
Netstat is a vital command-line tool utilized by network professionals, system administrators, and those keen to understand their network’s inner workings in Windows or Unix listening ports. It provides insights into network connections, protocols, and network statistics. Let’s dive into the netstat tool with the top 7 netstat commands essential for diagnosing network problems, monitoring connections, etc.
Netstat installation
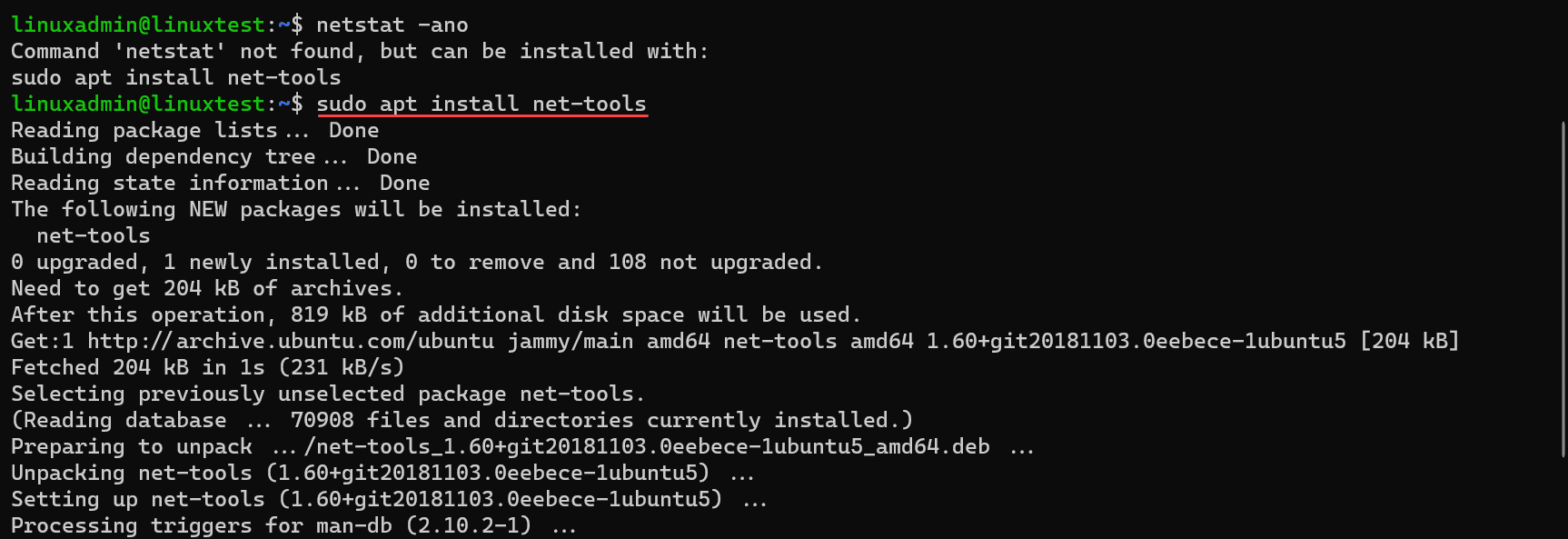
In Windows, you will find that netstat is part of the operating system. There is no need to install netstat to access it from either the command or PowerShell prompt. In Linux, you may need to install the net-tools package.
Below is a look at installing net-tools in Windows Subsystem for Linux (WSL) in Ubuntu 22.04.
sudo apt install net-toolsOverview of the Top 7 Netstat Command examples
netstat -a: Displays all connections and listening ports.
netstat -n: Shows addresses and port numbers in numerical form.
netstat -t: Displays active TCP connections.
netstat -i: Provides detailed statistics by protocol, including interface statistics.
netstat -r: Shows the kernel interface table and IP routing table.
netstat -e: Displays extended network statistics, including foreign addresses.
netstat -p: Reveals information specific to protocols such as TCP, UDP, or ICMP.
