Windows Remote Management (WinRM) is an essential tool for administrators when managing remote servers in a lab or production environment. However, occasionally, you might encounter the following error message: WinRM negotiate authentication error. This blog post will guide you through fixing this error, ensuring seamless server management.
Understanding the WinRM Service
The Windows Remote Management (WinRM) service is a key component of Microsoft’s WS-Management Protocol implementation, allowing administrators to manage and interact with remote computers and servers. This section will delve into the WinRM service, its features, and its role in remote server management.
Learn more about WinRM from Microsoft here: Installation and configuration for Windows Remote Management – Win32 apps | Microsoft Learn.
Features and Functionality of WinRM Service
The WinRM service offers several features and functionalities to enhance the remote management experience for administrators:
Remote Command Execution: WinRM enables administrators to execute PowerShell commands and scripts on remote servers without the need for direct access to the machines. This feature is particularly useful in large-scale environments where managing numerous servers would be cumbersome without remote capabilities.
Configuration Management: The WinRM service facilitates the remote management of server configurations, such as modifying settings, enabling or disabling features, and more. Administrators can use WinRM to configure servers according to organizational policies and requirements.
Access to Event Logs and Performance Data: WinRM allows administrators to access event logs, performance data, and other information from remote servers, aiding in troubleshooting and monitoring efforts.
Security: WinRM employs various security measures to ensure secure communication between the client and server. This includes encryption, authentication mechanisms like Kerberos, and role-based access control to restrict unauthorized access.
Possible authentication mechanisms
Basic Authentication
Digest Authentication
Negotiate Authentication
Kerberos Authentication
Client Certificate-based Authentication
How WinRM Service Operates
The WinRM service operates by creating “listeners” on the remote server, which are responsible for processing incoming management requests from client computers. These listeners can be configured to use different transport protocols (HTTP or HTTPS) and various authentication mechanisms (Kerberos, NTLM, or Basic).
To enable and configure the WinRM service on a remote server, administrators can use the “winrm” command-line tool or the PowerShell “Enable-PSRemoting” cmdlet. These tools help set up the necessary listeners, configure firewall rules, and modify other settings as needed.
Once the WinRM service is enabled and configured, administrators can use tools like PowerShell, Server Manager, or other remote management utilities to manage the remote server through WinRM.
Understanding WinRM and Negotiate Authentication
WinRM is a powerful feature in Windows Server that allows administrators to manage and configure servers remotely. It operates over HTTP or HTTPS and uses the WS-Management protocol for communication. One of the key aspects of WinRM is its support for various authentication mechanisms, including Kerberos, NTLM, and Negotiate.
Negotiate authentication is a mechanism that enables clients to use either Kerberos or NTLM for authentication, depending on the server and client configurations. While it is convenient, it can sometimes cause errors, particularly when clients and servers are not correctly configured.
Best Practices for Using WinRM Service
When using the WinRM service for remote server management, consider the following best practices:
Always use encrypted communication (HTTPS) to protect sensitive data during transit.
Employ strong authentication mechanisms like Kerberos to reduce the risk of unauthorized access.
Regularly update and patch the WinRM service and other system components to mitigate potential security vulnerabilities.
Configure role-based access control and restrict remote management permissions to authorized personnel only.
Common Causes of WinRM Negotiate Authentication Error Message
There are several possible reasons for a WinRM negotiate authentication error to occur when you add remote destination computers for management. Some of the most common causes include:
Verify that the remote server’s DNS settings are configured correctly. Ensure the DNS server is reachable and can resolve the remote server’s hostname.
Check the remote server’s time synchronization. Time discrepancies between the client and server can cause Kerberos authentication failures. Synchronize both machines with a reliable time source to resolve this issue.
Examine the remote server’s Service Principal Name (SPN) configuration. Incorrect or duplicate SPNs can result in Kerberos authentication issues. Use the “setspn” command-line tool to view and modify SPN settings as needed.
Review the Event Viewer logs on the client and server for any related error messages or event IDs. These logs can provide valuable insight into the root cause of the negotiate authentication error.
