
I really like to geek out on free and open-source solutions that allow you to do amazing things, both in the home lab and in production environments. One of my favorite parts of the home lab is the network. If you are looking for an open-source firewall that can do some amazing things, pfSense is a great solution with enterprise features, including the ability to configure VPN connections. Wireguard is another excellent network technology that provides one of the fastest and most performant VPN protocols today. Let’s see how to install and configure Wireguard on pfSense and the process involved.
What is pfSense
pfSense, an open-source firewall/router software distribution based on FreeBSD, is renowned for its reliability and feature-rich nature. It offers unrivaled flexibility and control and is perfect for securing a network and managing traffic. Running on commodity hardware provides cost-efficient network security that rivals most commercial firewalls.
Learn more about pfSense here: pfSense® – World’s Most Trusted Open Source Firewall.
What is Wireguard
WireGuard is an innovative VPN protocol striving for simplicity and efficacy. With its streamlined codebase, it excels in performance, reliability, and ease of deployment, offering robust encryption standards.
When compared to IPSec or OpenVPN, WireGuard establishes connections faster, maintains them seamlessly and consumes less processing power – all while ensuring top-notch security.

Learn more about Wireguard here: WireGuard: fast, modern, secure VPN tunnel.
The Power Duo: pfSense and WireGuard
The marriage of pfSense and WireGuard brings together a robust firewall/router with an efficient VPN protocol. This combo ensures optimized network security, speed, and stability. It empowers users to create secure VPN tunnels, effortlessly manage network traffic, and uphold stringent security practices – all on one platform.
Setting Up WireGuard on pfSense: A Comprehensive Guide
Installing the WireGuard Package
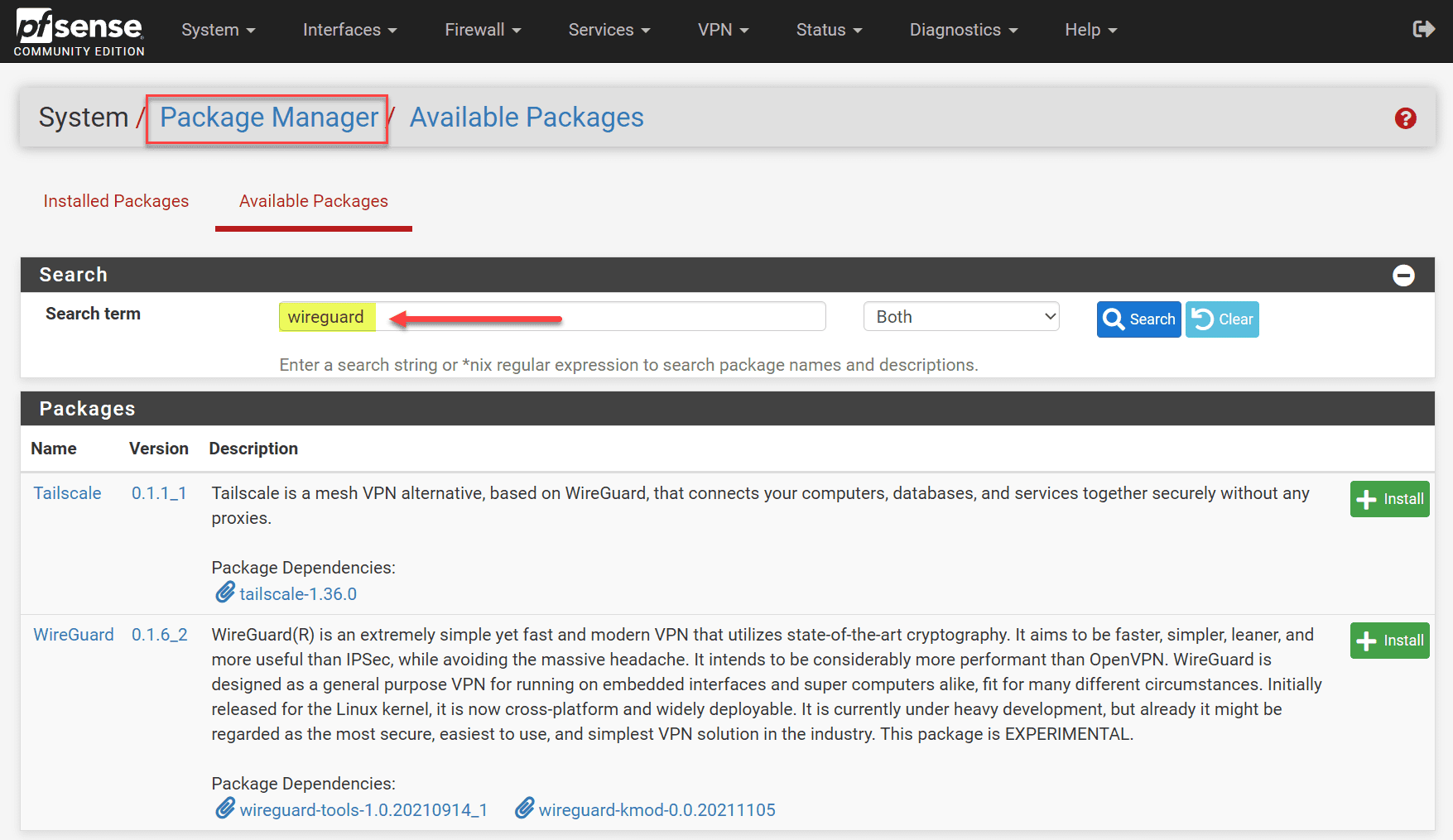
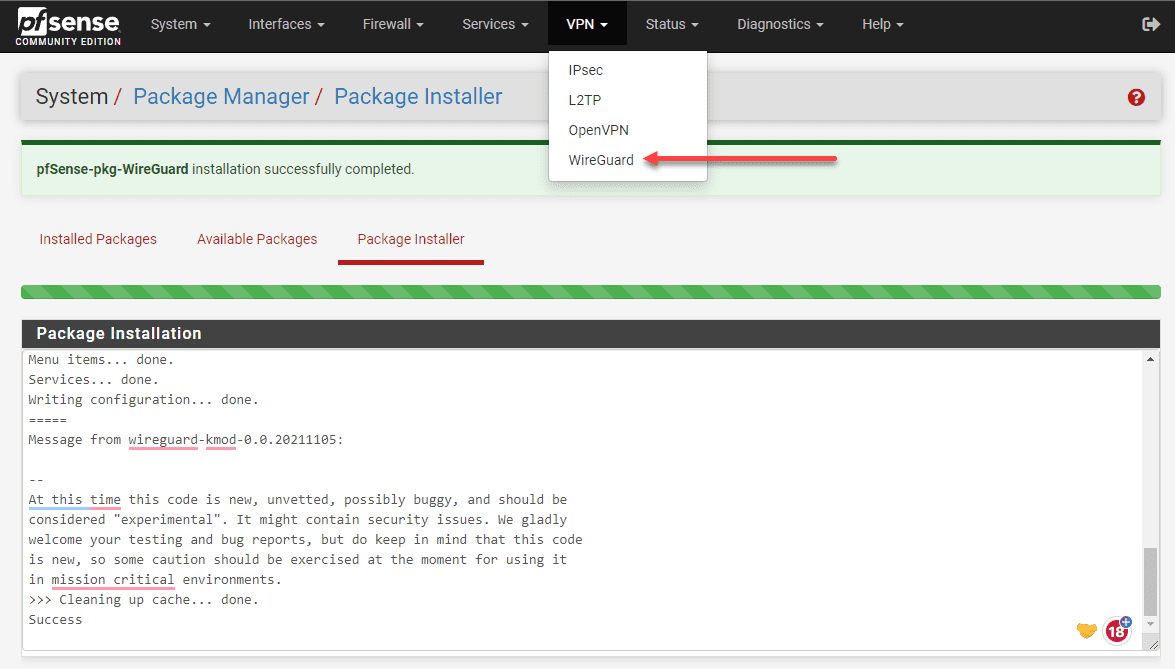
Kick-start the process by installing the WireGuard package. Navigate to the package manager within the pfSense interface, locate WireGuard within the available packages, and click install. Make sure to check the ‘Enable WireGuard’ box after installation.
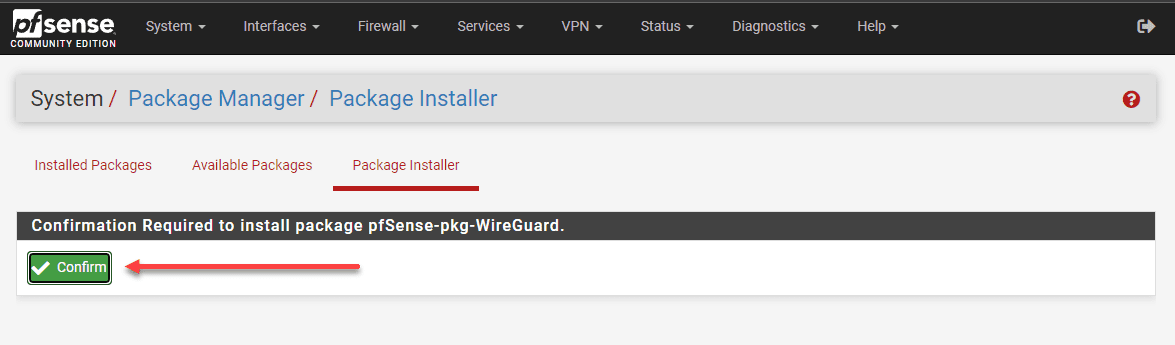
Next, confirm the installation of the package on your pfSense instance.
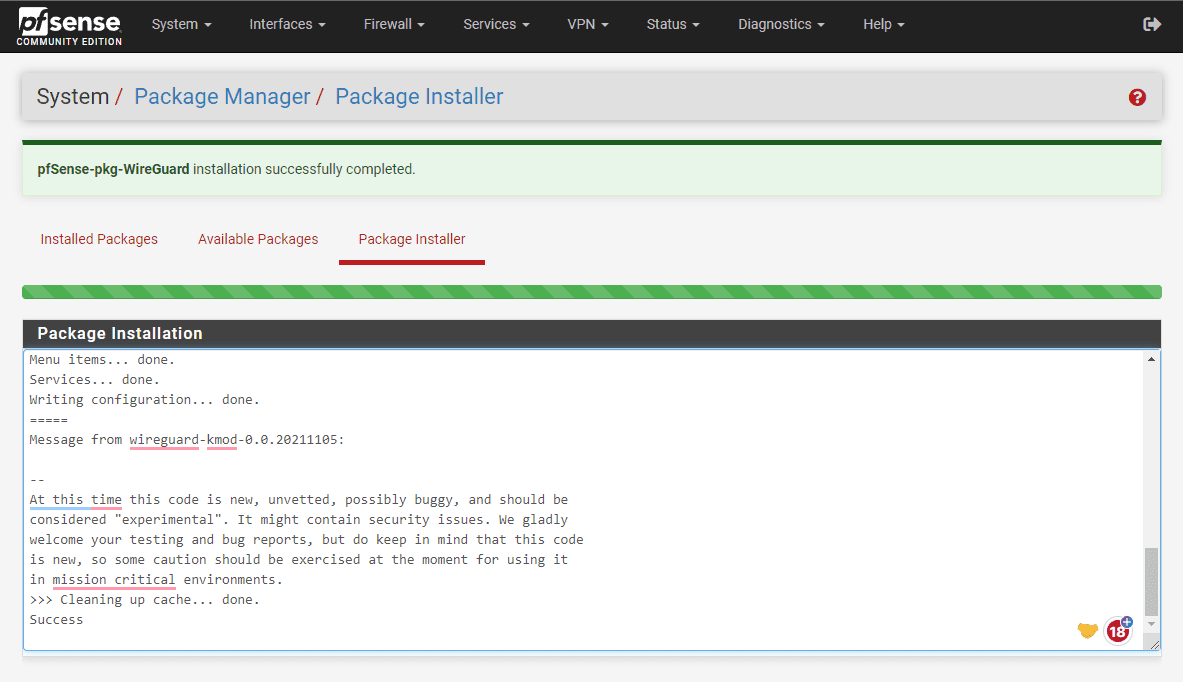
You will see the package installer status.
Now, you will see the Wireguard option listed under the VPN menu.