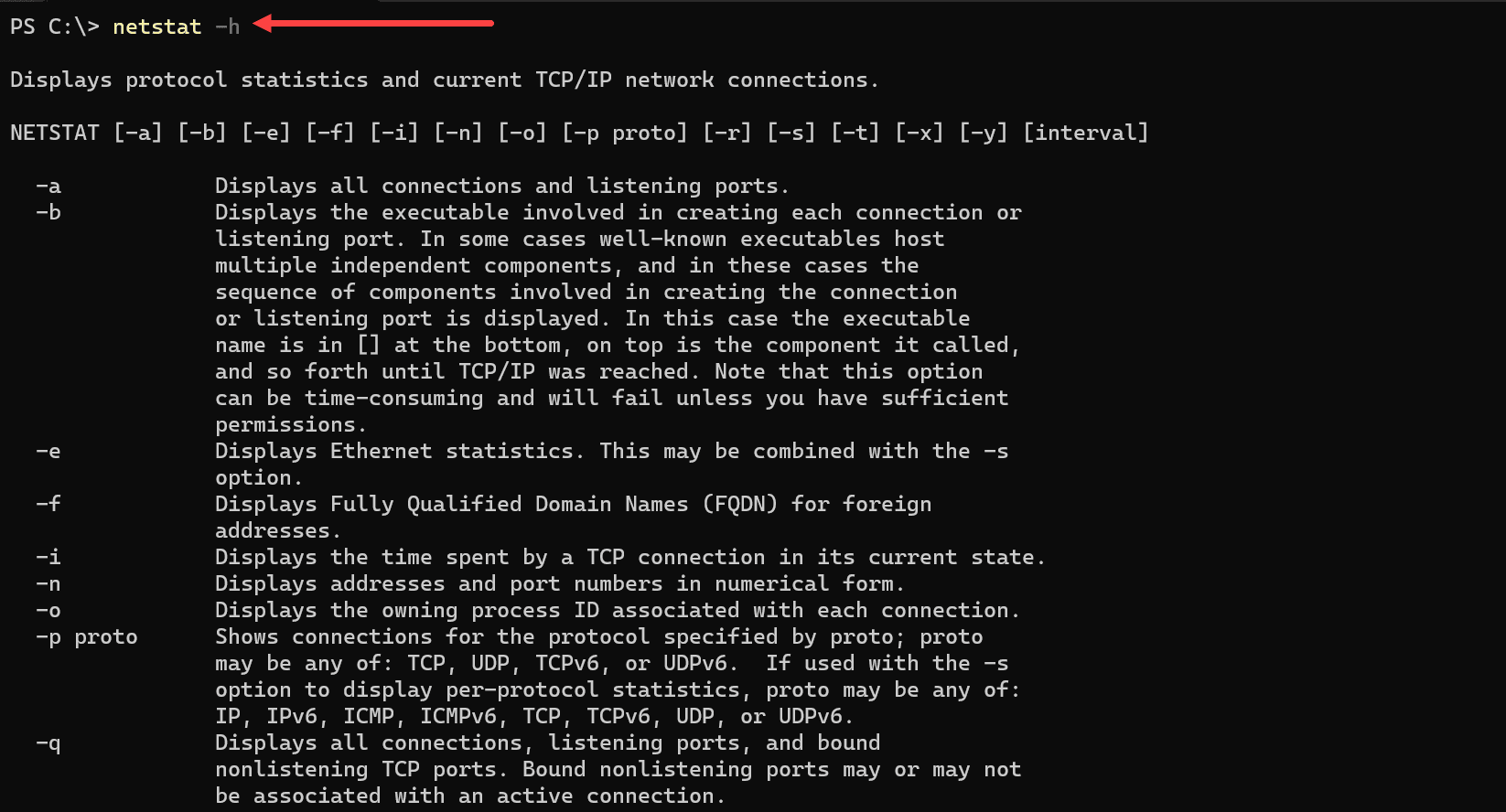
You can view all the netstat command options with the command:
netstat -h1. The netstat -a Command: All Connections and Listening Ports
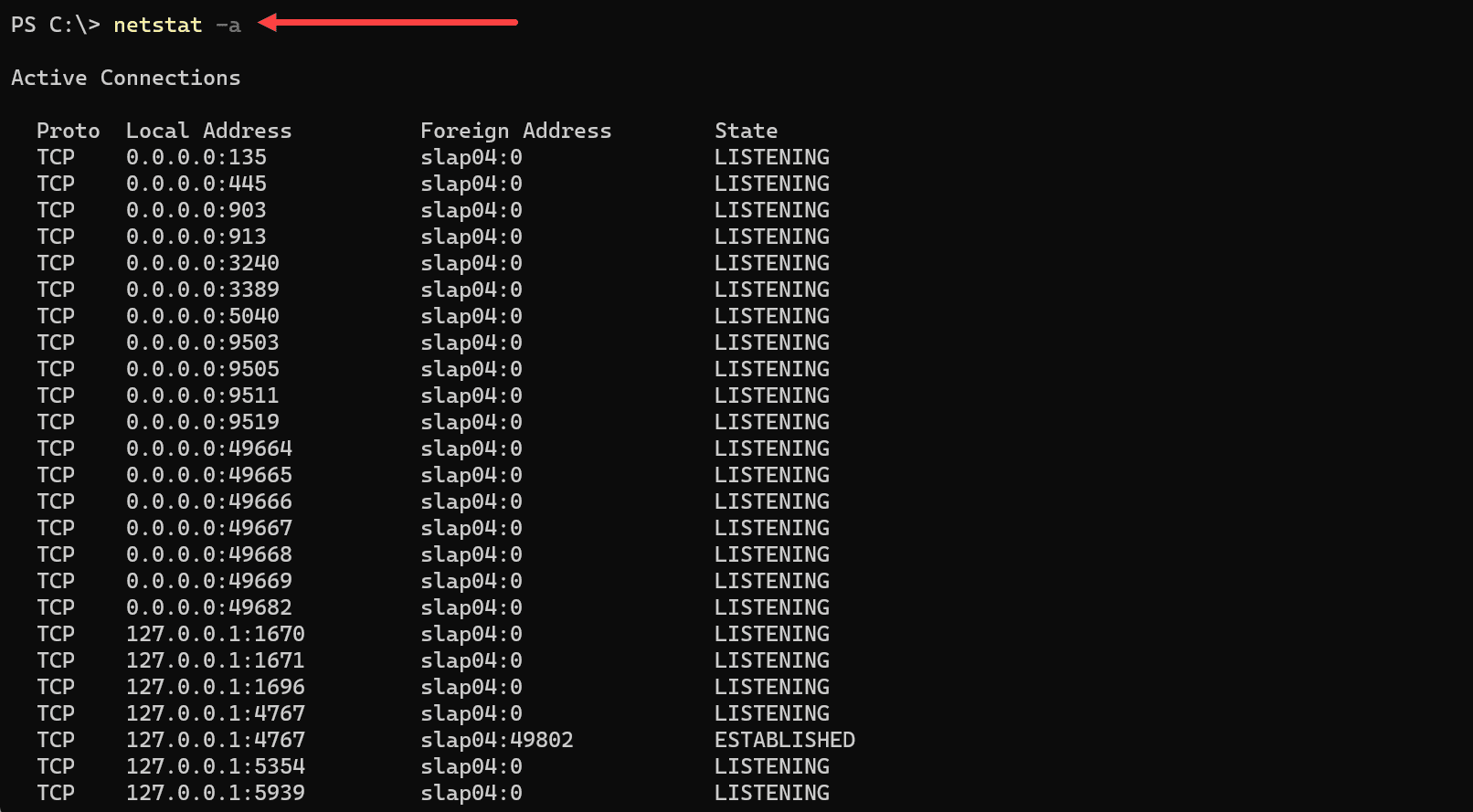
The netstat -a command is a fundamental and powerful tool within the netstat command suite. It allows users to view all active connections and listening ports on a system, displaying information for TCP, UDP, and other IP protocols.
Displaying All Connections and Listening Ports
Executing the netstat -a command displays a comprehensive list of all connections and ports on the system that are currently in listening state or established connections.
Syntax
netstat -aOutput
The output will provide several key pieces of information:
Protocol: This will show whether the connection is TCP, UDP, or another protocol.
Local Address: The local address and port number of the connection.
Foreign Address: The external IP address and port number that the local address is connected to.
State: The current state of the connection (e.g., ESTABLISHED, LISTENING).
Use Cases
Monitoring Network Connections: Network administrators and users can keep tabs on all active connections and listening ports.
Troubleshooting Network Problems: By revealing the listening state, established connections, and more, the command aids in diagnosing network issues.
Security Assessments: Identifying unexpected or suspicious connections can be essential in security evaluations.
Example Usage
Displaying All Connections
Simply run the following command to display all connections and listening ports:
netstat -aCombining with Other Options
The -a option can be combined with other netstat options for more specific information.
