distribution based on the FreeBSD operating system. It is not only popular in home lab environments but also in the enterprise for protecting critical resources.
The flexibility and versatility of pfSense allow users to configure numerous security features, including:
Firewall rules
VPN access
Content filtering,
Force safesearch, etc
These ensure a safe and controlled browsing experience on a LAN network.
It supports traditional network services like DHCP and can house multiple interfaces to support different physical network segments for devices, etc.
What is Safe Search?
Many search engines, including Google, Bing, and YouTube, offer a feature called Safe Search that filters out explicit content. This includes:
Pornographic images, videos, and websites
Hate, violence, and other mature content
This functionality benefits families, schools, and organizations wanting to provide users with a secure and age-appropriate online experience.
Why would you want to enable Safe Search engines?
Enabling Safe Search engines is crucial for maintaining a secure and controlled online environment, especially when multiple users share the same network.
With Safe Search enabled, users are protected from accessing explicit content, ensuring a more family-friendly and work-appropriate browsing experience.
Additionally, implementing Safe Search can help organizations comply with content filtering policies and prevent potential legal issues.
How do you enable plugins in pfSense?
pfSense offers a range of plugins that can be installed to enhance its functionality and add new features. Follow these steps below to enable plugins, which will be needed, to enforce Safe Search:
Access your pfSense web interface by navigating to the IP address of your firewall in your browser.
Log in using your pfSense credentials.
Click on “System” in the top menu, and then select “Package Manager” from the dropdown menu.
Navigate to the “Available Packages” tab to browse the list of available plugins.
Locate the desired plugin and click the “+” button next to it to install.
Install pfBlockerNG
pfBlockerNG is a powerful pfSense plugin that allows users to manage and filter DNS server queries and block DNS access to specific domains, websites, or entire block lists.
pfBlockerNG allows enforcing Safe Search across your network. To install pfBlockerNG, follow these steps:
Access your pfSense web interface and log in.
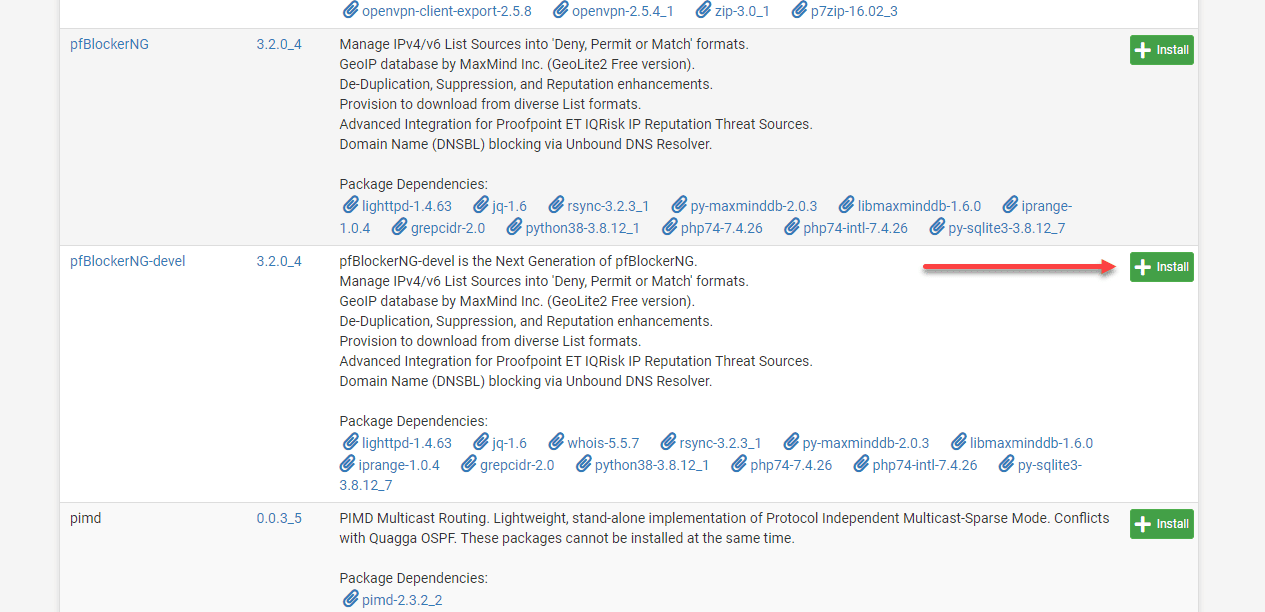
Navigate to “System” > “Package Manager” > “Available Packages”.