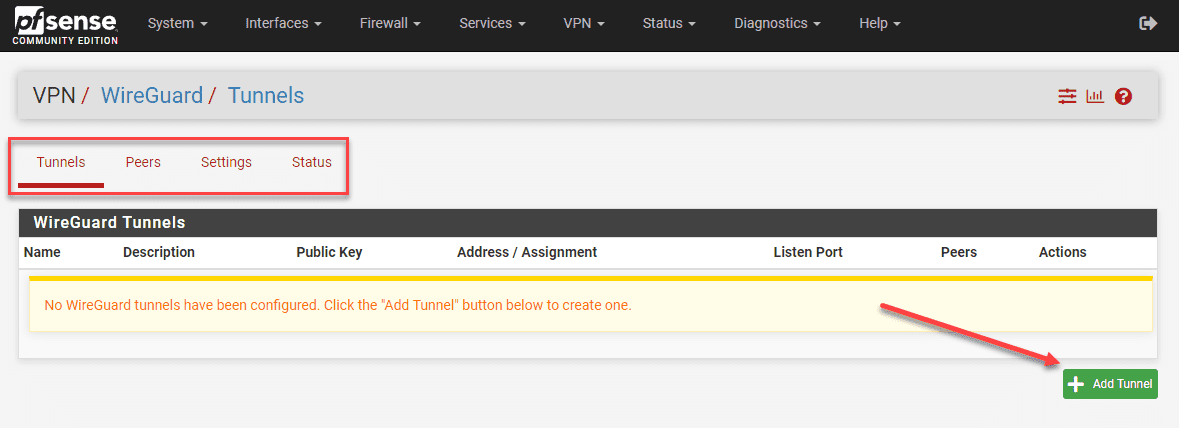
Establishing the WireGuard Tunnel
Let’s establish your WireGuard tunnel. Under WireGuard -> Tunnel, input your tunnel configuration, including the private key, listen port, and interface addresses. Check the tunnel settings and click save.
Below we are clicking the Add tunnel button.
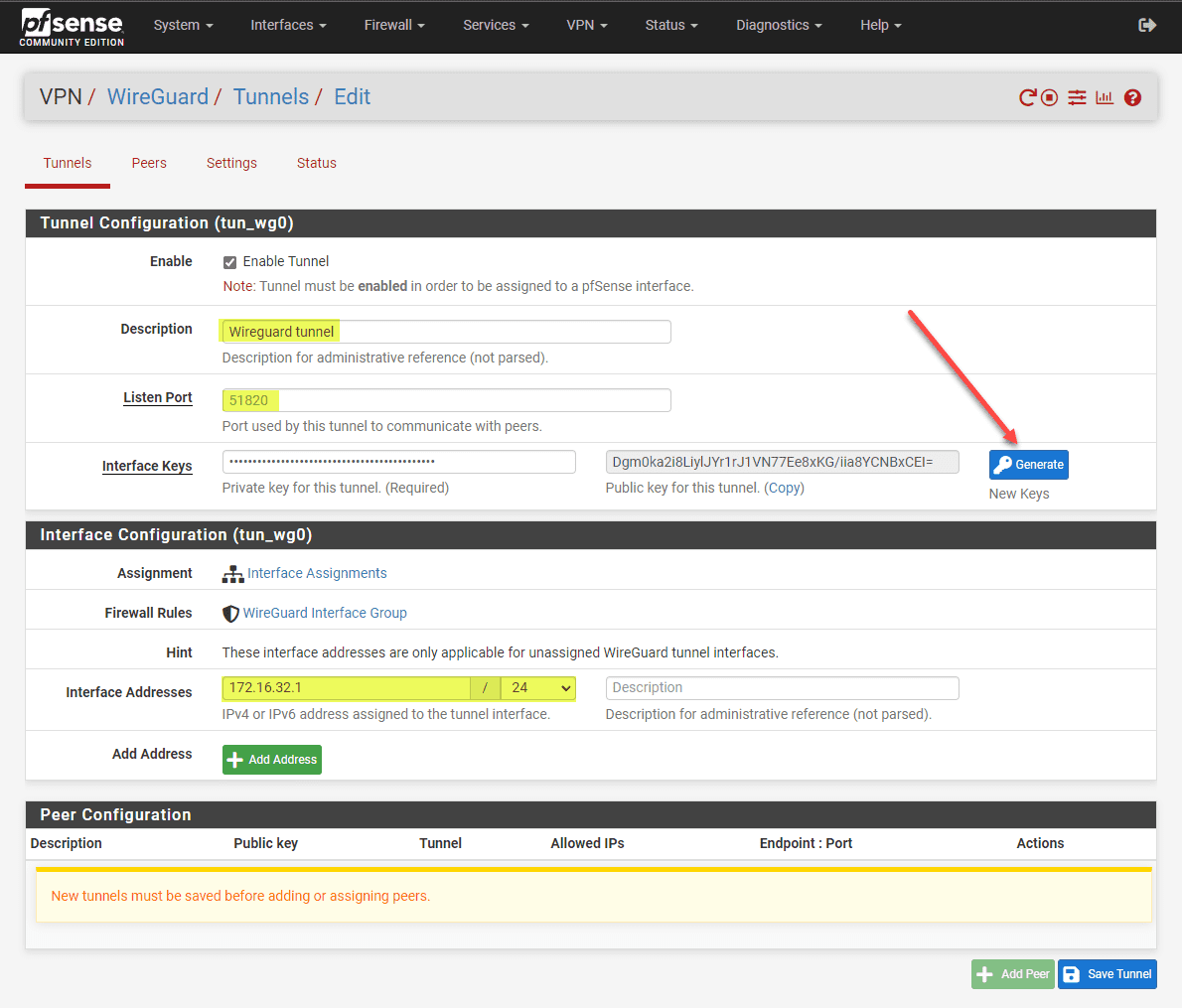
Here you will configure a listen port, generate the interface keys, and assigned an interface address.
Generate the keypair that will be used for establishing connections securely.