Display Numerical Addresses: Combine with -n to display numerical IP addresses:
netstat -anFilter by Protocol: Use with -p to filter by TCP or UDP:
netstat -a -p TCP netstat -a -p UDP2. The netstat -n Command: Numerical Form Addresses
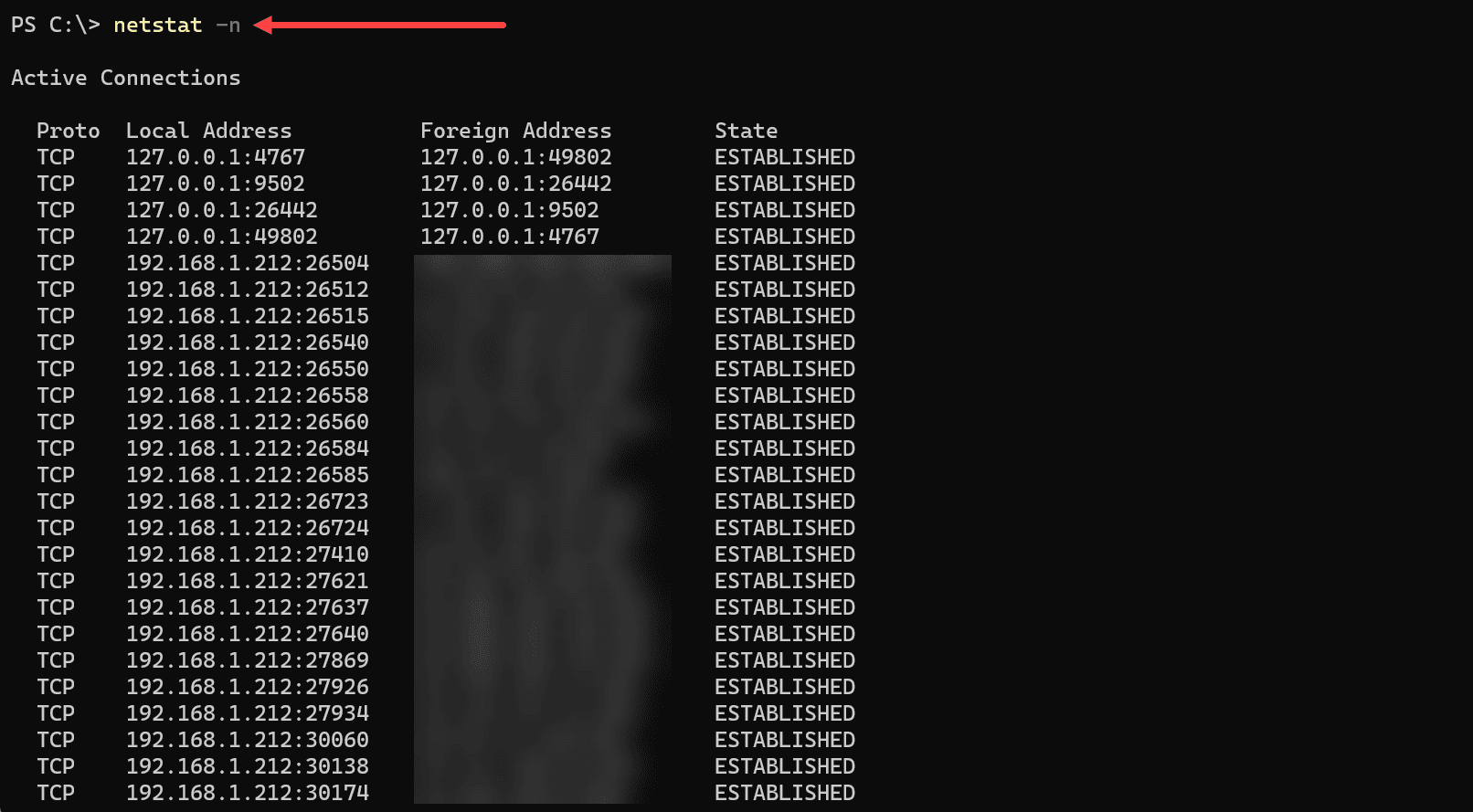
The netstat -n command is used to display active connections, listening ports, and network statistics but presents all addresses in numerical form. Instead of showing hostnames, it will display IP addresses, providing a more direct and often faster view of network connections.
Displaying Addresses and Ports Numerically
Executing the netstat -n command will reveal the same information as other netstat commands, but all addresses will be in numerical form.
Syntax
netstat -nOutput
The key details in the output will include:
Protocol: TCP, UDP, or other IP protocols.
Local Address: The numerical IP address and port number for the local connection.
Foreign Address: The numerical IP address and port number for the remote or foreign connection.
State: The current state of the connection (if applicable), such as ESTABLISHED for TCP.
Use Cases
Quick Lookups: The -n option often returns results more quickly because it doesn’t resolve hostnames.
Analyzing Connections: For those working directly with IP addresses and port numbers, this numerical view can be more useful.
Troubleshooting: By displaying numerical IP addresses, it may facilitate the identification of specific network problems.
Example Usage
Displaying Numerical Information
To view all connections and listening ports numerically, you can execute:
netstat -nCombining with Other Options
The -n option is often combined with other netstat commands to refine the output.
Display TCP Connections Numerically: Combine with -t:
netstat -ntShow All Connections Numerically: Combine with -a:
netstat -naShow TCP and UDP Ports Numerically: Combine both -t and -u:
netstat -ntu3. The netstat -t Command: Active TCP Connections
The netstat -t command is specifically designed to display active TCP connections. It narrows down the information to only TCP protocol-related connections and statistics, making it a valuable tool for focusing on TCP traffic.
Displaying Active TCP Connections
Executing the netstat -t command will filter the output to show only TCP connections, both established and those waiting to be established.
