
You can do many cool things with Kali Linux, including testing the security of a wireless network. This post will look at airmon-ng VMware Kali VM configuration and what you can do with airmon-ng and aircrack-ng once installed in VMware Workstation.
What is Kali Linux?
Kali Linux is a popular open-source Linux distribution designed for penetration testing, ethical hacking, and other cybersecurity-related tasks. It is based on Debian and comes preloaded with various security tools and utilities that enable cybersecurity professionals to assess vulnerabilities, perform network analysis, and conduct various security audits.
With its extensive toolset and capabilities, Kali Linux has become an essential platform for beginners and experts in information security.
What is Airmon-ng?
Airmon-ng is a powerful command-line tool part of the Aircrack-ng suite, a collection of tools for assessing wireless network security.
Airmon-ng enables users to configure their wireless adapters into monitor mode, which allows them to capture raw 802.11 frames, eavesdrop on wireless networks, and collect valuable data for further analysis.
By leveraging Airmon-ng, cybersecurity professionals can gain valuable insights into the security posture of wireless networks and identify potential vulnerabilities and weak points.
Is Airmon-ng Pre-installed In Kali Linux?
Airmon-ng comes pre-installed in Kali Linux as part of the Aircrack-ng suite. This integration allows users to access and utilize Airmon-ng and other Aircrack-ng tools immediately, streamlining the process of conducting wireless network security assessments and penetration testing tasks.
Install Kali Linux on VMware VM
You can also install Kali Linux on Virtual Box. However, in this tutorial, we will be Installing Kali Linux on a VMware virtual machine, and download the Kali Linux ISO file from the official Kali Linux website.
Next, open VMware Workstation or Player and click “Create a New Virtual Machine.” Select the option to install the operating system later and choose “Linux” as the guest operating system, with Debian as the version.
Allocate sufficient resources such as RAM and disk space, and then create a new virtual disk. After configuring the virtual machine settings, connect the Kali Linux ISO file as a virtual CD/DVD drive, and start the virtual machine to begin the graphical install process.
Download Kali Linux for your virtualization technology.
Extract the files. In this case, I am extracting VMware Workstation files.
Boot Kali Linux in VMware Workstation.
Start using Docker-Kali Image
Using Docker images can be a convenient way to deploy Kali Linux and leverage its tools without installing the full operating system. To get started, ensure Docker is installed on your host machine, and then pull the official Kali Linux Docker image by running the following command:
docker pull kalilinux/kaliNext, create and run a new container with the Kali Linux image:
docker run -it --name kali-container kalilinux/kaliNow install tools into your Kali Linux
Once Kali Linux is installed on a virtual machine or running as a Docker container, you may need to install additional tools that are not included by default. You can use the “apt-get” package manager to update the package list and install the desired tools. For instance, to install the Metasploit framework, run the following commands:
sudo apt-get update sudo apt-get install metasploit-frameworkHow To Install Aircrack-ng
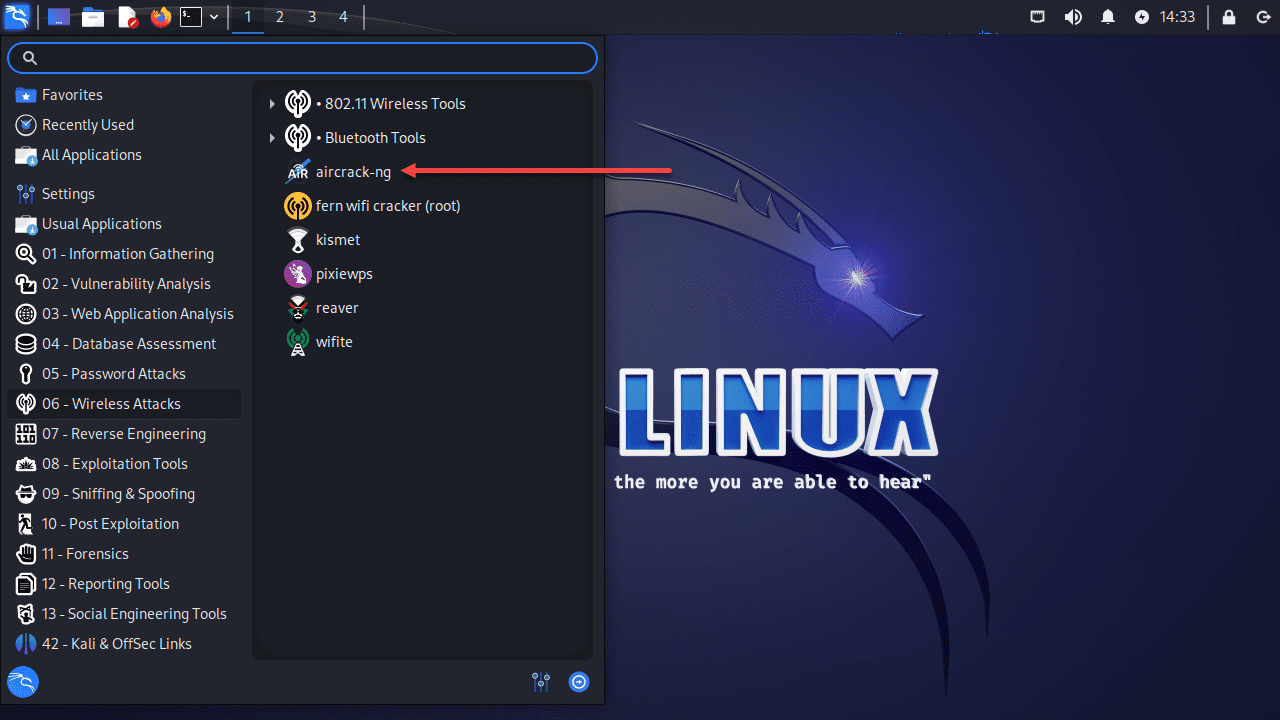
Aircrack-ng, as mentioned earlier, comes pre-installed with Kali Linux. However, in case you need to install or reinstall it, you can use the following commands:
sudo apt-get update sudo apt-get install aircrack-ngConnect a Wireless card to Kali Linux Virtual Machine (VMware Player)
To use a wireless adapter with your Kali Linux virtual machine in VMware Player, you need to ensure that your host machine recognizes the adapter and that the virtual machine settings allow USB connections.
First, plug your USB Wi-Fi adapter into your host machine’s USB port. Then, in VMware Player, select the Kali Linux virtual machine and open its settings.
Under the “USB Controller” settings, ensure the USB compatibility is set to the appropriate version (usually USB 2.0 or 3.0). Click “OK” to save the settings.
Next, with the Kali Linux virtual machine running, go to the “VM” menu, and under “Removable Devices,” find your Wi-Fi adapter. Click “Connect (Disconnect from host)” to attach the adapter to the virtual machine. Once connected, Kali Linux should recognize and enable the adapter in the virtual environment.
You can then start working with the network adapter settings in the VM as you run Kali Linux.
Best WiFi Adapters for Hacking (With Monitor Mode)
When selecting Wi-Fi network adapters for hacking or penetration testing, choosing one that supports both monitor mode and packet injection is crucial. You will likely not want to use the internal wifi card for the Wifi network. Rather, some of the best Wi-Fi adapters for these purposes include:
Alfa AWUS036NHA
TP-Link TL-WN722N
Panda PAU09
Alfa AWUS036ACH
Alfa AWUS1900
These adapters have been proven to work well with Kali Linux and the Aircrack-ng suite, providing reliable performance for ethical hacking tasks.
Installing VMware Tools on Kali Linux VMware VM
VMware Tools is a set of utilities that enhance the performance and usability of virtual machines, including features such as improved screen resolution and seamless integration with the host machine. To install VMware Tools on your Kali Linux virtual machine, run the following commands:
sudo apt-get update sudo apt-get install open-vm-tools-desktop fuseAfter the installation is complete, reboot the virtual machine for the changes to take effect.
Configuring Screen Resolution
After installing VMware Tools, you may need to configure the screen resolution for your Kali Linux virtual machine. To do this, open the “Terminal” in Kali Linux and run the following command:
sudo xrandr -s 1920x1080Replace “1920×1080” with your desired screen resolution. The changes should take effect immediately.
Vmware Player: How To Use A USB Wifi Adapter
To use a USB Wi-Fi adapter with your Kali Linux virtual machine in VMware Player, follow the steps mentioned in the “Connect a Wireless Adapter to Kali Linux Virtual Machine (VMware Player)” section.
Ensure the host machine recognizes the adapter and enables USB connections in the virtual machine settings. Once connected, Kali Linux should recognize and enable the adapter in the virtual environment.
How to Connect a WI-FI Adapter to a VMware VM to Be Used by Kali Linux?