Configuring the WireGuard Interface
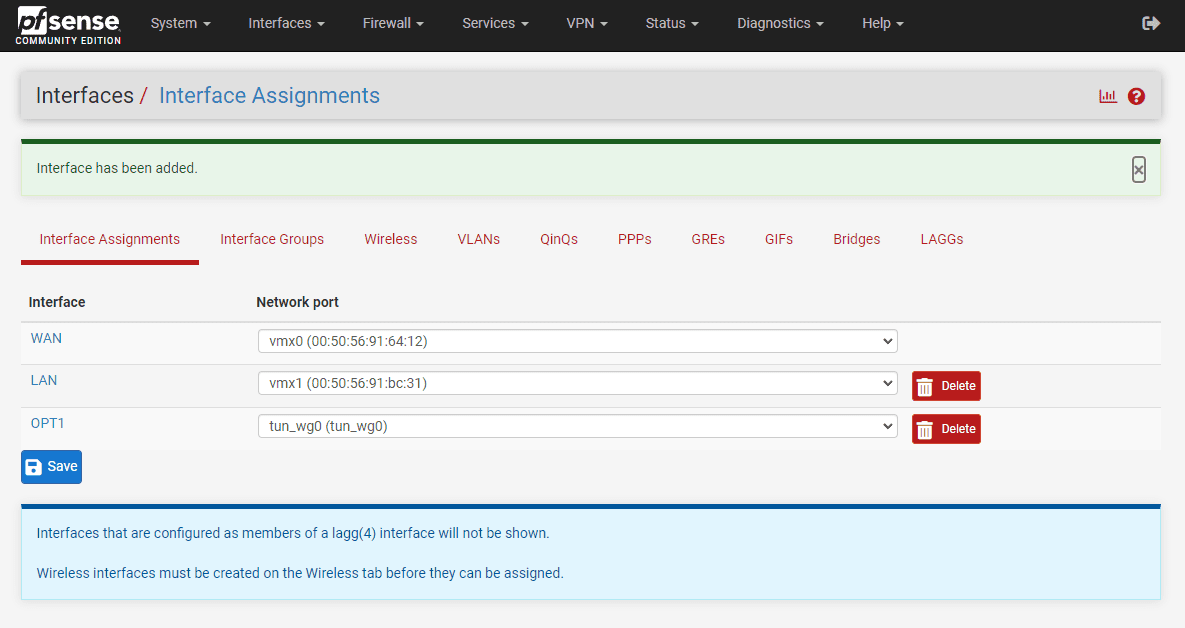
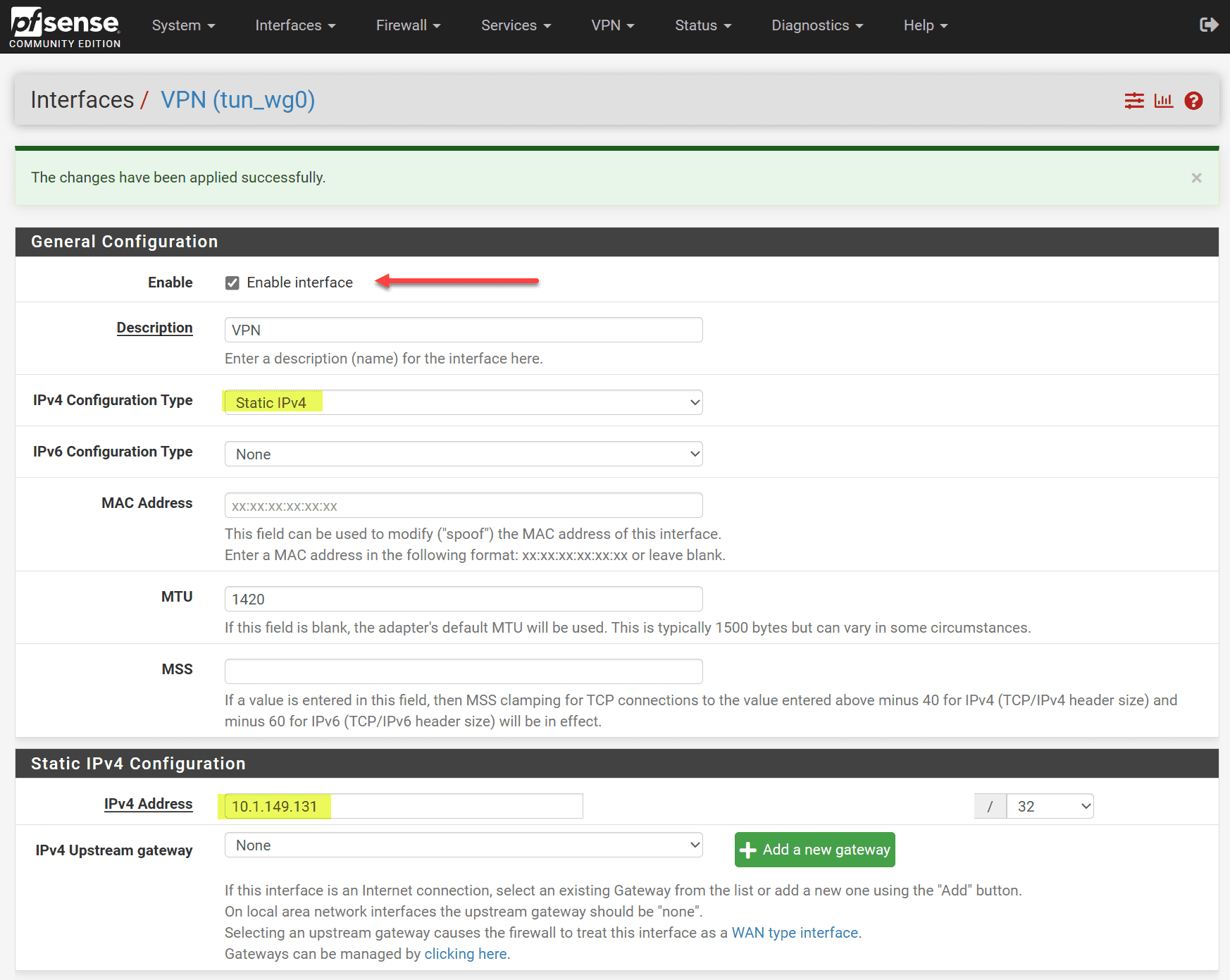
You can also create a new interface for wireguard if you choose the Interface Assignment. After adding the tunnel, the Wireguard will create the OPT interface, which may be numbered differently depending on your existing interfaces. Including IP address and listen port. Remember to generate a unique public and private key pair for secure communication.