Syntax
netstat -t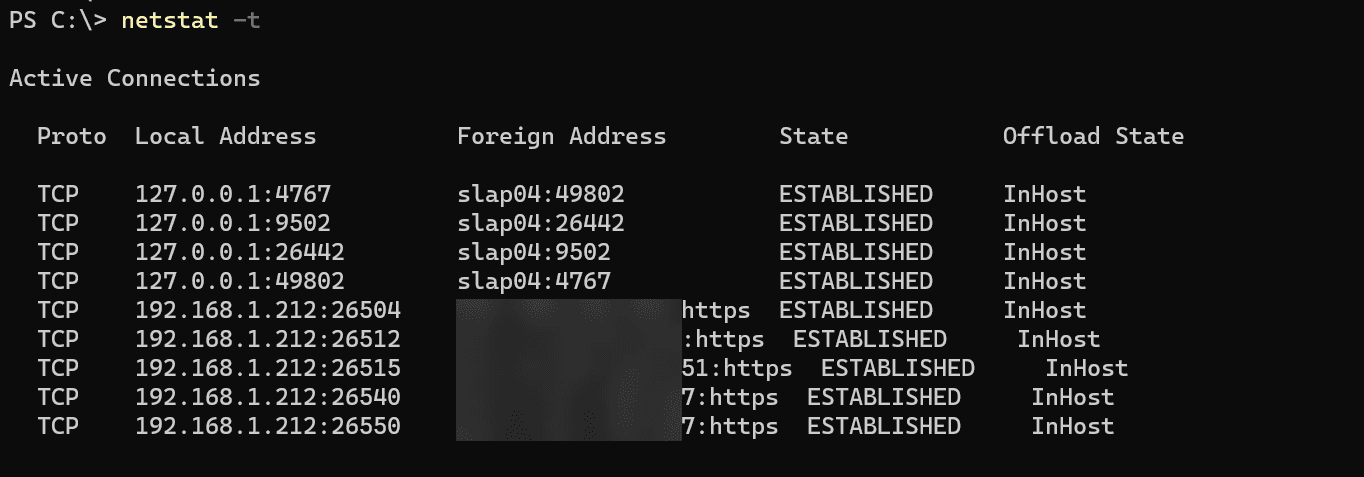
Output
The output will include the following details:
Protocol: This will always be TCP since the command filters only TCP connections.
Local Address: The local IP address and port number.
Foreign Address: The remote IP address and port number connected to the local address.
State: The current state of the TCP connection (e.g., ESTABLISHED, LISTENING, SYN_SENT).
Use Cases
TCP Traffic Monitoring: The command allows system administrators and users to focus on TCP connections, one of the core transport protocols on the Internet.
Diagnosing TCP Connection Issues: For troubleshooting specific TCP connections, this command can provide insights.
Security Analysis: Understanding active TCP connections can be essential in identifying suspicious or unexpected network behavior.
Example Usage
Displaying TCP Connections
To see all active TCP connections, run:
netstat -tCombining with Other Options
The -t option can be paired with other netstat options for more refined results.
Display Numerical Addresses: Combine with -n to display numerical IP addresses and port numbers:
netstat -tnShow Listening TCP Ports: To view listening TCP ports, combine with -a:
netstat -ta4. The netstat -i Command: Statistics by Protocol
The netstat -i command is utilized to display statistics for the network interfaces available on the system. This command provides an overview of how network interfaces are operating, including details like the number of packets received and sent.
Displaying Network Interface Statistics
When the netstat -i command is executed, it displays a summary of statistics for each network interface.