If the error is related to Kerberos authentication, consider temporarily switching to NTLM or Basic authentication for troubleshooting purposes. Remember that these methods are less secure and should be reverted to Kerberos once the issue is resolved.
Ensure the remote server credentials are correct when you store remote server credentials
Understanding these causes is crucial to troubleshooting and resolve the error effectively.
Fixing WinRM Negotiate Authentication Error Message
Before attempting to fix the error, it’s important to verify that both the client and server have the necessary configurations in place. Additionally, ensure that the client computer and remote server are on the same subnet and domain, as this can affect the authentication process.
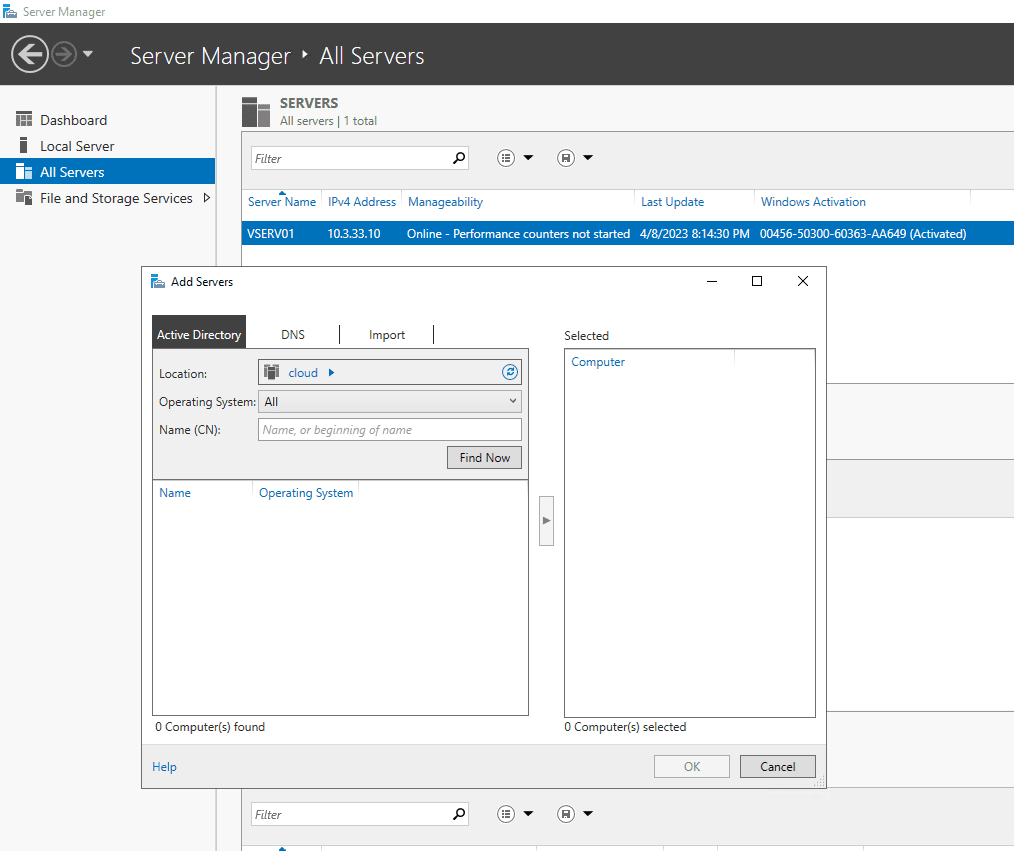
Verifying Server Manager Configuration
The Server Manager in Windows Server is a crucial component for managing remote servers. To check the configuration, follow these steps:
Open Server Manager on your WinRM client computer.
Navigate to the “All Servers” section.
Add the remote server you’re trying to connect to.
Ensure that the server is correctly configured for remote management.
If you encounter any issues with the server configuration or authentication mechanisms reported, consult the relevant documentation or seek assistance from an expert in Windows Server management.