Locate “pfBlockerNG-devel” in the list and click the “+” button to install it.
Once installed, you will find the pfBlockerNG menu under “Firewall” in the top menu.
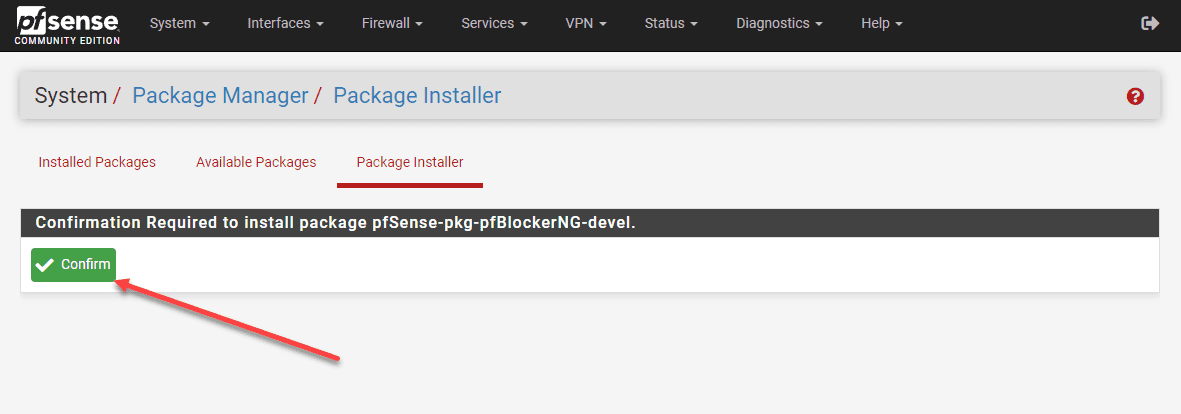
Confirm the installation of pfBlockerNG.
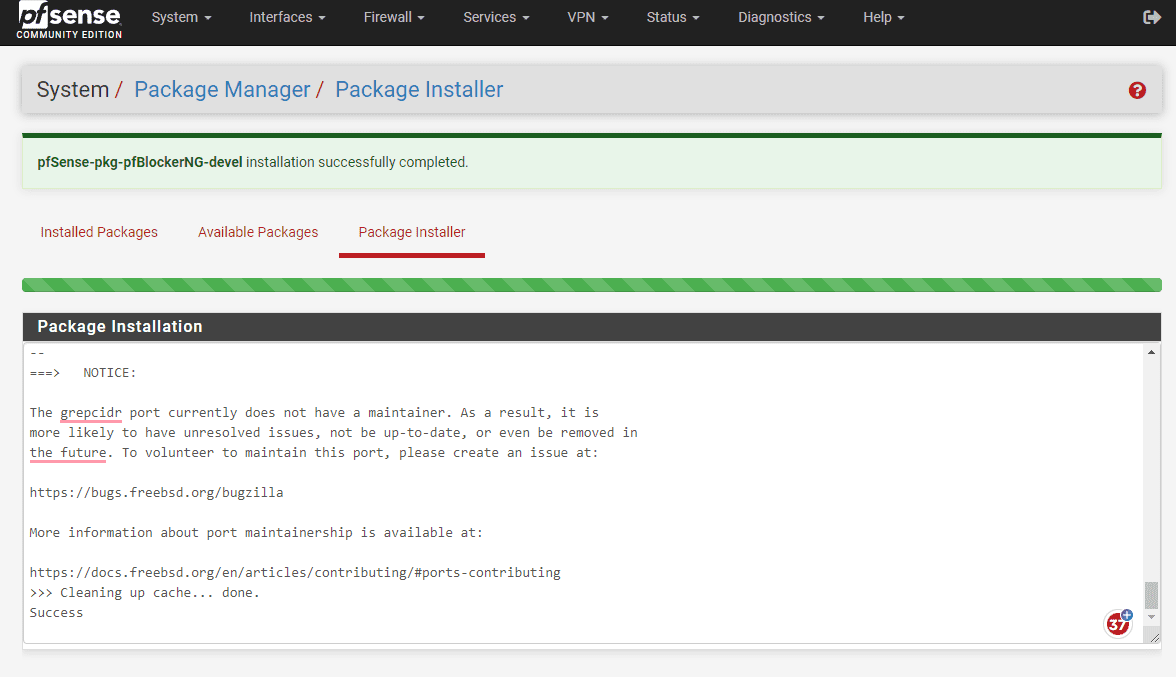
The installation begins, proceeds, and finishes.