Syntax
netstat -i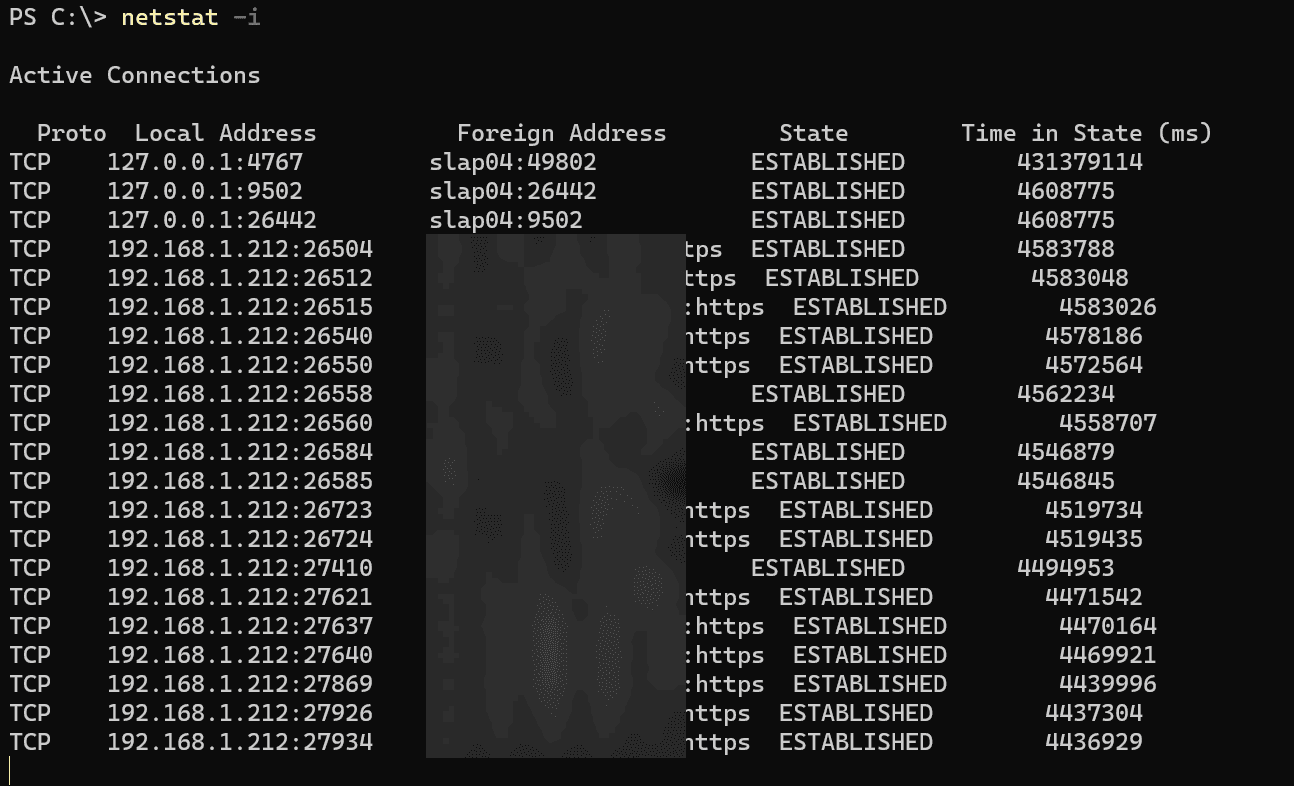
Output
The output typically includes the following information:
Interface Name: The name of the network interface.
MTU: Maximum Transmission Unit size.
RX Packets: Number of packets received.
TX Packets: Number of packets transmitted.
Errors: Number of errors while receiving or transmitting.
Collisions: Number of packet collisions detected.
RX Bytes: Number of bytes received.
TX Bytes: Number of bytes transmitted.
Use Cases
Monitoring Interface Performance: This command offers a snapshot of how the network interfaces are performing, helping in identifying issues or assessing efficiency.
Troubleshooting: Useful for diagnosing problems with specific network interfaces.
Capacity Planning: By analyzing network load and performance, it can aid in planning future network capacity needs.
Example Usage
Displaying Basic Interface Statistics
To see basic statistics for all network interfaces, simply run:
netstat -iExtended Information
Some systems allow additional options to get more details:
Displaying Extended Information: On Unix systems, you might use:
netstat -ieShowing Statistics for a Specific Interface: If you want details for a particular network interface, you might use:
netstat -I eth05. The netstat -r Command: Kernel Interface and IP Routing Table
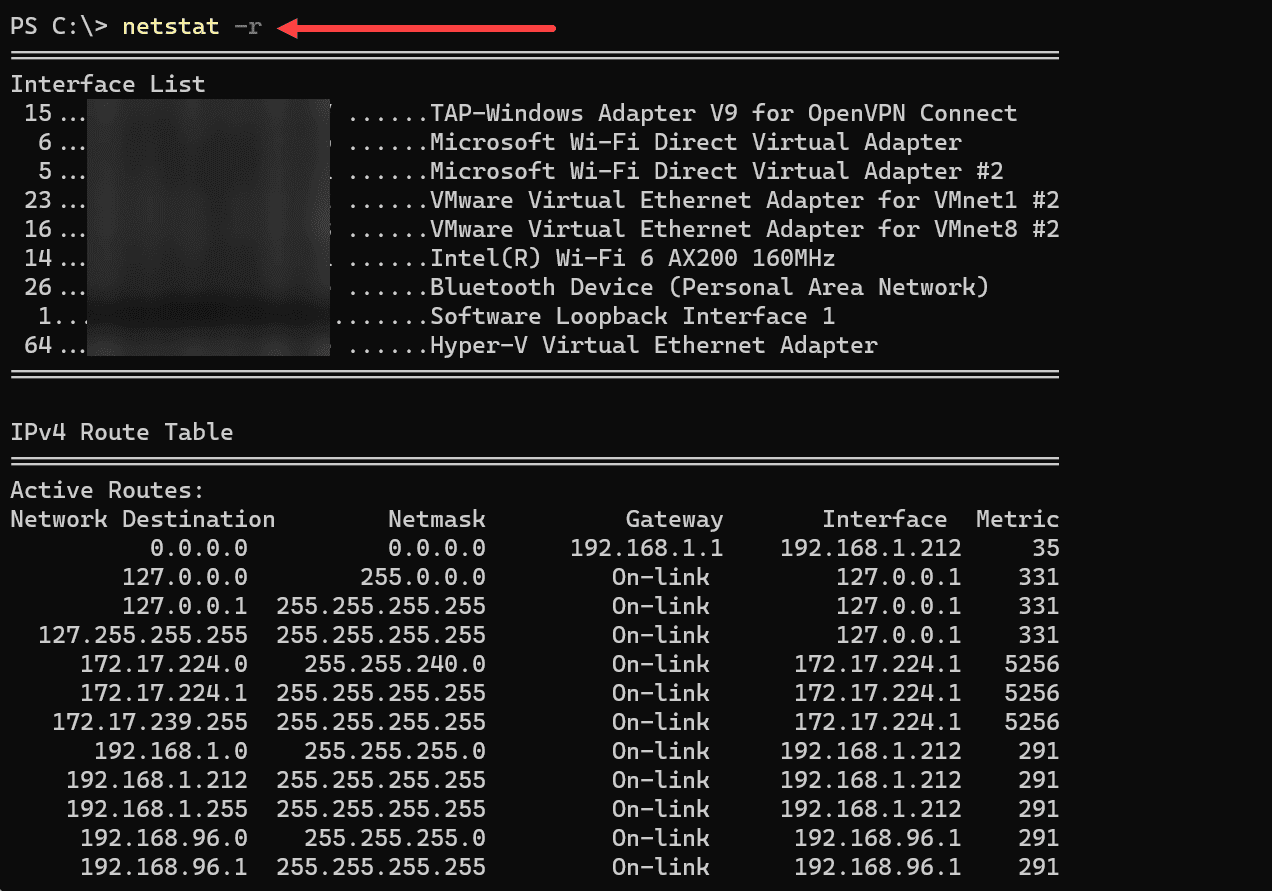
The netstat -r command provides a way to view the routing tables of the system from the command prompt in Windows. Routing tables are essential in determining where and how data packets are directed through the network. The routing table can be crucial for network configuration, troubleshooting, and optimization.
Displaying the Routing Table
Executing the netstat -r command will provide an overview of the routing table, including essential details about the available routes. The output is similar to what you find with the route print command.