Checking DNS Server Configuration
DNS server configuration ensures clients can properly resolve the remote server’s hostname. To verify the DNS server settings, follow these steps:
Open the DNS Manager on your client’s computer.
Locate the DNS server responsible for resolving the remote server’s hostname.
Ensure the DNS server has the correct records and configuration for the remote server.
If the DNS server configuration is incorrect, update the settings and try connecting to the remote server again.
Configuring WinRM Negotiate Authentication
In some cases, the WinRM negotiate authentication error may be caused by a mismatch between the authentication mechanisms on the client and server. To configure WinRM negotiate authentication, follow these steps:
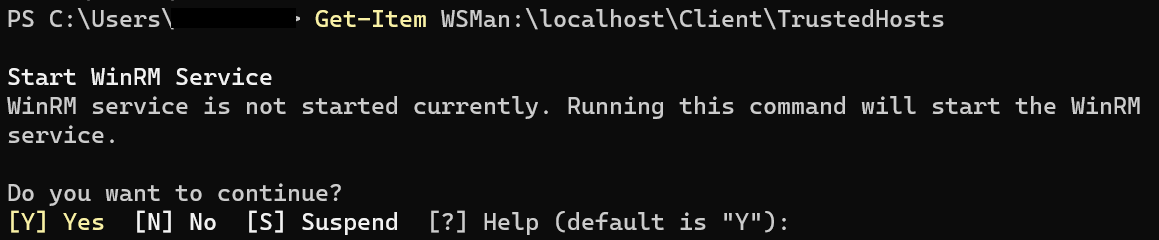
Open a privileged PowerShell session on the client computer.
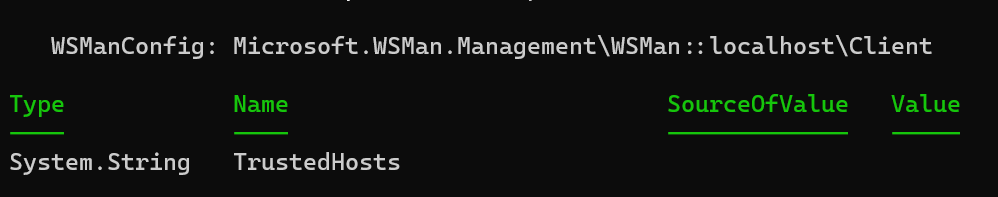
Run the following command to view the current WinRM configuration:
Get-Item WSMan:localhostClientTrustedHostsIf the remote server is not listed in the trusted hosts, add it by running the following command:
Set-Item WSMan:localhostClientTrustedHosts -Value "RemoteServerName"Replace “RemoteServerName” with the hostname or IP address of the remote server.
Verify that the authentication mechanisms on the client and server are compatible. In some cases, it might be necessary to enable basic authentication or disable the negotiate authentication mechanism.
Set-Item WSMan:localhostClientAuthBasic -Value $trueResolving Credential Delegation and Windows Firewall Concerns
If the WinRM negotiate authentication error stems from credential delegation or Windows Firewall, perform the following steps to address the issue:
On the client computer, open the Group Policy Management Console (GPMC).
Navigate to this path:
Computer Configuration > Administrative Templates > System > Credentials DelegationEnable the “Allow delegating fresh credentials” policy and include the remote server in the list of servers authorized to receive delegated credentials.
If the problem is related to Windows Firewall, ensure the ports are open and that the firewall settings permit WinRM traffic.
Addressing Hyper-V Server and Workgroup Scenarios
In some instances, the WinRM negotiate authentication error may arise while managing Hyper-V servers or servers in a workgroup environment. In these situations, follow these supplementary steps:
Confirm that the client computer and remote server are either domain-joined or part of the same workgroup.
If the remote server is a Hyper-V host, verify that the required components and configurations are in place for remote management.
Update the TrustedHosts list in the WinRM configuration to include the remote server, as outlined in the “Adjusting WinRM Negotiate Authentication Settings” section above.