To connect a Wi-Fi adapter to a VMware virtual machine for use with Kali Linux, follow the same steps as previously mentioned in the “Connect a Wireless Adapter to Kali Linux Virtual Machine (VMware Player)” section.
Attach the Wi-Fi adapter to the host machine’s USB port, configure the virtual machine settings to enable USB connections, and then connect the adapter to the virtual machine through the VMware software.
Problems With Built-in Wireless Cards
Built-in, internal wireless cards on host machines often pose challenges for virtual Kali Linux machines, as they may not support monitor mode or packet injection. This limitation makes it difficult to perform effective wireless network assessments and penetration testing tasks.
To overcome this issue, it is recommended using an external USB Wi-Fi adapter that is compatible with Kali Linux and supports both monitor mode and packet injection, as discussed in the “Best WiFi Adapters for Hacking (With Monitor Mode)” section.
How To Enable Wifi Adapter In Kali Linux In Vmware
To enable a Wi-Fi adapter in Kali Linux running in a VMware virtual machine, follow these steps:
Ensure the adapter is connected to the host machine’s USB port and recognized by the host system.
Configure the virtual machine settings in VMware to allow USB connections, as described in the “Connect a Wireless Adapter to Kali Linux Virtual Machine (VMware Player)” section.
With the Kali Linux virtual machine running, connect the Wi-Fi adapter to the virtual machine using the VMware software.
In Kali Linux, open the terminal and run the following command to enable the Wi-Fi adapter:
sudo ifconfig wlan0 upVerify that the Wi-Fi adapter is enabled and functioning by running:
sudo iwconfig
The Wi-Fi adapter should now be enabled and ready for use within your Kali Linux virtual machine.
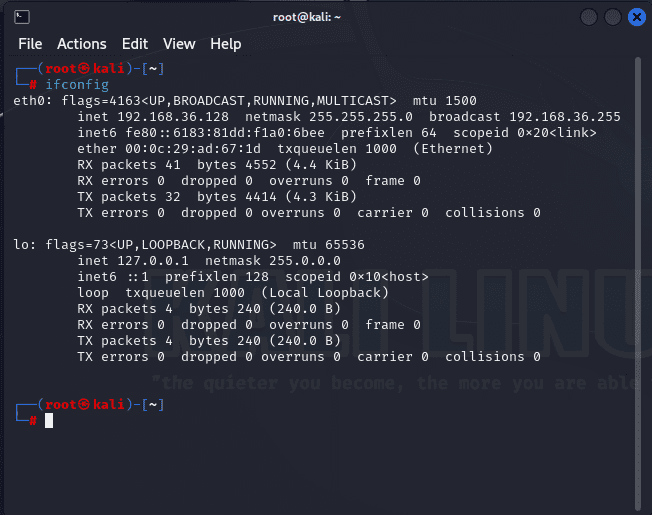
You can use ifconfig, as shown below. If you have added your wireless adapter, it should display the IP address here.
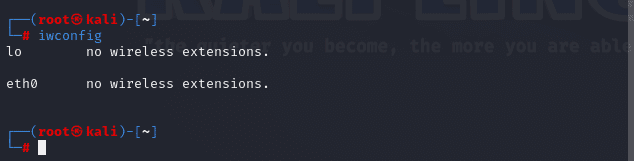
If you have no wireless connections, you will see the following with an iwconfig output.
How To Use Aircrack-ng And Airodump-ng In Kali Linux To Crack Wi-fi Passwords
Aircrack-ng and Airodump-ng are essential tools within the Aircrack-ng suite, allowing users to capture Wi-Fi traffic and crack Wi-Fi encryption keys. Here is a brief overview of how to use these tools in Kali Linux to crack Wi-Fi passwords:
Put your Wi-Fi adapter into monitor mode using Airmon-ng:
sudo airmon-ng start wlan0Identify the target wireless network by running Airodump-ng:
sudo airodump-ng wlan0monCapture the handshake between the access point and a client by running Airodump-ng with the target network’s BSSID and channel:
sudo airodump-ng -c [channel] --bssid [BSSID] -w [output-file] wlan0monWait for a handshake to be captured, indicated by the “WPA handshake” message in the Airodump-ng output.
Use Aircrack-ng to crack the captured handshake and retrieve the Wi-Fi password:
sudo aircrack-ng -a2 -b [BSSID] -w [wordlist] [output-file-01.cap]Replace [wordlist] with the path to a wordlist file containing potential passwords.
By following these steps, you can use Aircrack-ng and Airodump-ng in Kali Linux to crack Wi-Fi passwords and assess the security of wireless networks.