If you configure your OPT interface, you have the option to Enable interface. Also, set the IPv4 or IPv6 configuration type. Set your IP address configuration.
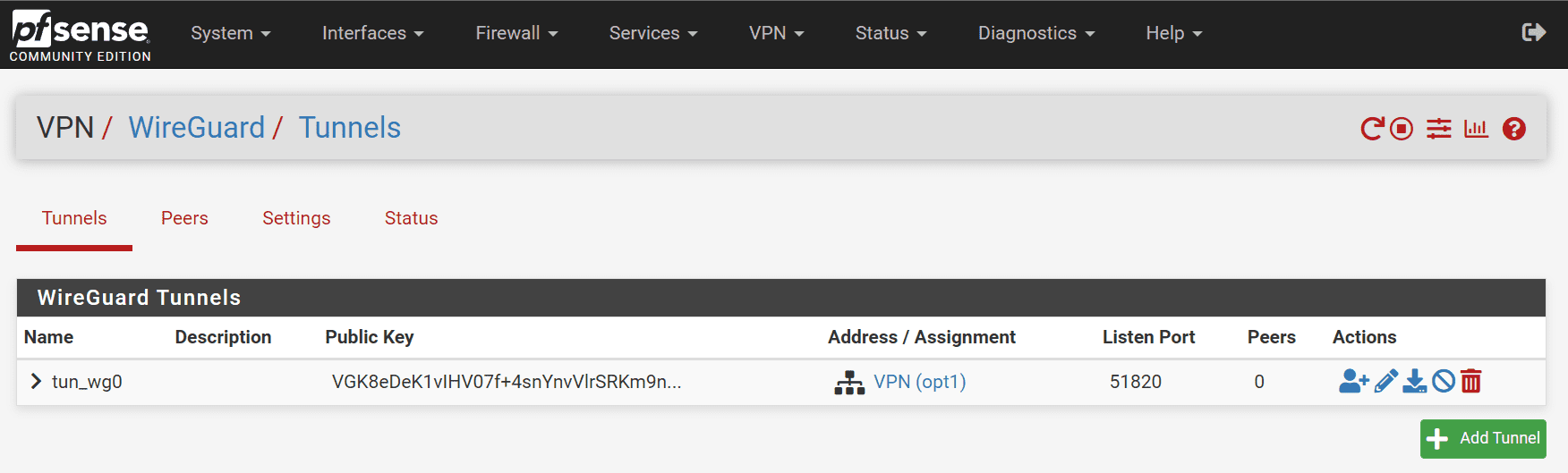
You can see the Address/Assignment is configured for the Wireguard tunnel.
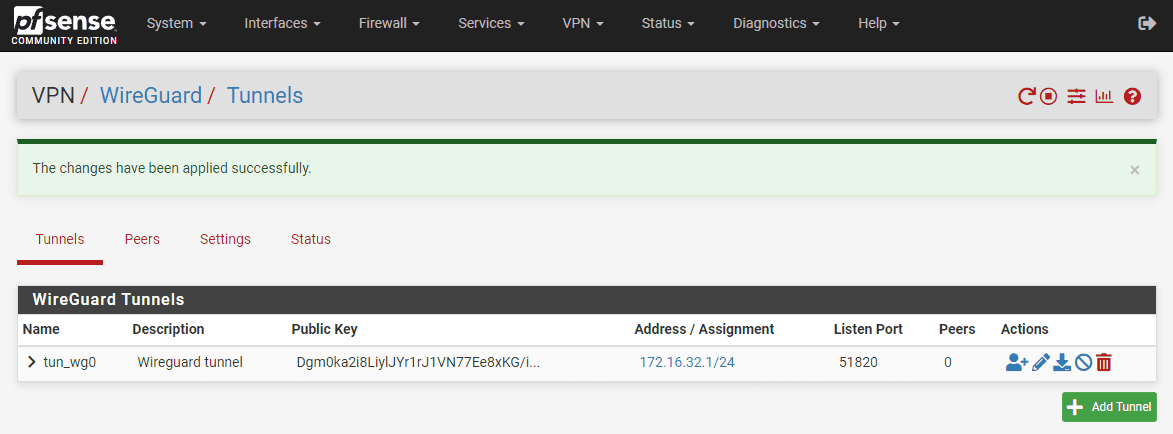
If you just use an address and don’t create a new interface (which is perfectly fine), you will see the tunnel created and it looks like the following.