Syntax
netstat -rOutput
The typical output will display the following information:
Destination: The destination network or host.
Gateway: The gateway or next hop to reach the destination.
Genmask: The netmask associated with the destination.
Flags: Various flags indicating specific route characteristics (e.g., U for Up, G for Gateway).
Use: A count of the number of lookups for the route.
Interface: The network interface used for the route.
Use Cases
Understanding Network Routing: This command provides insights into how the system routes packets, helping in network planning and optimization.
Troubleshooting Network Issues: If there are connectivity problems, viewing the routing table can help diagnose misconfigurations or failures.
Security Assessments: By analyzing the routing table, potential security vulnerabilities related to routing can be identified.
Example Usage
Displaying the Routing Table
To view the system’s routing table, you can run:
netstat -rCombining with Other Options
The -r option can be paired with other netstat options for specific requirements.
Displaying Numerical Addresses: Combine with -n to display numerical IP addresses and avoid resolving hostnames:
netstat -rnShow Kernel Routing Table: On Unix systems, this option may be available to show the kernel’s interface table:
netstat -r -e6. The netstat -e Command: Extended Network Statistics
The netstat -e command is used to display detailed statistics about the Ethernet or network adapter’s performance on a system. This information can be pivotal for network monitoring, troubleshooting, and optimization, providing a snapshot of the network interface’s status and activities.
Displaying Ethernet Statistics
When you execute the netstat -e command, it reveals comprehensive statistics about the Ethernet connections on the machine.