Keep in mind that this process should be used responsibly and only for ethical hacking purposes, such as testing the security of your own network or with explicit permission from the network owner.
How to Keep Your Wireless Network Safe
To ensure the security of your wireless network, follow these best practices:
Use strong encryption: Enable WPA3 encryption on your Wi-Fi router if available. If WPA3 is not supported, use WPA2 instead of the outdated and insecure WEP or WPA.
Set a strong password: Use a complex and unique password for your Wi-Fi network to prevent unauthorized access. It should be at least 12 characters long, including uppercase and lowercase letters, numbers, and special symbols.
Change the default SSID: Change the default Service Set Identifier (SSID) or network name to something unique to make it harder for attackers to identify your router model and exploit known vulnerabilities.
Disable WPS: Wi-Fi Protected Setup (WPS) can be vulnerable to brute-force attacks. Disable this feature on your router to improve security.
Enable router firewall: Ensure that the built-in firewall on your router is enabled and properly configured to block malicious traffic.
Keep router firmware updated: Regularly update your router’s firmware to protect against known security vulnerabilities and ensure optimal performance.
Disable remote management: Turn off your router’s remote management features to prevent unauthorized internet access.
Use MAC address filtering: Limit access to your Wi-Fi network by allowing only specific devices based on their MAC addresses. However, this should not be solely relied upon, as MAC addresses can be spoofed.
Create a separate guest network: Set up a separate guest Wi-Fi network with a different visitor password. This helps to isolate your main network from potential security risks.
Turn off the network when not in use: If you don’t need your Wi-Fi network for extended periods, turn it off to reduce the risk of unauthorized access.
By implementing these security measures, you can significantly improve the safety of your wireless network and protect your data from potential cyber threats.
Airmon-ng VMware Kali FAQs
In this section, we will address some frequently asked questions about using Airmon-ng, VMware, and Kali Linux for Wi-Fi network security assessments and penetration testing.
Q: Can I use the built-in wireless card of my laptop with Kali Linux in a VMware virtual machine?
A: While it is technically possible to use the built-in wireless card with Kali Linux in a VMware virtual machine, it is generally not recommended due to compatibility issues and limitations in functionality.
An external USB Wi-Fi adapter that supports monitor mode and packet injection is the preferred option for optimal performance and compatibility.
Q: How do I install VMware Tools on my Kali Linux virtual machine?
A: To install VMware Tools on your Kali Linux virtual machine, follow these steps:
Update your Kali Linux system with the following command:
sudo apt-get updateInstall the open-vm-tools package:
sudo apt-get install -y open-vm-toolsReboot your virtual machine for the changes to take effect.
Q: Why do I need monitor mode and packet injection support for my Wi-Fi adapter in Kali Linux?
A: Monitor mode allows your Wi-Fi adapter to capture all Wi-Fi traffic in the air, regardless of the network it is connected to. Packet injection enables your adapter to inject custom packets into a network, which is useful for exploiting vulnerabilities and testing the security of Wi-Fi networks.
Both features are essential for effective penetration testing and network security assessments.
Q: Can I use VirtualBox instead of VMware for running Kali Linux?
A: Yes, you can use VirtualBox as an alternative to VMware for running Kali Linux. The process of setting up Kali Linux in VirtualBox is similar to that in VMware. However, there might be slight differences in configuration options and performance.
Q: Is using Kali Linux and its tools to crack Wi-Fi passwords legal?
A: It is only legal to use Kali Linux and its tools to crack Wi-Fi passwords for ethical hacking purposes, such as testing the security of your own network or with explicit permission from the network owner. Unauthorized access to networks and systems without permission is illegal and unethical.
Wrapping up
There are many great features and capabilities found in the Kali Linux distribution allowing cybersecurity specialists the opportunity to have quick and easy access to cybersecurity tools.
Testing out the security of wireless networks is an extremely important part of the overall cybersecurity strategy.
Using the airmon-ng and aircrack ng tools in Kali Linux is a great way to test the strength of your wireless network and protocols.
You can easily install Kali Linux in VMware Workstation and use an affordable USB network adapter to have easy access to wireless networks inside your VMware Workstation VM.
You can pass the USB network adapter through to the virtual machine and allow it to use the wireless adapter.
It isn’t recommended to use built-in internal network connections as these often have issues being passed through to the virtual machine. Hopefully this airmon-ng VMware Kali walkthrough will help with getting started with these really great security tools.






0 Comments