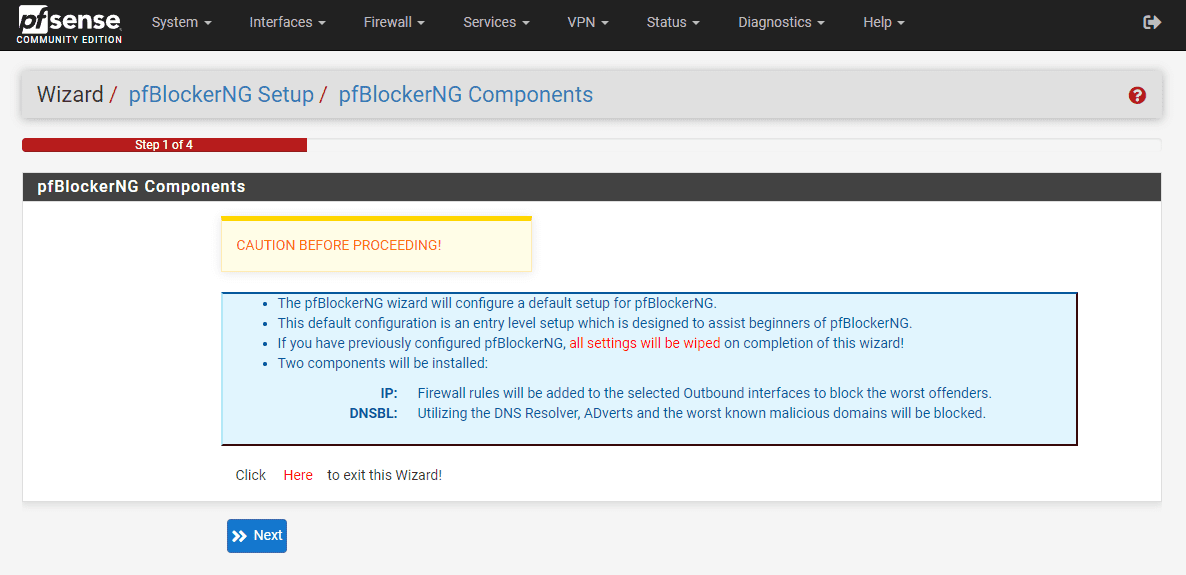
Running the pfBlockerng devel setup wizard
After you install the pfBlockerNG module and launch it, under Firewall > pfBlockerNG it will have you run through a setup wizard.
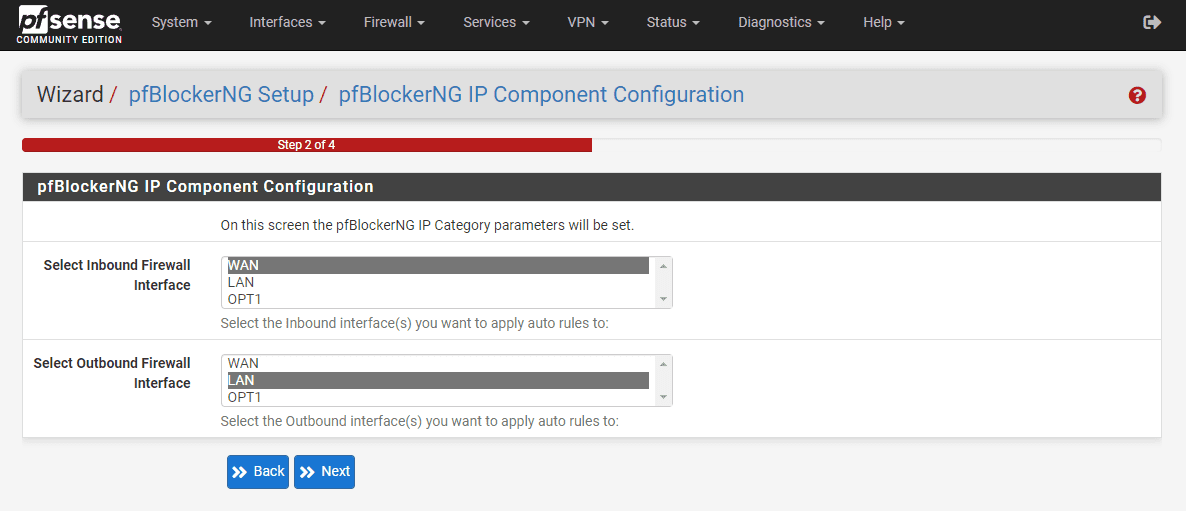
Configure the inbound and outbound interfaces.