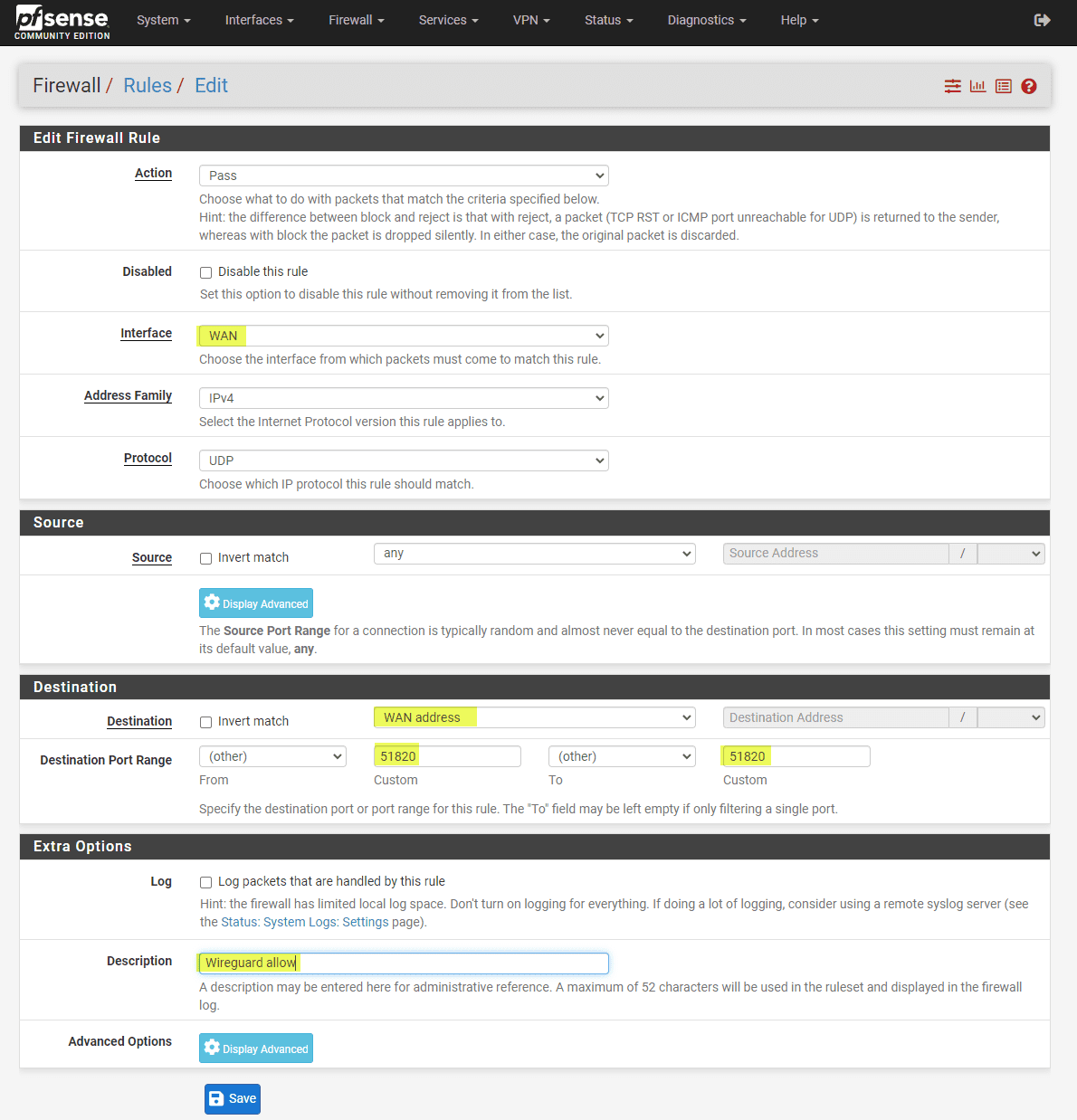
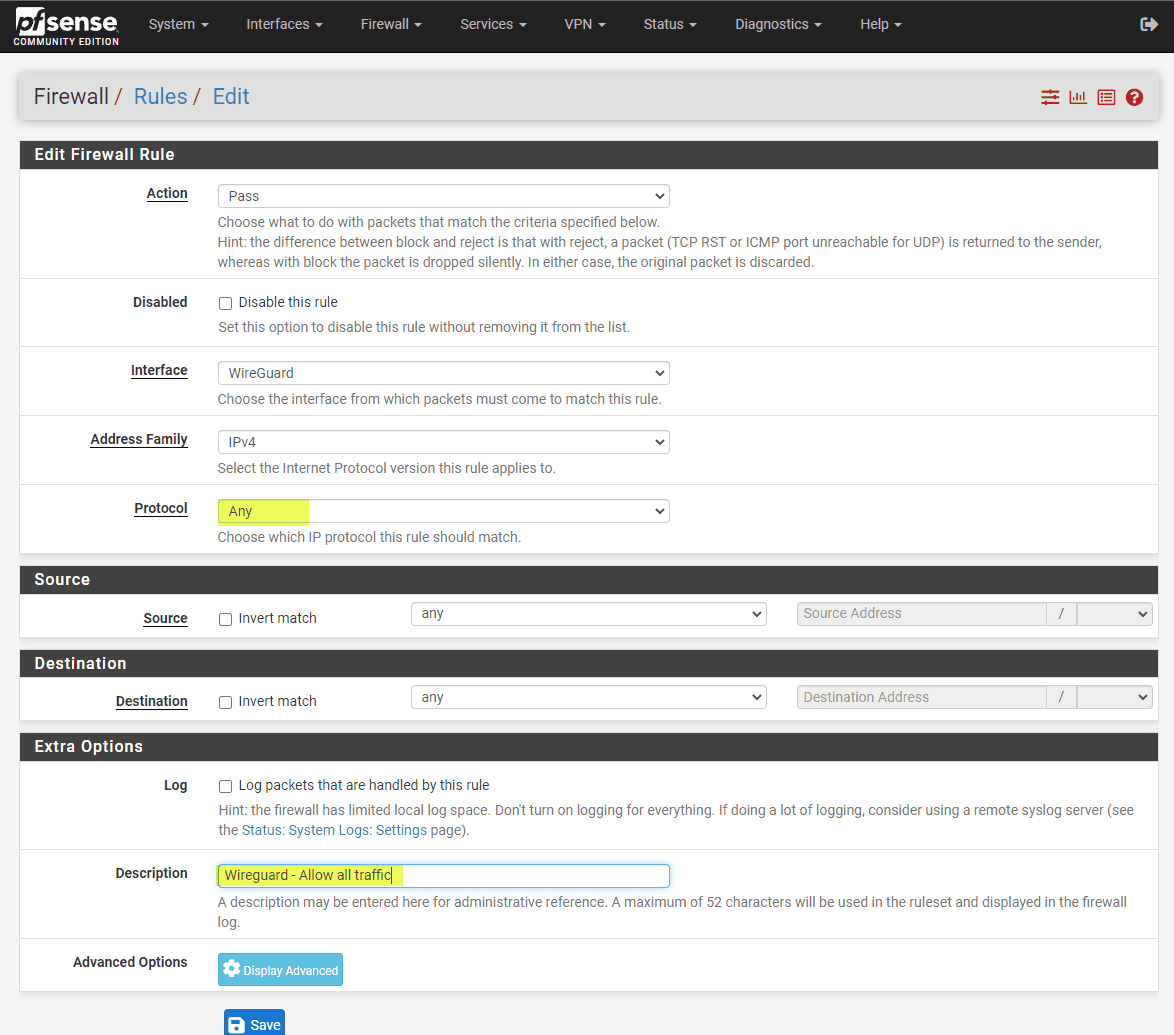
Setting Up Firewall Rules
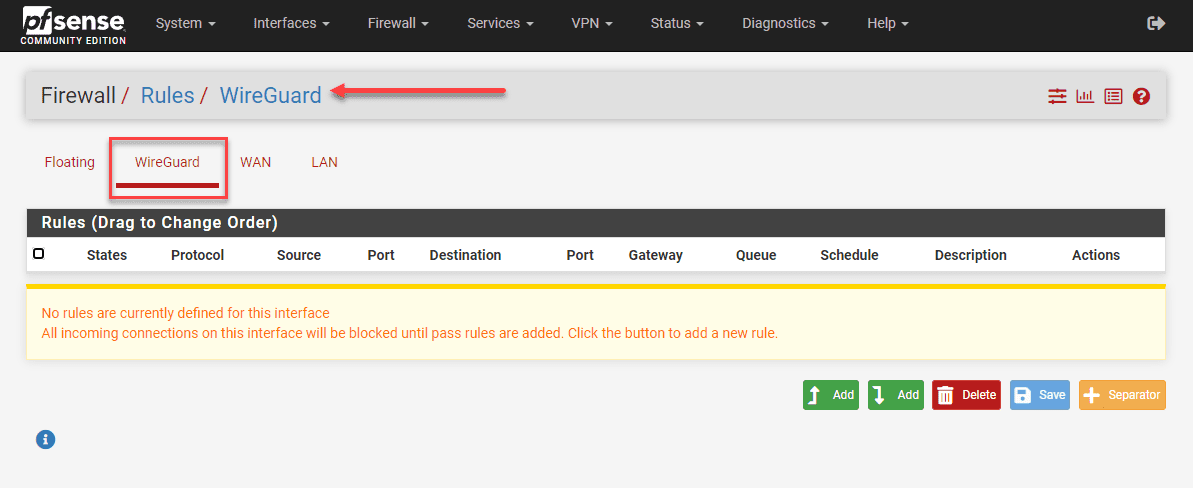
Navigate to Firewall -> Rules -> WireGuard. Setting up appropriate firewall rules to govern the traffic flow through your WireGuard tunnel is crucial. Pay extra attention to rules regarding the local network (LAN net) and the allowed IPs. After finalizing the rules, click save. Of course you