Additional Troubleshooting Recommendations
If the WinRM negotiate authentication error continues to persist despite following the steps mentioned above, consider these further troubleshooting recommendations:
Inspect the Windows Event Log on both the client computer and remote server for pertinent error messages or event IDs.
If you have an error related to WinRM, make a note of this.
You can often find other blog posts or online resources of ones who have encountered similar error messages.
WinRM connectivity to the destination computer and configuration problems can also lead to negotiate authentication errors. To identify and address these issues, follow the steps below:
Test WinRM connectivity between the client and remote server using the “Test-WSMan” PowerShell cmdlet. This command can help identify if there are any communication issues between the machines.
Test-WSMan -ComputerName RemoteServerName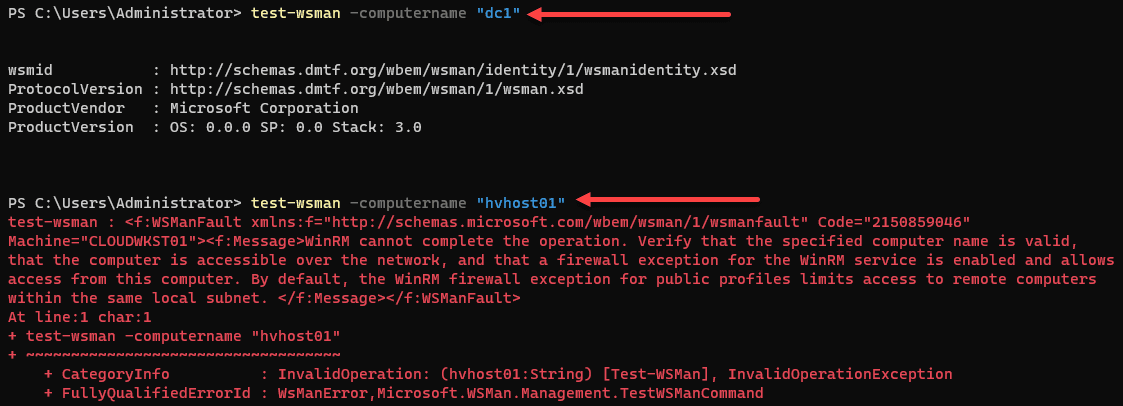
Replace “RemoteServerName” with the remote server’s actual hostname or IP address.
Review the WinRM configuration on both the client and server. Ensure the listener settings, authentication mechanisms, and other configuration options are correctly set up. Use the “winrm get winrm/config” command to view the current configuration.
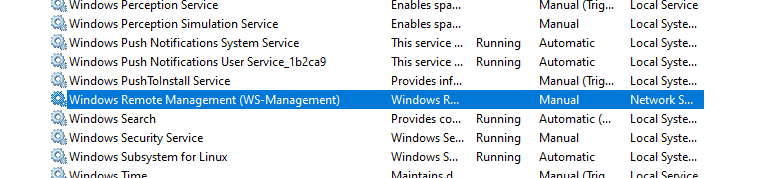
Ensure that the required WinRM services run on the client and server. The “WinRM” and “Windows Remote Management (WS-Management)” services should be set to start automatically and be running without any issues.
Verify that the appropriate firewall rules are in place to allow WinRM traffic. In some cases, restrictive firewall settings can prevent successful communication between the client and server.
Check the Disallow Negotiate authentication policy setting
This policy setting allows you to manage whether the Windows Remote Management (WinRM) client uses Negotiate authentication.
Navigate to Regedit > HKLM\SoftwarePolicies\Microsoft\Windows\WinRM\Client
DWORD > AllowNegotiate > 1
The WinRM client does not use Negotiate authentication if you enable this policy setting.
If you disable or do not configure this policy setting, the WinRM client uses Negotiate authentication.
Wrapping up
While WinRM negotiate authentication errors can be difficult to figure out, using a systematic approach and careful troubleshooting can help resolve the issue and allow you to continue managing your remote servers effectively. Following the steps in this guide, you can address the WinRM negotiate authentication error, and continue to use WinRM to manage and monitor your environment.


0 Comments