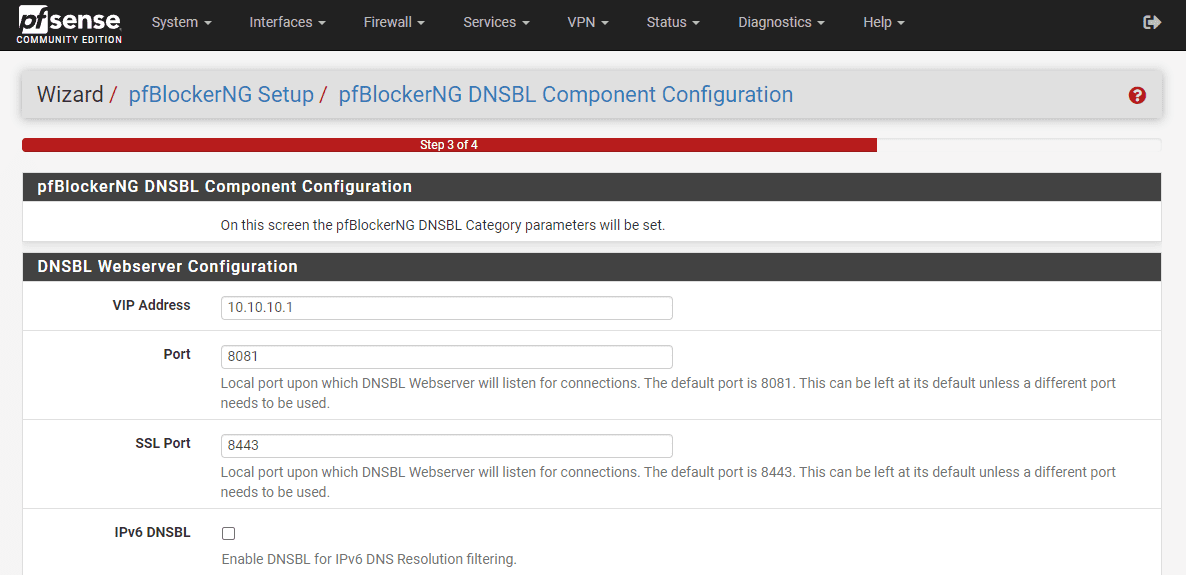
Configure the IP and port the pfBlockerNG module will listen on.
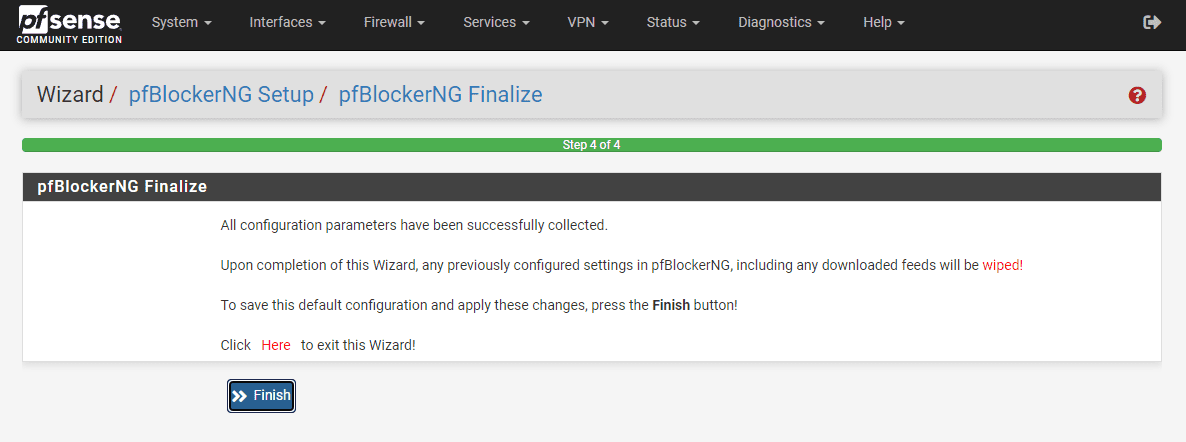
Finally, finish the configuration in pfBlockerNG.