can add any firewall rule needed to filter traffic with VPN or other connections.
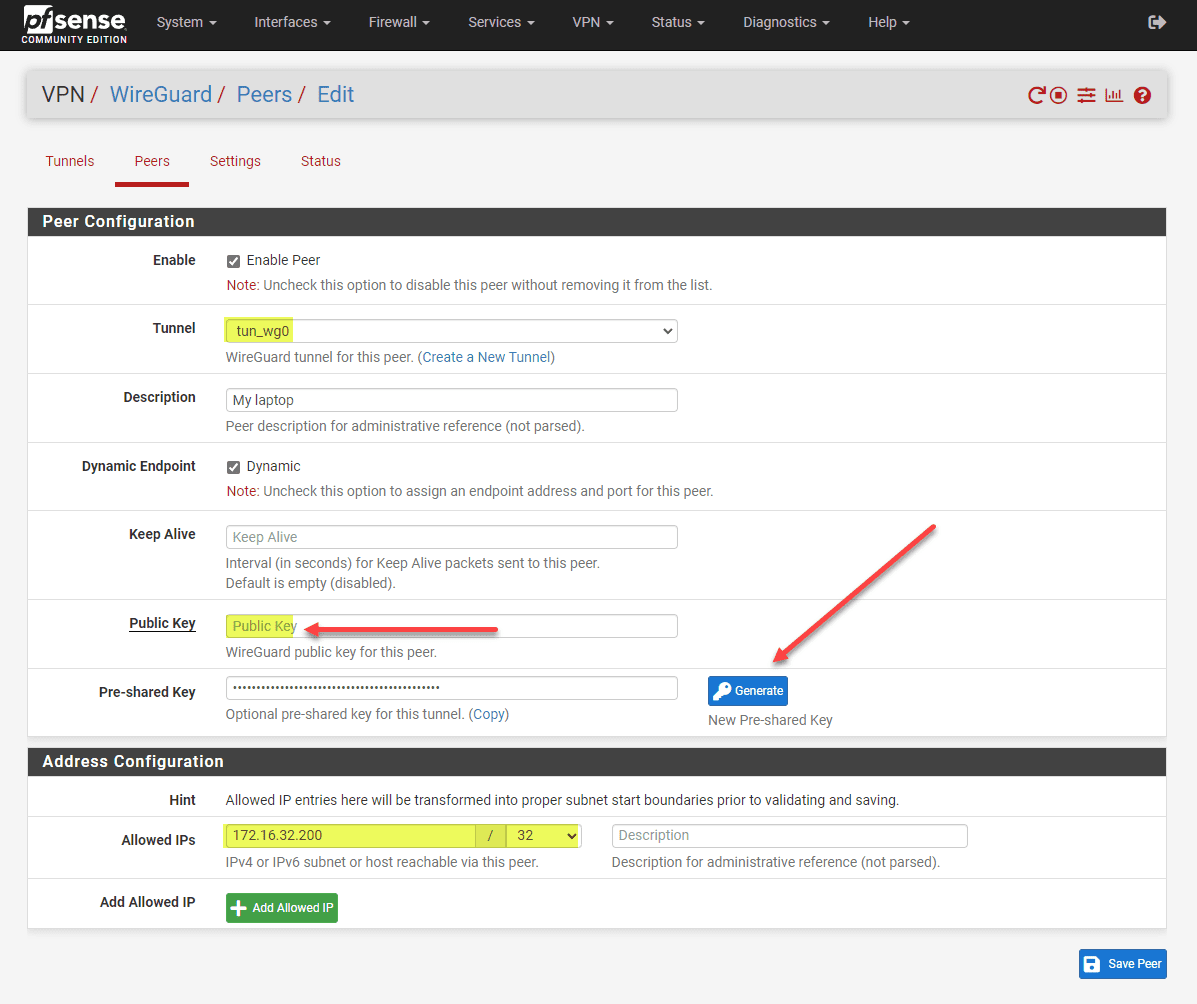
Peer Configuration: Keys and Endpoints
Peer configuration is a vital step in establishing a secure VPN connection. For each Wireguard peer (e.g., client device), you need a unique public key and IP address (allowed IPs). Additionally, specify endpoint IP addresses and endpoint port for dynamic endpoint resolution.