Syntax
netstat -e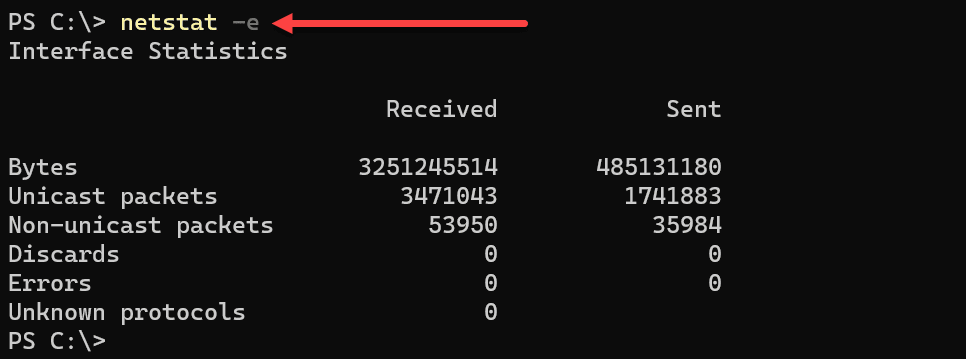
Output
The typical output will include:
Bytes: The total number of bytes sent and received.
Unicast Packets: The number of unicast packets sent and received.
Non-Unicast Packets: The number of non-unicast packets sent and received.
Discards: The number of packets that were discarded.
Errors: The number of errors that occur while sending or receiving packets.
Unknown Protocols: Count of received packets with unknown protocols.
Use Cases
Monitoring Network Performance: By providing detailed Ethernet statistics, this command helps in monitoring network performance.
Diagnosing Issues: If there are problems with the network adapter or Ethernet connections, these statistics can assist in pinpointing the issue.
Security Analysis: Unusual patterns in the statistics could indicate security threats or unauthorized activities.
Example Usage
Displaying Basic Ethernet Statistics
To view essential statistics about the Ethernet connections, simply run:
netstat -eCombining with Other Options
The -e option can be combined with other netstat options to tailor the output to specific needs.
Displaying Both Interface and Routing Tables: Combine with -r:
netstat -e -rDisplaying Numerical Form of Addresses: Combine with -n:
netstat -e -n7. The netstat -p Command: Protocol-Specific Information
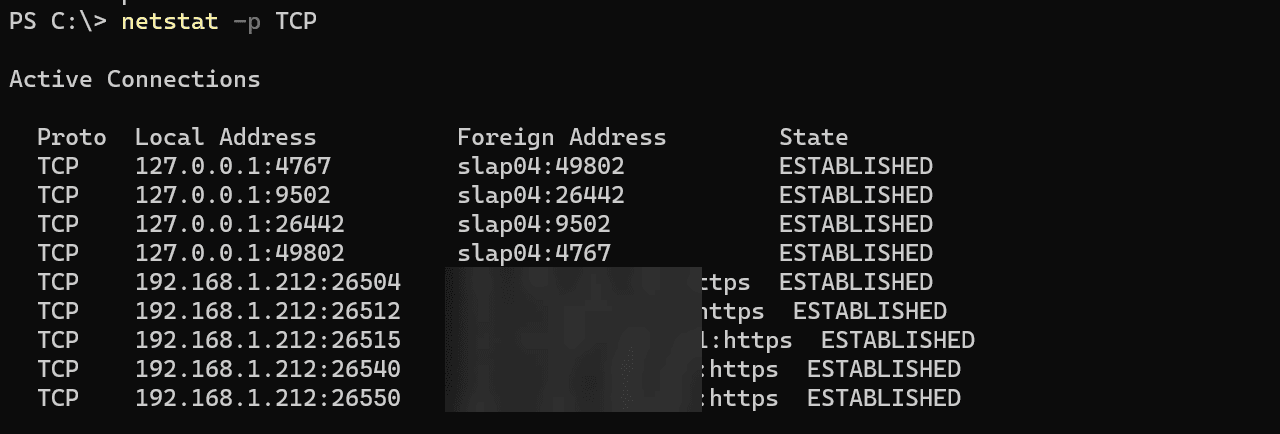
The netstat -p TCP command filters and displays only TCP protocol-related statistics and connections.
Example Usage
To display TCP protocol details, execute the following command:
netstat -p TCPYou’ll see a list of active TCP connections, port numbers, IP addresses, and the TCP connection state (such as ESTABLISHED).
The netstat -p UDP Command: UDP Protocol Specifics
Using the netstat -p UDP command focuses on UDP connections, showing statistics and details related only to the UDP protocol.
Example Usage
To display UDP protocol details, run the following command:
netstat -p UDPThis command will list all active UDP ports, the local address, and foreign address associated with each UDP connection, and other related information.
Using the -p option with TCP or UDP as an argument, you can narrow down the information to the specific protocol, which is valuable for monitoring, troubleshooting, or understanding how these protocols function within your network.
Wrapping up
The top 7 netstat commands described in this post basic commands for anyone dealing with network connections, whether on a Windows server, a Unix system, or any platform supporting netstat. Understanding the options included with netstat and using these effectively, will help admins, and network professionals have a leg up on troubleshooting and diagnosing network connectivity issues.


0 Comments