The pfBlockerNG plugin downloads the latest updates to DNSBL lists, etc.
Google Safe Search VIP
Google offers a special DNS service called “SafeSearch VIP” that forces Safe Search for all Google search queries. To configure Google Safe Search VIP in pfSense, follow these steps:
Access your pfSense web interface and log in.
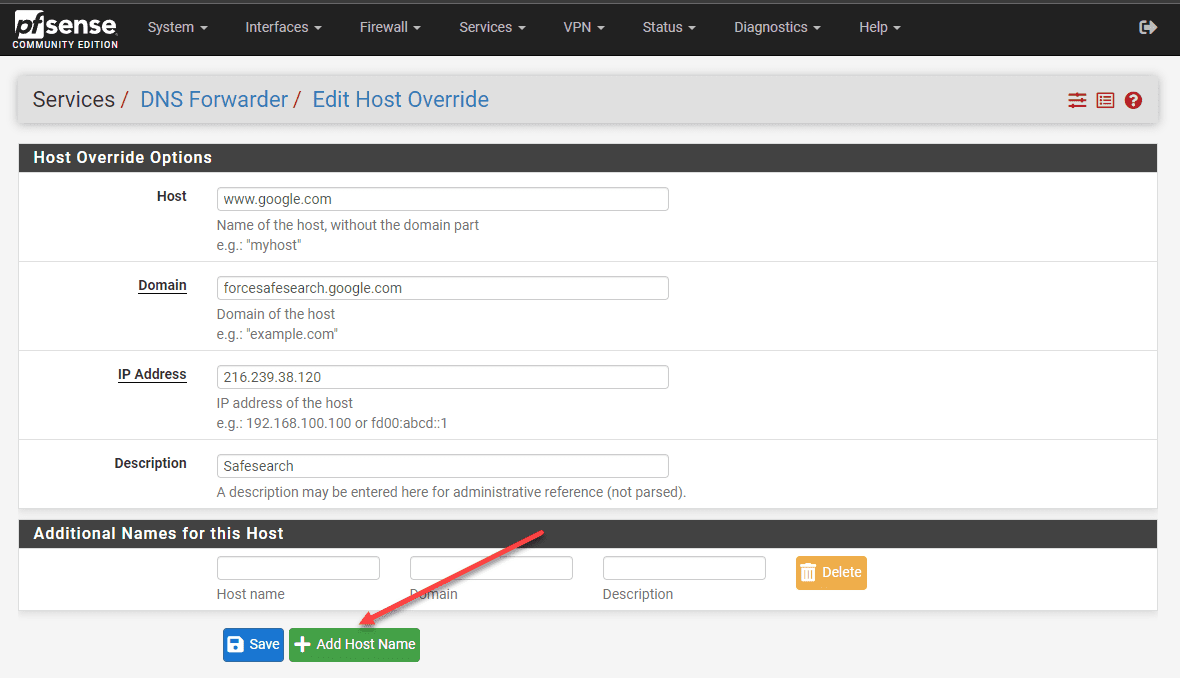
Navigate to “Services” > “DNS Forwarder” or “DNS Resolver”, depending on your setup.
In the “General Settings” tab, locate the “Host Overrides” or “Domain Overrides” section, depending on your setup.
Click the “+” button to add a new entry.
Enter the following details:
Host: www.google.com
Domain: forcesafesearch.google.com
IP Address: 216.239.38.120
Save the changes and apply the settings.
Repeat these steps for other Google domains, such as www.google.co.uk, www.google.ca, etc.
Configure DNS Forwarder or Resolver for Bing and YouTube
To force Safe Search on other search engines, such as Bing and YouTube, you will need to configure the DNS Forwarder or Resolver in pfSense. Follow these steps:
Access your pfSense web interface and log in.
Navigate to “Services” > “DNS Forwarder” or “DNS Resolver”, depending on your setup. 3. In the “General Settings” tab, locate the “Host Overrides” or “Domain Overrides” section, depending on your setup.
Click the “+” button to add a new entry for each search engine you want to force Safe Search on. For example:
Host: www.bing.com
Domain: strict.bing.com
IP Address: 204.79.197.220
Host: www.youtube.com
Domain: restrict.youtube.com
IP Address: 216.239.38.120
Save the changes and apply the settings.