You can also increase security with a pre-shared key for the tunnel. If you want to manually enter an IP address, you will need to uncheck the Dynamic Endpoint checkbox.
Make sure to apply all your changes to your Wireguard configuration.
Advanced pfSense WireGuard Settings
Optimizing DNS Servers and Query Forwarding
pfSense allows extensive DNS resolver configuration. You can set up DNS servers, enable forwarding mode for DNS query forwarding, and even override DNS servers if required. Remember, an optimized DNS setting can significantly enhance your network performance.
Adjusting Default and Upstream Gateways
pfSense’s ability to manage multiple gateways stands out. Depending on your network setup, you can adjust your default gateway and upstream gateway settings under System -> Routing. Adding a new gateway or changing an existing one is as easy as a click.
Managing Network Ports and Port Forwarding
In your network settings, you have a plethora of ports at your disposal. pfSense provides the flexibility to manage these network ports efficiently. Additionally, port forwarding can be set up via NAT rules, ensuring optimized network traffic routing.
WireGuard Server vs WireGuard Client on pfSense
Within the WireGuard on pfSense ecosystem, understanding the difference between a server and a client is critical. The WireGuard server, typically your pfSense router, listens for connections from clients. Clients can be any device like your laptop or smartphone, that connect to the server for secure data transmission.
Configuring the WireGuard Client on pfSense
Configure the WireGuard client on your pfSense to establish a successful VPN connection. Navigate to the WireGuard tab on the pfSense interface and add a new peer. Input the client’s public key, set the allowed IPs, and save the peer. Remember to check the ‘Enable WireGuard’ box before you click the ‘Save’ button.
Managing IP Addresses and Subnet Masks on pfSense
The right IP address and subnet mask configuration ensure efficient routing and delivery of IP packets. On pfSense, you can assign static IPv4 addresses for the WireGuard interface. It enables you to retain the same IP address even after a system restart, contributing to a stable VPN connection.
Optimizing the LAN Interface and Local Network Settings
To make the most of your WireGuard on pfSense setup, optimizing LAN interface and local network settings is key. A well-configured LAN interface ensures that all client devices on your local network have secure access to the VPN tunnel. Set up the appropriate firewall rules to allow VPN traffic from your LAN subnet.
Secure Your pfSense Router with Pre-shared Keys
To boost the security of your pfSense router, consider using pre-shared keys along with the standard public and private keys. This provides additional security to your WireGuard VPN connection, making it harder for unauthorized entities to gain access.
IPv4 Configuration in pfSense WireGuard Setup
Setting up the right IPv4 configuration is crucial for your VPN to work correctly. This includes defining the IPv4 tunnel network in your WireGuard interface and setting static IPv4 for your pfSense router. A well-configured IPv4 setup ensures efficient routing of your VPN traffic.
Checking and Monitoring Your WireGuard Setup
Once you’ve configured the WireGuard on pfSense, checking your setup for any inconsistencies is good. Navigate to the WireGuard interface to see the list of peers and their connection status. You can also check the WireGuard service under ‘Status’ -> ‘Services’ to ensure it’s running correctly.
Troubleshooting Common WireGuard and pfSense Issues
Tunnel Configuration and VPN Connection Issues
VPN tunnel configuration issues can be common, but pfSense makes troubleshooting relatively simple. Reviewing the WireGuard interface, tunnel, and peer configurations can help solve most problems. Look for mismatched public or private keys, incorrect IP address assignments, or improper endpoint configurations.
Addressing DNS Server Override and IP Address Problems
If you encounter DNS or IP address issues, navigating to the DNS server settings can be useful. Check if the DNS server override option is enabled and if the IP addresses assigned are correct. Using the ‘Execute Shell Command Box’ in the Diagnostics tab can also provide valuable insights.
FAQs About pfSense and WireGuard
Can WireGuard run on pfSense?
Absolutely! As of version 2.5.0, pfSense supports WireGuard directly. Install the WireGuard package via the package manager, and you can set up and manage WireGuard VPN tunnels directly from the pfSense interface.
Is WireGuard better than traditional VPN protocols?
WireGuard is often praised for its speed, simplicity, and modern cryptographic methods, offering a leaner and more efficient codebase than traditional VPN protocols like IPSec or OpenVPN. However, every VPN protocol has its strengths and use cases, and the “best” choice can depend on specific needs.
How to manage multiple WireGuard tunnels on pfSense?
You can set up and manage multiple WireGuard tunnels via the WireGuard tab in the pfSense interface. Each tunnel requires its configuration, including a unique private key and associated peers.
How secure is a WireGuard VPN on pfSense?
WireGuard utilizes state-of-the-art cryptographic protocols to provide a high level of security. It uses public key cryptography for encryption and identity verification, providing robust security for your VPN tunnels.
Combined with the advanced firewall features of pfSense, this makes for a highly secure solution for enterprise and personal use. Always remember to keep your software up-to-date and follow best security practices like using strong, unique keys for each connection and regularly auditing your security setup.
What is the performance impact of running WireGuard on pfSense?
WireGuard is designed to be lightweight and efficient. Compared to other VPN protocols, WireGuard tends to have a lower impact on system resources, making it a good choice for devices with limited processing power.
However, as with any VPN, running WireGuard on pfSense will incur some overhead due to the processing required for encryption and decryption. The actual impact on performance will depend on factors such as your hardware, network conditions, and overall system load.
Can I use WireGuard with dynamic IP addresses on pfSense?
Yes, WireGuard can handle dynamic IP addresses. This is useful in situations where your ISP does not provide a static IP address, or where peers (clients) may frequently change locations.
The “Endpoint” for a peer in WireGuard is simply the latest IP address and port that the peer has used to send authenticated data from, and can be updated dynamically as needed. Remember to ensure that your firewall and port forwarding rules, if any, are set up to accommodate this.
Wrapping Up: Harnessing the Power of pfSense and WireGuard
Combining the strength of pfSense and WireGuard can provide tremendous advantages in managing network security and performance. It will allow you to create secure ways to remotely connect to critical resources in the home lab and production networks.
With this guide, you can install WireGuard on pfSense, configure the VPN tunnel, and troubleshoot common issues. While the process may seem complex at first glance, the flexibility, control, and security that this combination offers make it worth it.

0 Comments