Other plugins and ways to filter web traffic in pfSense
In addition to forcing Safe Search, pfSense offers other plugins and methods to filter and control web traffic on your network. Some of these options include:
URL filtering: pfSense can be configured to block specific URLs or entire domain categories using services such as SquidGuard or DNSBL (DNS Blacklist) within the pfBlockerNG plugin.
Content filtering: Plugins like Squid and SquidGuard can analyze and filter web content based on predefined rules, keywords, or categories, preventing access to inappropriate or harmful material.
VPN filtering: You can create firewall rules to block or restrict VPN access to certain websites or services, preventing users from bypassing content filtering.
Application control: Using the Snort or Suricata plugins, you can monitor and control specific applications or protocols on your network, ensuring that only authorized traffic is allowed.
Implementing Firewall Rules to Enhance Content Filtering
Aside from configuring Safe Search and utilizing plugins, you can also create firewall rules in pfSense to further enhance content filtering and control web traffic. These rules can block or restrict access to specific IP addresses, ports, or protocols, giving you more granular control over your network’s security. To create firewall rules in pfSense, follow these steps:
Access your pfSense web interface and log in.
Navigate to “Firewall” > “Rules” in the top menu.
Choose the interface (e.g., LAN) where you want to apply the rule.
Click the “+” button to add a new rule.
Specify the action (pass, block, or reject), protocol, source, destination, and other settings according to your content filtering requirements.
Add a description for the rule to help you remember its purpose.
Save the changes and apply the settings.
Monitoring and Logging for Improved Network Security
Monitoring and logging are essential aspects of maintaining a secure and well-functioning network. With pfSense, you have access to various tools and features that enable you to closely monitor network activity, detect potential issues, and troubleshoot problems. Some key monitoring and logging features in pfSense include:
Dashboard: The pfSense dashboard provides a real-time overview of your network’s status, including system information, interface statistics, and service statuses. It also allows you to customize and add widgets to access essential data quickly.
System Logs: pfSense keeps detailed logs of various system events, such as firewall actions, DNS queries, and VPN connections. These logs can be accessed via the “Status” > “System Logs” menu and can help you identify security issues or other network problems.
Traffic Graphs: The “Status” > “Traffic Graph” menu in pfSense displays real-time graphs of network traffic, making it easy to visualize data flow and detect unusual activity.
Reporting: pfSense offers several reporting tools, such as RRD Graphs and Insight, which allow you to analyze historical network data and identify trends or anomalies.
Editing Local Unbound Configuration Files for Safe Search
In some cases, you might want to edit the local configuration files for Unbound, the DNS resolver used by pfSense, to enforce Safe Search settings manually. One such file you can create and edit is /var/unbound/google.conf. This file can contain custom settings for forcing Safe Search on various Google domains. To edit or create the google.conf file, follow these steps:
Access your pfSense firewall using an SSH client, such as PuTTY, or access the command prompt directly through the pfSense web interface by navigating to “Diagnostics” > “Command Prompt.”
Type the following command to create or open the google.conf file in the vi text editor:
vi /var/unbound/google.confPress the “i” key to enter insert mode, allowing you to edit the file.
Add the following lines to the file, which will redirect Google search queries to the SafeSearch VIP addresses:
local-zone: "www.google.com" redirect local-data: "www.google.com 30 IN A 216.239.38.120"Repeat these lines for other Google domains, such as www.google.co.uk, www.google.ca, etc., accordingly replacing the domain in the local-zone and local-data lines.
Once you’ve added the necessary entries, press the “Esc” key to exit insert mode.
Type :wq and press “Enter” to save your changes and exit the vi text editor.
To apply the changes, restart the Unbound DNS resolver service by running the following command:
service unbound restartCreating and editing the /var/unbound/google.conf file allows you to manually enforce Safe Search on specific Google domains, ensuring that explicit content is filtered from search results. This method provides a more hands-on approach to configuring Safe Search settings in pfSense, giving you direct control over the DNS resolver’s behavior.
Wrapping up
The pfSense open-source firewall is a great solution with enterprise features and the control needed to protect users on the LAN from mature, explicit, and other types of inappropriate content. The pfBlockerNG module is free to download and install in the already free pfSense firewall, making the entire solution powerful and cost-effective.


0 Comments